Covenant C2
The description states: "Covenant is a .NET command and control framework that aims to highlight the attack surface of .NET, make the use of offensive .NET tradecraft easier, and serve as a collaborative command and control platform for red teamers."
I wanted to like this and perhaps there's much to like but when I'm looking at these types of frameworks, I'm interested in how it can help me. There's definitely a red team / blue team component to this and maybe that's where this excels but that's of little interest to me.
This is the first time I've run a dot net application on Linux so that was kind of cool And in general, it's a cool tool but I don't see how it will aid me.
Upon finishing the install, we hit the UI with a browser and we're asked to set a username and password:
I can't remember exactly when I had that deja vu feeling but sooner or later, I felt like this framework was similar to Faction. Faction is another c2 I checked out but it's still in the too early stages although I wanted to like it too.
Anyway, when we get logged in, we see users:
I'm not interested in adding more users, I head over to Listeners:
Admittedly, I got a little confused with Listeners because the instructions indicate that I should (and can) change the URL:
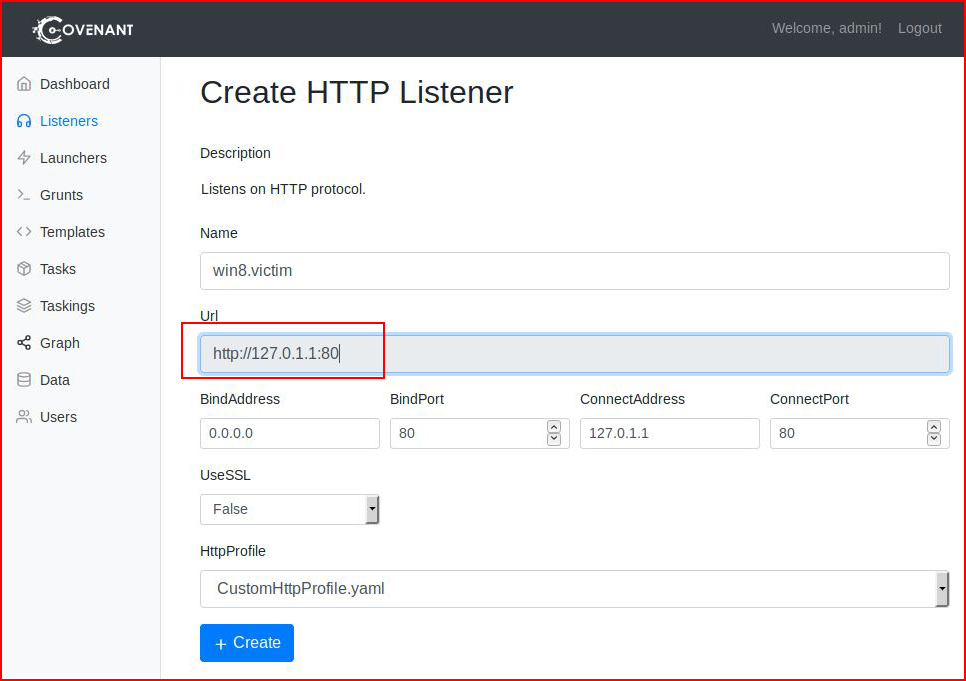
Except you don't change it there, you change it here in the second position, then the first will reflect that change:
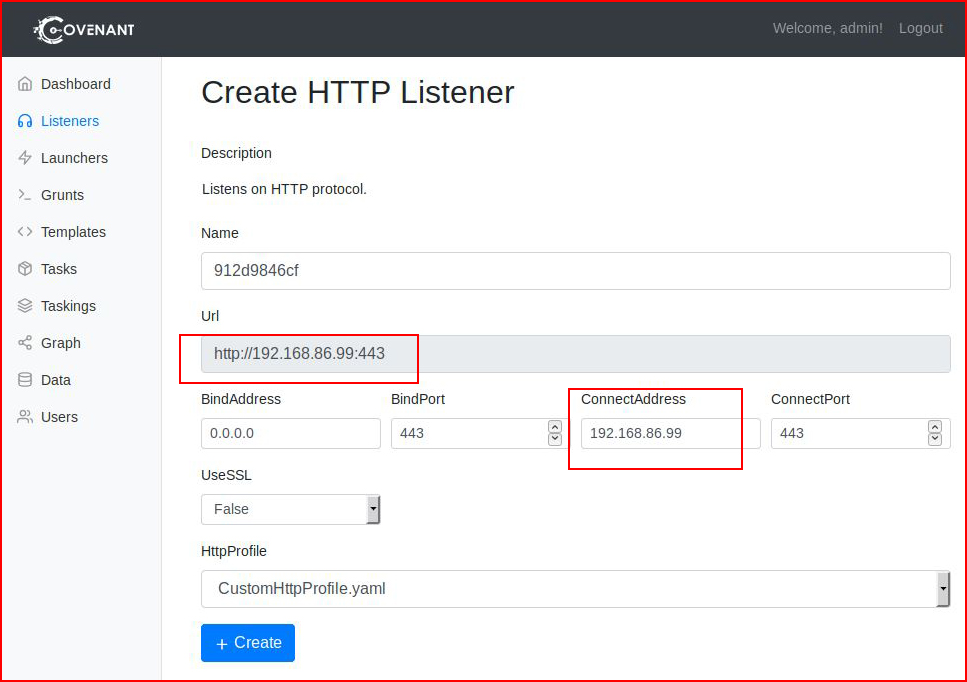
When we hit create, we see our Listener setup and waiting:
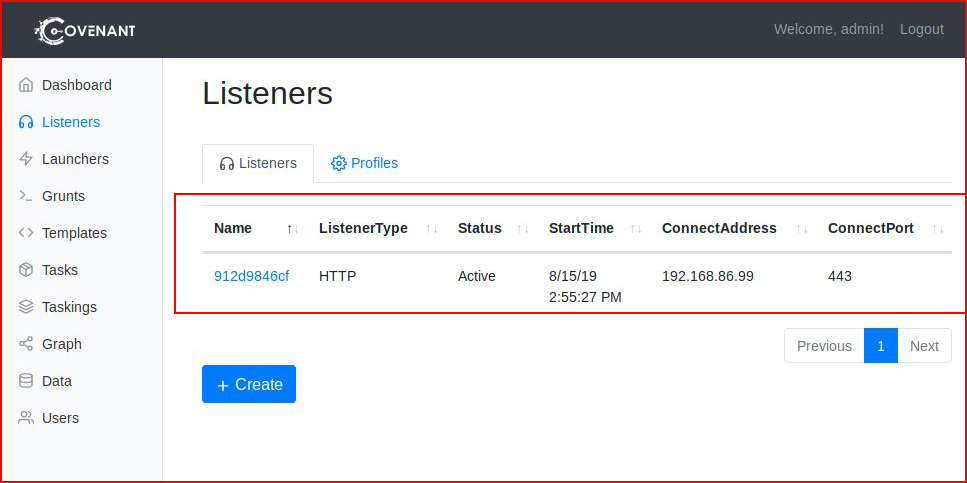
