Pentesting 101: Passwords and Wordlists
The stock Kali Linux distribution contains a number of password and word lists. The most notable password list, RockYou, is from a breach that occurred in 2009. The biggest revelation to come from this breach was the frequency of the most basic passwords. The top five most used passwords in RockYou are:
123456
12345
123456789
password
iloveyou
In total, there were 32 million passwords in the RockYou breach but in the Kali version of this list, there are only 14 million passwords.
On a brand new installation of Kali Linux, you can find the RockYou password list under: /usr/share/wordlists/rockyou.txt.gz
To extract this list: gzip -d rockyou.txt.gz
When the file is finished extracting, we should end up with: rockyou.txt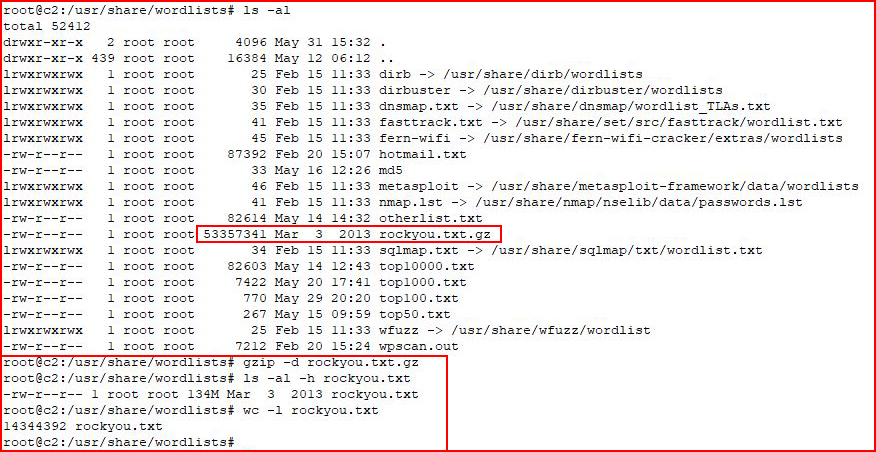
The total size of this file is 134MB -- of text. It's huge. As I mentioned previously, it contains over 14 million passwords. To use this file in its whole form is a last resort but we can easily create smaller lists using the head command. The RockYou list is in order of most used passwords and if we use head to extract the first 10, first 100, first 1000, or first 10000, we are literally getting the most popular in order.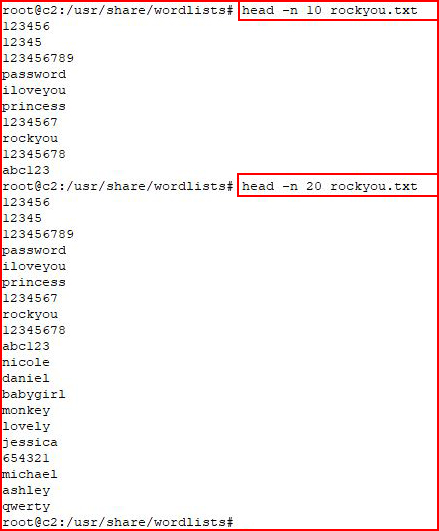
Depending upon the specific situation, the speed at which we process through our list will vary greatly. If we're using the entire RockYou list for cracking a sha512crypt hash using a basic Graphics Processing Unit (GPU), we could be waiting for a very long time. This is a situation where we might use the top 100, top 1000, or even top 10000 before we resort to the entire list. If the hash is MD5, the process will move along much faster and we might want to start with a larger list. I have multiple lists already generated and I decide which list to use based on the situation.
Word lists really aren't much different and we can find those under: /usr/share/wordlists/[SOME DIRECTORY]
The two most common locations:
/usr/share/wordlists/dirb
/usr/share/wordlists/dirbuster
There are some pretty solid lists in both of these directories and I like to combine them into one larger list. Again, like the RockYou list, bigger is not necessarily better but if I'm looking for the sledgehammer, I'll go for the combined list.
Up until now, I've been talking like password lists and word lists are separate entities but they are essentially the same -- they are lists. For the sake of convenience, and not necessarily betterment, we are using these stock lists. Taking a more targeted approach might be a better option.
Indulge me for a moment as I go off on a tangent --
IBM's first CEO was Thomas J. Watson. If you look throughout IBM, you will see the name Watson appear in a number of forms. A Google search for "IBM Watson" brings up their "question-answering computer system". I first learned of the name Watson from ns.watson.ibm.com which is an IBM name server I used for many years because it was very reliable -- that is until it stopped taking public DNS requests.
The point being that it's not uncommon to see words and names recycled throughout a business. Server names, directory names, and passwords, could all be names gleaned from a company website. With the name Watson being so prevalent throughout the IBM world, how many passwords do you think had some variation of Watson?
Back on point --
At the very least, if I'm fuzzing or performing a brute force attack, among the lists I'm using is one that I've generated from the company's public facing sites uing Cewl: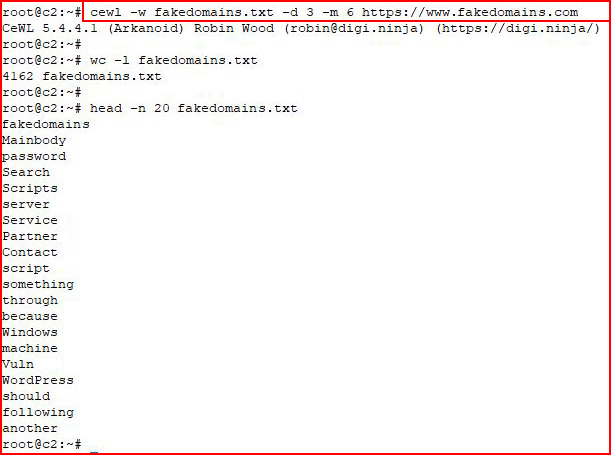
cewl -w fakedomains.txt -d 3 -m 6 https://www.fakedomains.com
-w = output file
-d = depth
-m = minimum word length
Using wc, we created a list with 4162 words. When we look at the first 20, it looks like a word list! We can mutate this list in a number of ways but for now, let's stick to the basics. When I grep through my largest word list and RockYou, I'm already finding words in our targeted list that do not appear in either of the larger lists. 4162 goes a lot faster than 14 million!