Man in the Middle Attack
I've been asked to give a talk on basic OpSec and I started compiling a small list of the essentials. Some of the items on my list have already been written and exist somewhere on this site while others are yet to be written. One of the questions that came up during the request for the OpSec talk involved public WiFi, the dangers, and how to protect yourself.
First, we have to understand how WiFi connections work at a basic level. The real danger comes from WiFi connections that are not secure, like those we find in an airport, a cafe, etc. When you turn on your device, the device will go through it's list of saved connections and it will toss out a request. Starbucks, you here? Oakland Airport, are you here?
Now suppose I have a device that is lurking, and waiting for such a request, when that request is made, my device answers. Instead of connecting directly to the Internet, you're now passing through my device and I become the Man in the Middle (MitM):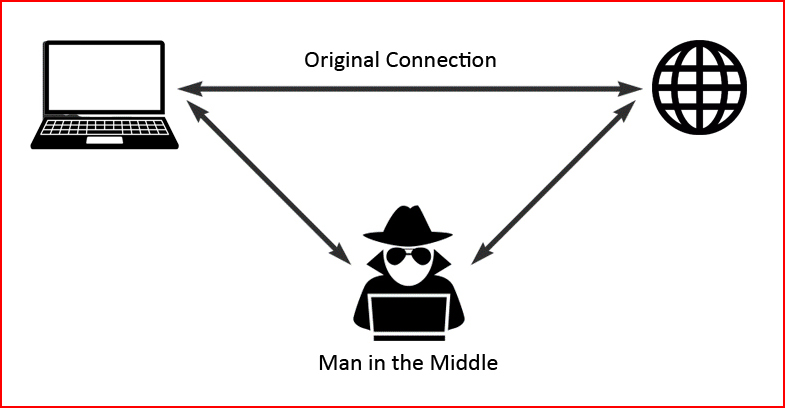
There are a number of ways to perform this type of attack but the simplest way is using a WiFi Pineapple which can be purchased for $99. Yes, for $99., most anyone without all that much skill can be a hacker criminal. That was intentional because not all hackers are criminals just like not all criminals are hackers. Seems lately the terms are used interchangeably and in reality, they are not interchangeable. Moving on...
I'm using the Pineapple because it illustrates the simplicity of this attack with this device and it should serve as a cautionary tale. At the very least, we all should pay a little more attention to our connections.
If you take the advice from the instructions for the Pineapple, when we power on the device, we boot up with the access point disabled. Once we're logged into the Pineapple, we move to the PineAp menu item. We need to make a few changes to get our system setup to hook a victim:
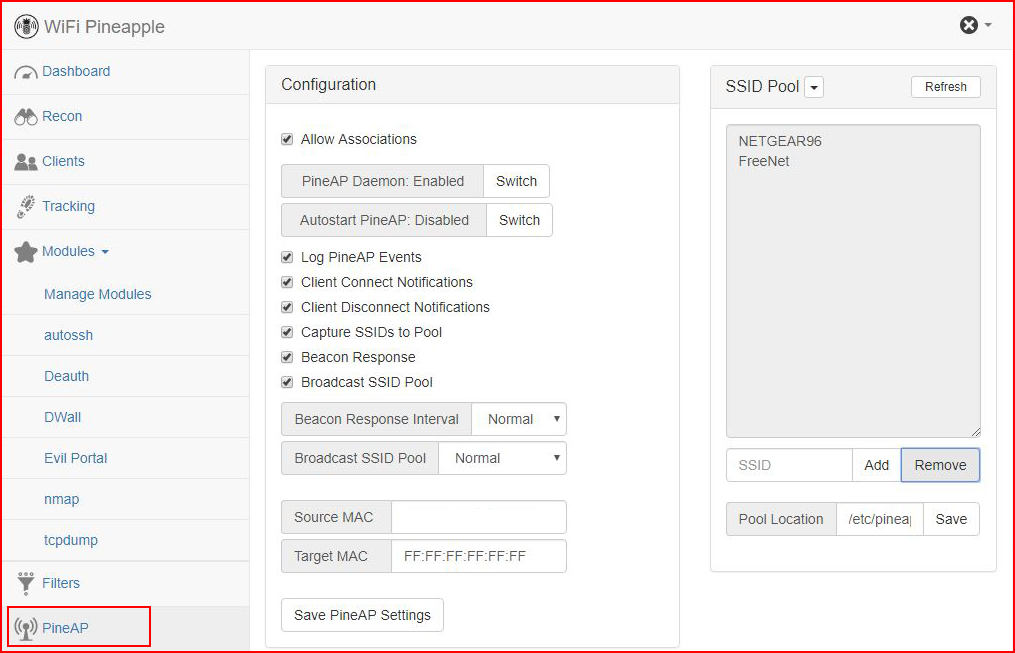