Now we head over to Launchers and we select a Binary:
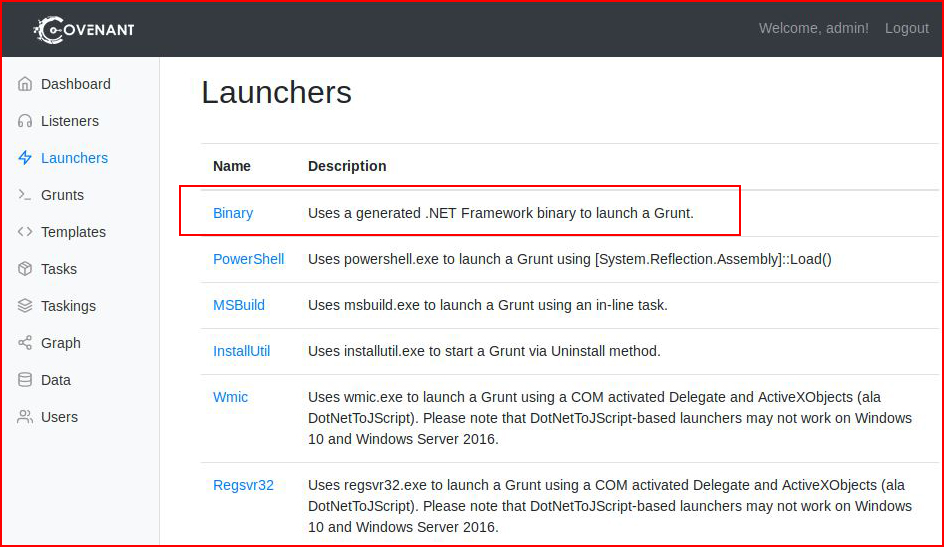
I like the idea of a Killdate and I assume that's a nicety when dealing with red team engagements. Just in case things don't get cleaned up, they are still dead:
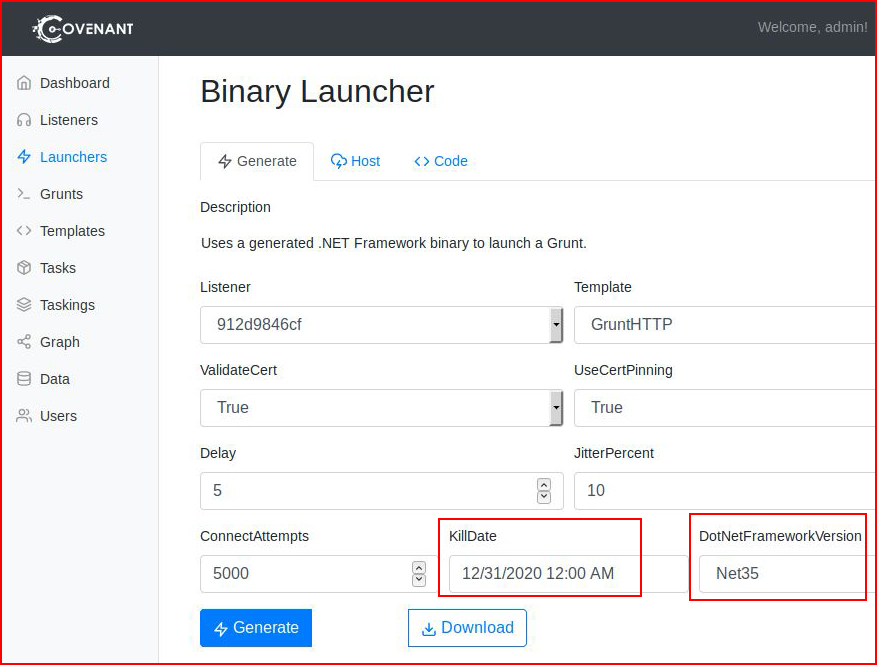
I should also point out that your victim needs to have whichever dot net framework installed. Might want to know that in advance of dropping your implant -- otherwise it requires the download, installation, and relaunching of the implant.
After we generate the implant, we select download:
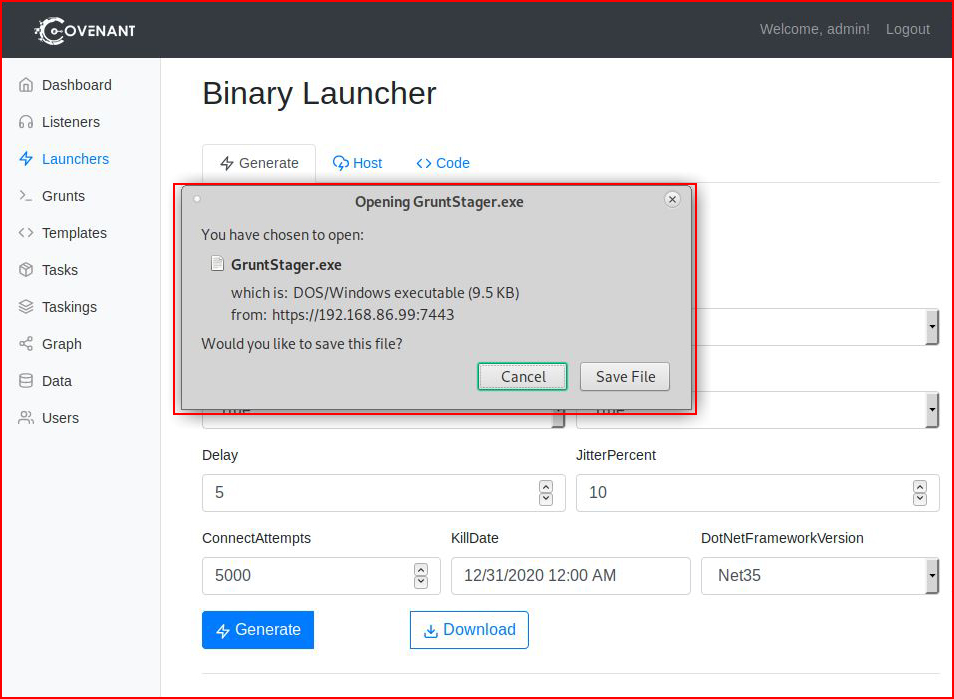
Just for the sake of testing without interference, I have a Windows 8 install without antivirus. I figure I need to make sure it's working before I test it with antivirus.
I download the implant:
I execute it and we get an event in the console:
When we refresh Grunts, we see our connected device:
When we click on the name, we drill down into the info:
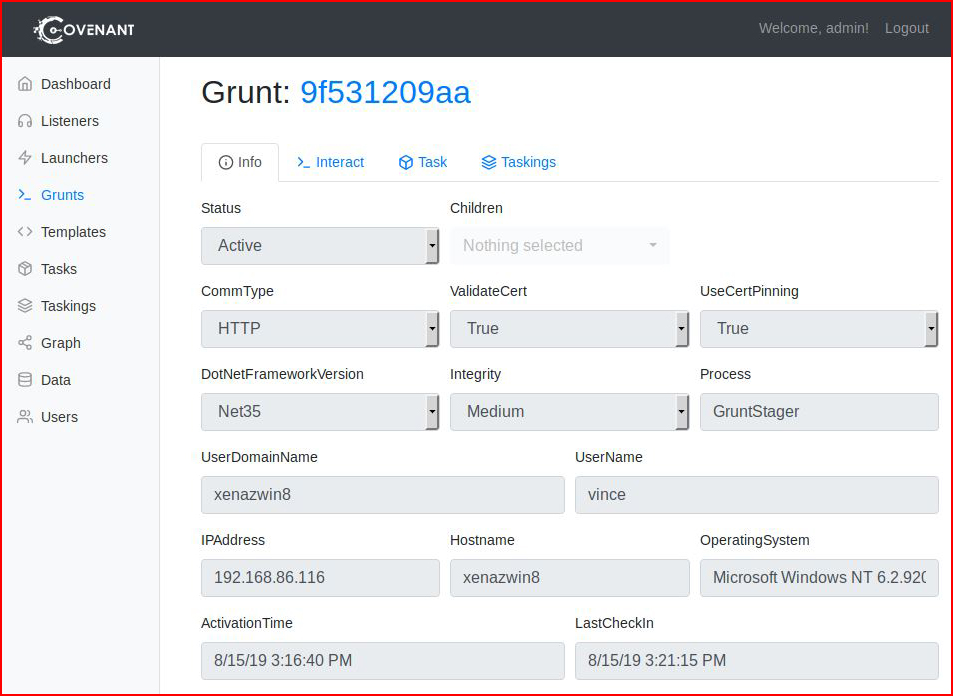
When we select Interact, we get to a console window.
Ah yes, this is where I'm reminded of Faction. Whoami exists but in order to use other command line commands, we have to append "shell".
Whoami:
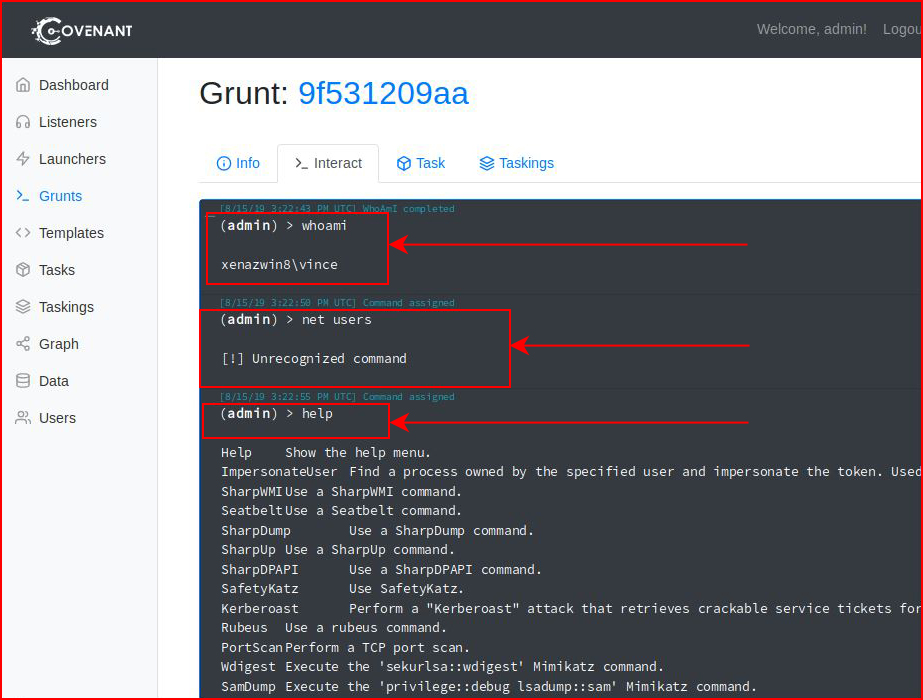