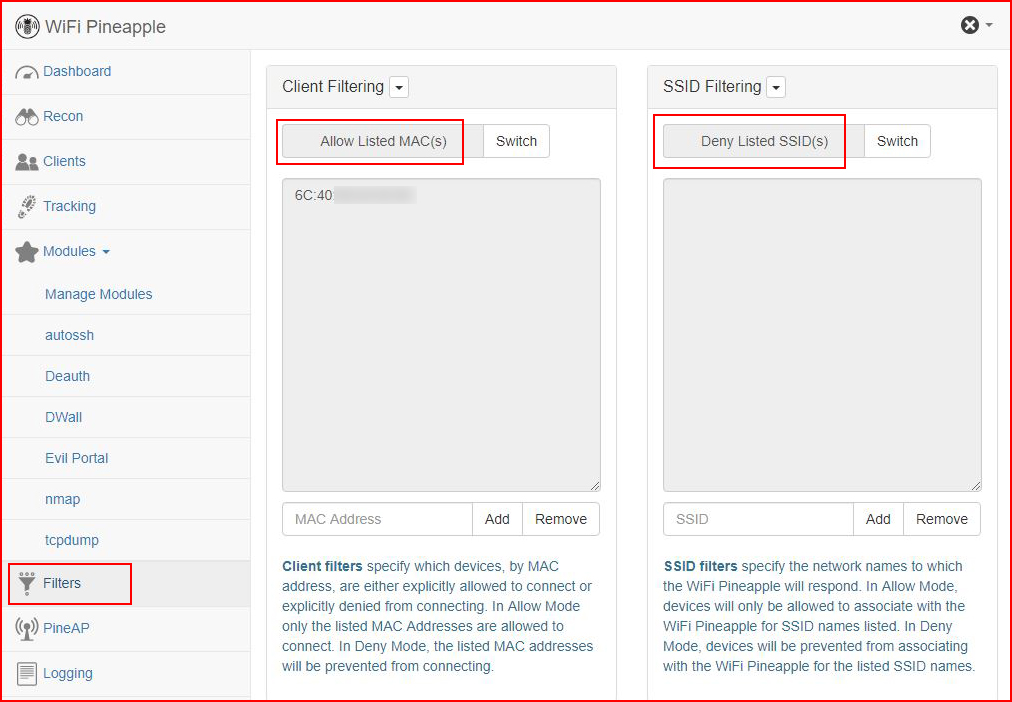
Because my goal is NOT to hook everyone in my vicinity, I've only added the Mac address for my system. And I'm pretty sure it's a crime to hook someone by mistake so pay close attention to how this is configured if you're setting this up with your own Pineapple:
Now that we've got the system configured, the quickest way to show the dangers of MitM is using the DWall module. Basically, this module is intercepting HTTP traffic. Because it's HTTP and not HTTPS, the traffic is unencrypted which allows us to see everything in plain text.
On my client laptop, I'm accessing a login form over HTTP. DWall captures the connection and as you can see below, the credentials are visible:
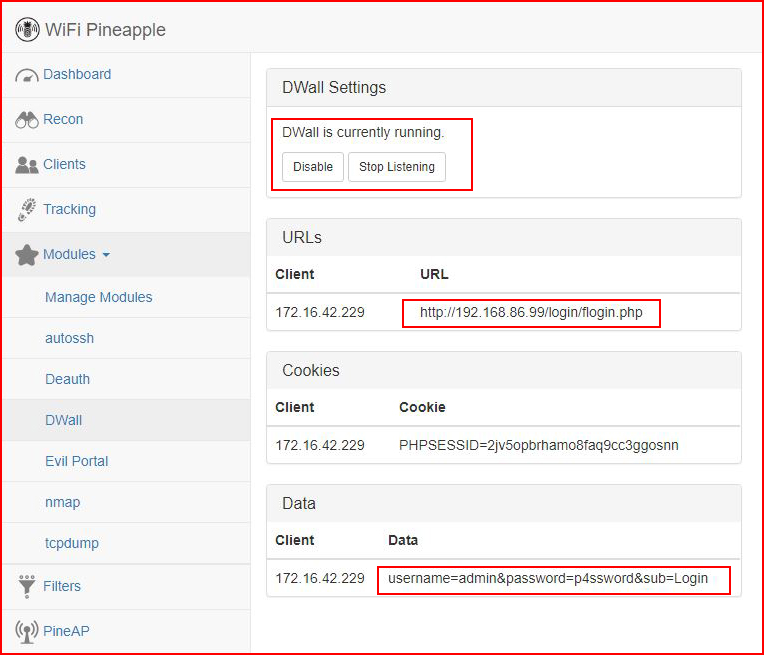
url: http://192.168.86.99/login/flogin.php
username: admin
password: p4ssword
Now that you understand what can be done, how do we protect ourselves from this type of attack?
While tedious, get in the habit of clearing out your WiFi connections. I'm guilty of this just like everyone else. I seem to be more disciplined with this task on my Mac but as I was writing this post, I saw a connection that I'm likely to never use again and I removed it. Once you're in the habit of cleaning up the connections, take note to WHAT you're connected to when you get connected. It's a really good sign you're a victim if you're sitting in Starbucks, and you're nowhere near the airport, but you're connected to airport's WiFi. Finally, a VPN in full tunnel mode is your friend because all of your traffic is routed to the Internet through an encrypted tunnel. Actually, that's not the last protection because I would be remiss if I didn't mention two factor authentication (2FA) but honestly, if you're on an HTTP connection, odds are pretty good that 2FA is not an option. But let's say for someone reason it was an option, someone could get your credentials but they would be without that second authentication method like a text message, an email, or a token you view on an app.