That's when I go hunting for help and I find the "shell" command:
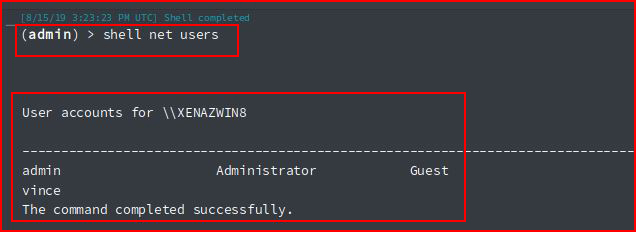
Just trying things here and there:
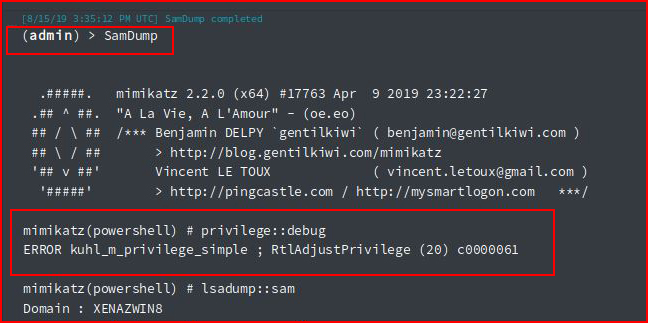
#NoJoy
And:
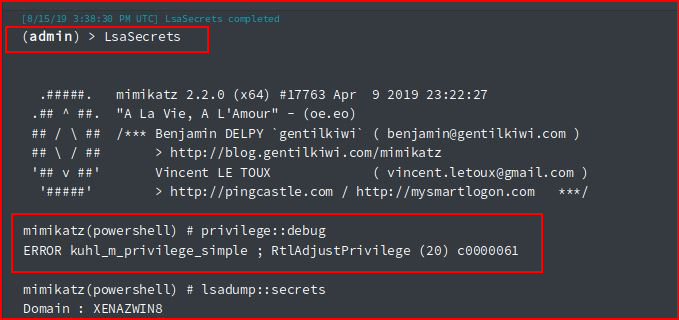
Also, #NoJoy
Something that maybe I don't understand but when we launch the Grunt, the Window stays open. If you close the window, the Grunt dies.
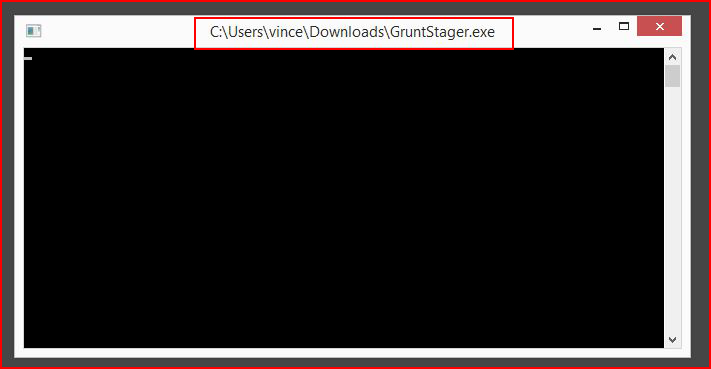
Moving along...
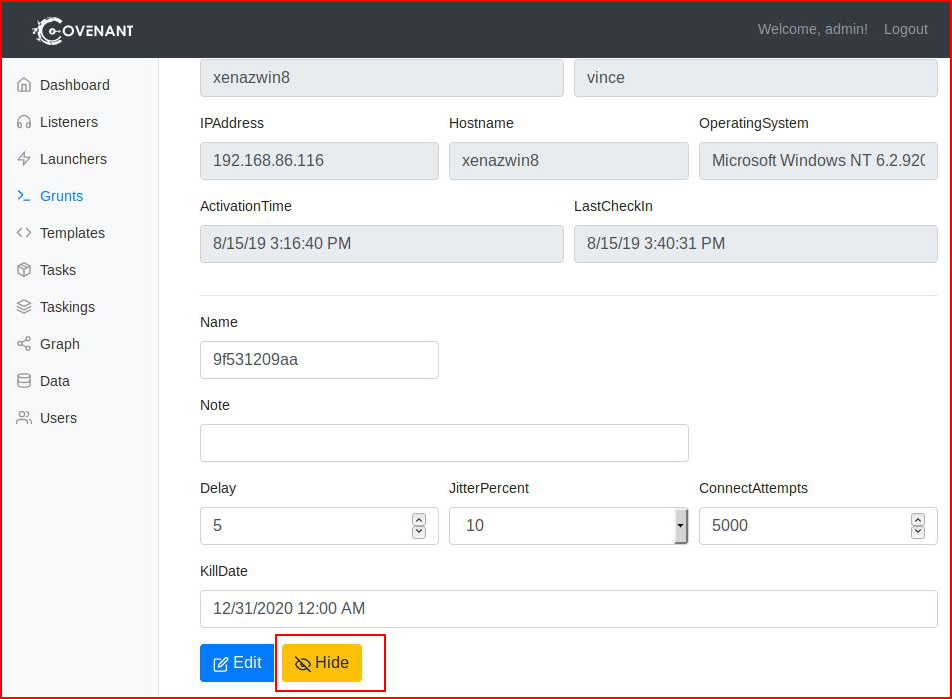
We have the option to "hide" the Grunt:
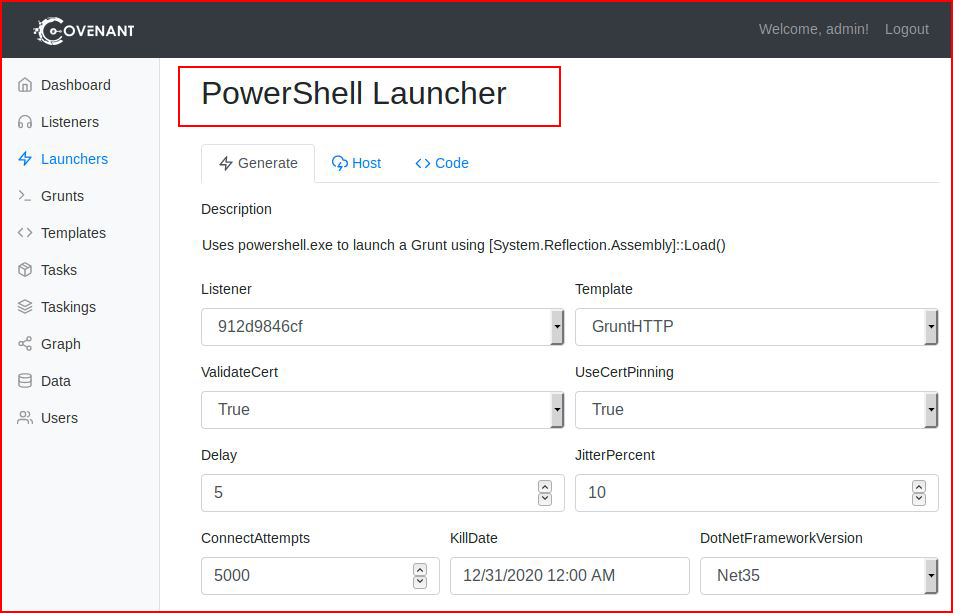
I wonder if we get anything different when going the PowerShell route:
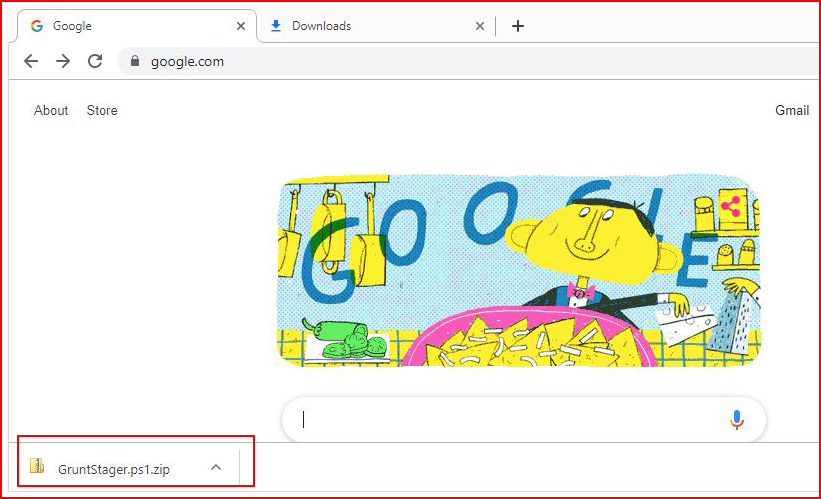
I download it:
I execute it:
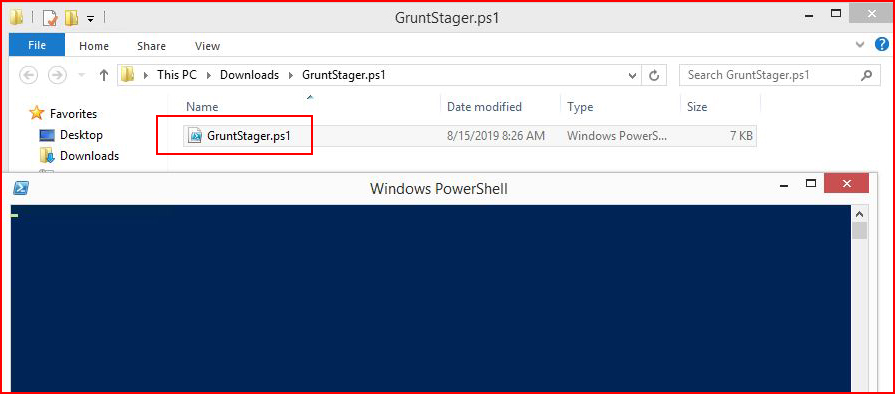
We see the Grunt in our console:
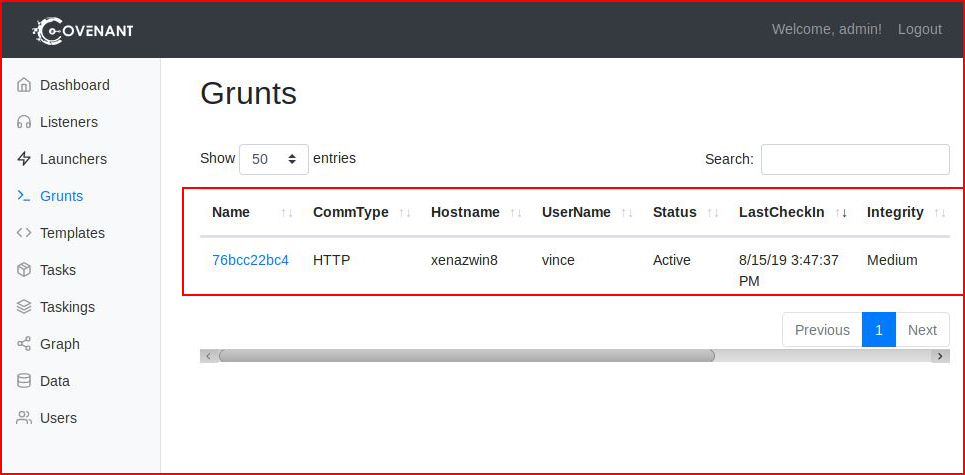
Essentially the same as the Binary including the window which stays open.
At this point, my attention span is waning and I want to see how antivirus reacts to our Grunts:
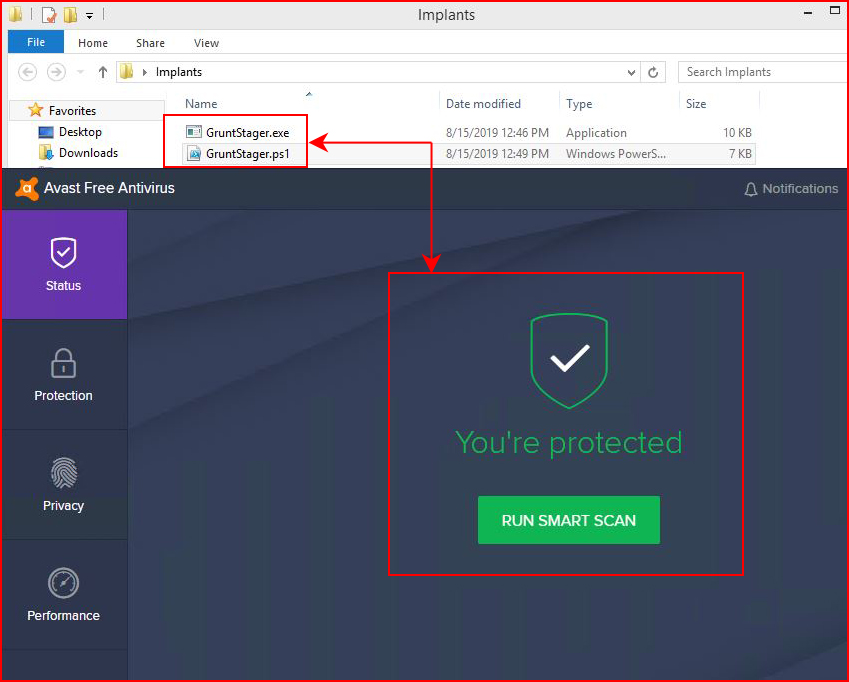
Nice work everyone! I should also point out that I've removed the gateway from the machine because I'd like to keep the antivirus mothership from getting a peek at these little guys.
One last test, we fire up the Grunt:
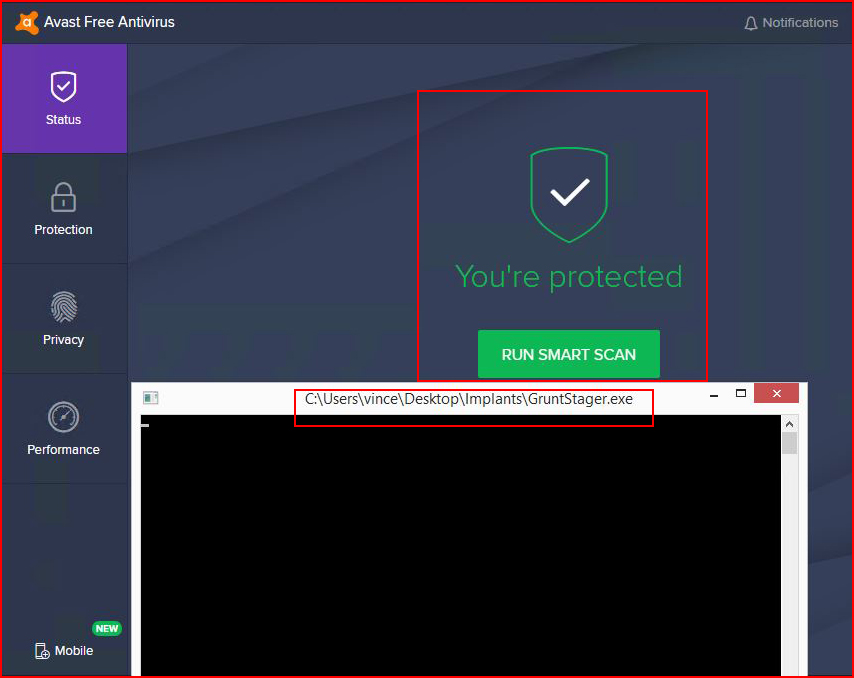
The antivirus is none the wiser and the Grunt appears in our console.
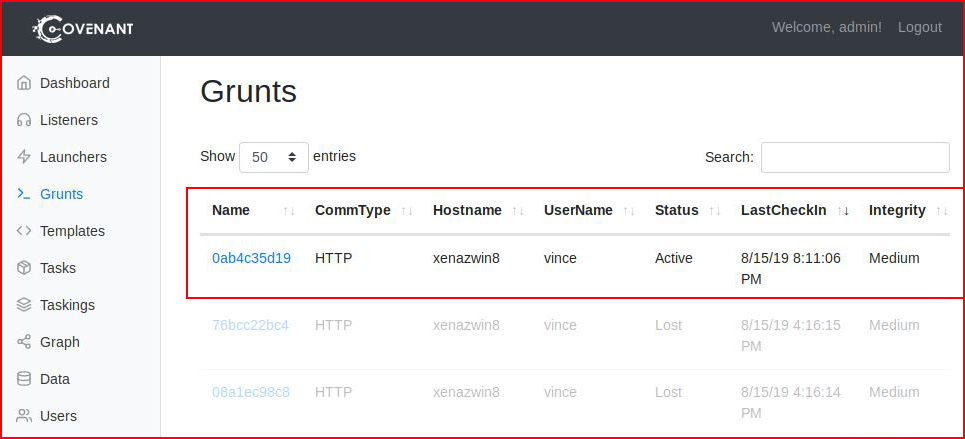
Pretty cool! I wish it did more that was useful to me. I should also point out that this UI is designed for a large monitor. I was originally working in a VM and I had to move out to a larger browser because the scaling is not great at 1440 x 900.